Despite espousing a common, layered approach to security these days, most enterprise security suites have taken markedly divergent paths to essentially arrive at the same location. For example, some solutions started out as intrusion detection and protection systems (IDPS) and gradually added on vulnerability detection and security information and event management (SIEM). Others began as penetration testing (pentesting) tools—or have built their offerings around pen testing—and similarly expanded their solutions to include other security mechanisms like endpoint protection and anomaly detection. Core Security and Rapid7 are two such enterprise security suites; let's see how they stack up in this comparison.
Organizations taking a vigilant stance against cyber attackers will often institute regular pentesting routines to test the security of their systems, applications, and infrastructures/environments. Pentesting allows firms to discover and exploit existing vulnerabilities for the purposes of identifying at-risk routes, failing information security policy controls, and previously unknown security flaws.
Generally speaking, Core Security and Rapid7's offerings revolve around two core competencies: pentesting and vulnerability assessment/management. Both firms have built comprehensive security suites around these competencies, to include capabilities such as access management and security information and event management (SIEM), among others.
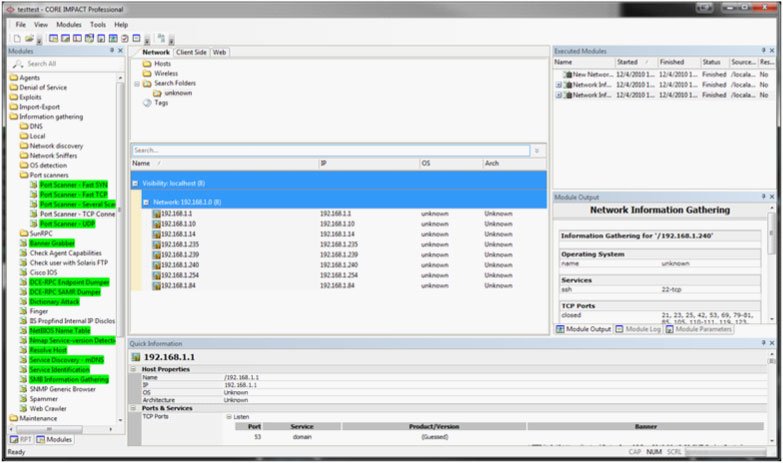
Core Security
Core Security was founded in Argentina two decades ago as a provider of pentesting and vulnerability assessment services. Its flagship pentesting product, Core Impact, has become an industry leading platform for vulnerability testing. Additionally, its Core Vulnerability Insight allows enterprises to unify, regulate, and prioritize vulnerability management initiatives.
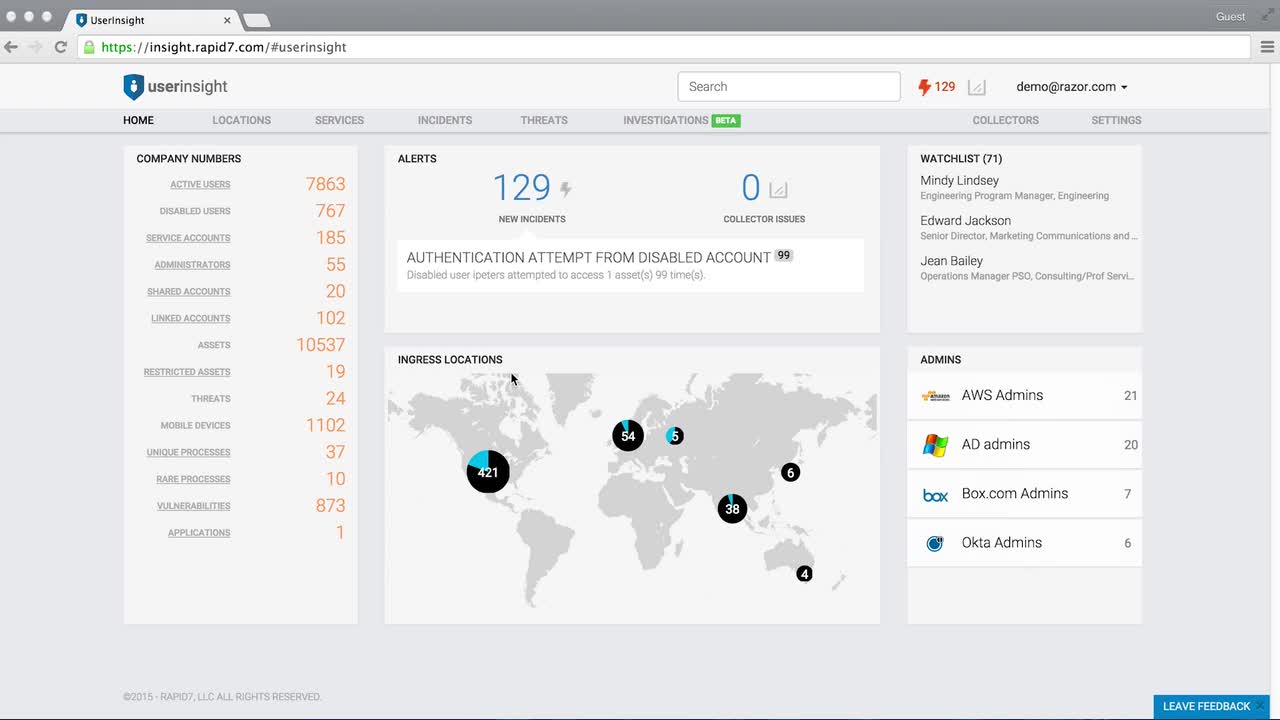
Rapid7
You've perhaps heard of the open source Metasploit Framework—purportedly the the world’s leading pentesting tool. Released in 2004, the project features an advanced platform for developing, testing, and using exploit code. Rapid7 acquired Metasploit back in 2009 and is the project's current owner. The project finds itself integrated into many of the company's solutions, including the Nexpose vulnerability management platform and the InsightIDR incident detection and response/SIEM platform, among others.
