Tuesday July 12th is online retail giant Amazon’s self-styled “Prime Day,” and the potential deals mean a surge in online shopping. Designing systems and applications to handle the amount of traffic a site like Amazon sees day to day, much less during promotions like Prime Day, can be difficult in and of itself. Throw in the complexity of cybersecurity and it becomes clear why so many online retailers have trouble keeping up. Amazon itself has relatively good security, but what exactly does that mean for customers? We’ll look at what measures Amazon has in place, what they mean, and a few simple steps to tighten security even further.
SSL - Keeps Traffic Private Between Customers and the Website
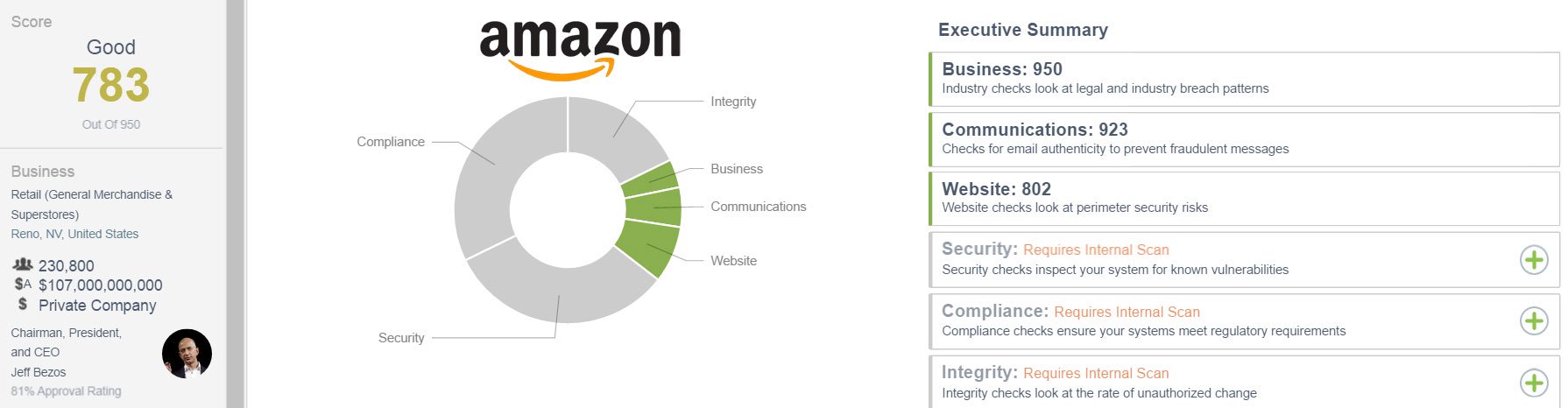
The first key to good security is making sure information passing between the customer and the website can’t be read or taken by a third party. Secure Sockets Layer (SSL) is a mechanism that encrypts web traffic, meaning that only those in possession of a key (you and the website) can read any of the data.
This prevents someone from “sniffing” your traffic and reading in plain text exactly what you’re doing. Have to log in? If it’s not done over an SSL connection, your username and password are sent in plain text to the website. Anyone who wants to can intercept that traffic and read its contents. With SSL, the traffic can still be intercepted, but because it’s encrypted, third parties only see gibberish.
UpGuard judges SSL based on three categories:
- Is it encrypted? This seems simple, it’s either on or off, right? Not exactly. SSL can be implemented “in part” by having only certain websites behind SSL connections. This is poor practice and can lead to a man in the middle attack, as customers are passed from non-encrypted lanes to encrypted lanes. Encryption should be enabled across the board for the entire website.
- How well is it encrypted? Different strengths of encryption, different cipher methods and different needs mean that every SSL configuration is unique. We look at how well the website encrypts data. SSL doesn’t mean anything if it relies on an old, vulnerable cipher suite. Websites should use the latest and greatest to keep their customers safe from the newest threats. Amazon does a great job with this.

- How strictly is it enforced? We check to see if the website allows non-SSL connections, or if it forces you back onto an SSL link. For example, if someone makes a bookmark and types in http:// instead of https://, they could inadvertently bypass SSL altogether. Remember: SSL should always be enforced on all parts of the website. Despite having a good SSL configuration, this is one piece Amazon could improve.