Side-by-Side Scoring: Core Security vs. Rapid7
1. Capability Set
Both Core Impact and Rapid 7 are powerful tools for exploitation and vulnerability assessment, but Rapid7's Nexpose supports the complete vulnerability management lifecycle management, from discovery to mitigation—on top of the popular Metasploit for vulnerability exploitation. That said, Core Security does offer extended capabilities through other offerings like Access Insight and the Access Assurance Suite for user identity and access management.
2. Ease of Use
Rapid7's clean web interface—coupled with the ubiquity of Metasploit—gives Core Security the win in this category. In contrast, Core Security's dated interface is less intuitive and certainly not as pleasant to look at as Rapid7's.
3. Community Support
Both feature several community-based support options, but Rapid7's resources are certainly more numerous and varied—in large part no doubt to the popularity of its open source Metasploit framework. Additionally, Core Security's Force.com-based community portal pales in comparison to Rapid7's robust community site.
4. Release Rate
Both platforms have seen regular releases over the years, though Rapid7's open source Metasploit Framework is the most actively maintained. Additionally, Core Security's rebranding and product renaming efforts over the years makes it difficult to track product releases.
5. Pricing and Support
A monitoring system won't troubleshoot a configuration error. A configuration test script will.
The Metasploit Framework remains free and open source, despite being acquired by Rapid7. Express versions of Nexpose and Metasploit start at $2,000 and $5,000, respectively, with a full-featured pro edition starting at $15,000 per year. In contrast, Core Impact costs almost twice as much—upwards of $30,000. Both vendors offer the standard range of support options.
6. API and Extensibility
Rapid7's Nexpose features an XML-based API while its Metasploit Framework offers a REST API for integrating custom applications with its services. In contrast, Core Security does not offer an API for any of its products.
7. 3rd Party Integrations
Core Impact integrates with leading vulnerability scanners like QualysGuard, NESSUS, and even Rapid7's own Metasploit. Rapid7 is also strong in this category, featuring integrations with leading vendors/platforms like AWS, ForeScout, Jenkins, Okta, VMware, and Splunk, among others.
8. Companies that Use It
Core Security is in use by global enterprises including EMC, Experian, Mastercard, and Credit Suisse, to name a few. Similarly, Rapid7's customer list is equally impressive: Adobe, Amazon.com, Ingram Micro, Johnson & Johnson, and Microsoft, among others.
9. Learning Curve
For most pen testers, getting up-to-speed with both platforms should be trivial; however, Rapid7's contemporary web interface may be more intuitive and accessible to novices.
10. Security rating
Both companies perform well when it comes to managing digital resilience and cyber risk, as quantified by their security rating scores. No major website perimeter and email security risks exist. CoreSecurity scores 817 and Rapid7 scores 703.
Scoreboard and Summary
Pen testing is a critical component of enterprise security—without it, firms can only assume that their security controls are working as expected. Borrowing from Core Security's tagline, pen testing allows you to "think like an attacker" and subject your infrastructure to simulated cyber attacks. Both Core Security and Rapid7 are competent pen testing suites that provide comprehensive vulnerability exploitation and assessment services. However, Rapid7's more attractive price point and popular open source Metasploit Framework certainly give it an advantage over Core Security.