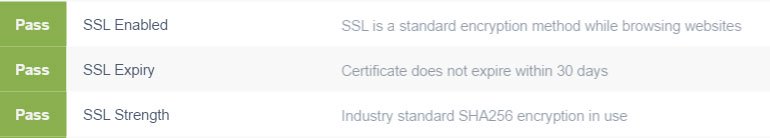
Header Information - Obscures the Website Details From Attackers
It’s always been the practice for web server software to advertise itself to clients. It’s always been the job of sysadmins to disable that. There are very, very few legitimate reasons a visitor to a website needs to know what kind or version of web server the site runs. But obviously there are many reasons why someone looking to attack a site would want that information. Despite often being the default configuration, these headers should always be obscured to prevent hackers from quickly narrowing down the attack routes. Amazon has all of their headers obscured, but many sites do not.
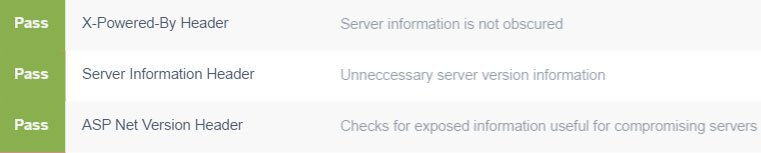
Secure Cookies - Prevents Client Malware From Impersonating the Customera
A cookie is a file on your computer that a website stores to track various things about you. These could be user preferences, location and most importantly, your credentials. If you click on a website and don’t have to type in your username and password every time, it’s probably because a cookie is stored on your system that the website reads that says “hey, remember me?” Very convenient.
There’s just one problem: what if it isn’t you using the cookie to say “hey, remember me?” Malware utilize what are called cross-site scripting (XSS) attacks to exploit cookie vulnerabilities and impersonate customers. There’s good news and bad news: methods exist to help prevent these attacks, and Amazon doesn’t use them.
- HttpOnly - This configuration setting prevents scripts from accessing the cookie. When malware queries the cookie, it returns a blank (instead of say, your login details,) which is then sent to the hacker’s website. If this configuration setting is not set, well, it sends the login details. This should be a no-brainer, as it’s literally a flip of the switch to implement.
- Secure - This flag ensures that cookies are only passed across SSL encrypted connections. Like data that you enter manually, cookies can be read in transit if they are not encrypted in an SSL tunnel. Since cookies often have the same sensitive information in them that people are worried about typing in, they should be protected just as carefully. Failure to use this flag means that cookies will be allowed on unencrypted connections, at which point they are vulnerable to snooping.
All modern browsers can handle these cookies flags, so there’s no reason to leave these settings as is. Even if a legacy browser receives a request for an HttpOnly cookie, it will just get a regular cookie instead. But better just the people using unsupported browsers than everyone. The secure flag requires all websites to be on SSL, which is optimal, but if a site uses an old configuration where some pages are still unencrypted, they likely have to leave the secure flag off so cookies will still function for those pages.
Email and DNS Protection - Verifies That Emails and Web Addresses are Real
You’ve probably gotten emails from Amazon: promotions, offers, order details, etc. You’ve also probably gotten emails from people claiming to be Amazon, looking to steal your credentials. These are called phishing emails and successfully trick people into giving up their account details by pretending to be a legitimate website or sender. So how can you tell the difference?
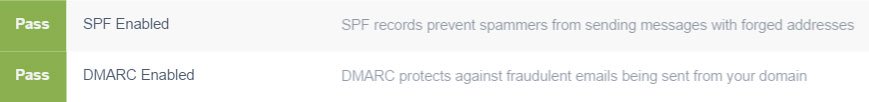
Email protocols such as SPF, DKIM and DMARC exist for just this reason. These mechanisms put information on the internet that say “mail from Amazon will ONLY come from these servers” and a list of valid source servers. Email purportedly from Amazon but originating from another mail server will be caught immediately for failing the SPF/DMARC check and be rejected as spam. All of this happens behind the scenes, with the mail servers doing all of the work for you. But if a company doesn’t use these mechanisms, there’s no way for mail servers to tell if the mail is real or fake, and so it gets passed along to a human, whose judgment is somewhat less than infallible. Amazon uses these mechanisms, a good sign for a company that sends so many emails.
DNSSEC - When you type amazon.com into your browser, what happens? Your request goes to the .com root domain name server, who says “oh, amazon.com is at the unique address of 54.239.25.200” and sends your computer on its way. But when a successful DNS hack occurs, instead of getting the legitimate address of the website you want, you get an address of the hacker’s choice instead, usually a dummy page to collect credentials. DNSSEC is a mechanism designed to prevent this by signing address translation responses with an encryption key. Unsigned responses are bogus and get trashed, while signed responses pass the test and continue to the customer.

Amazon doesn’t use DNSSEC, as it is relatively new and somewhat difficult to implement. However, as online communications require more stability and integrity, DNSSEC will be a standard business want to meet to ensure customer safety.
CEO and Company Rating - Gauges the Risk of Insider Breach
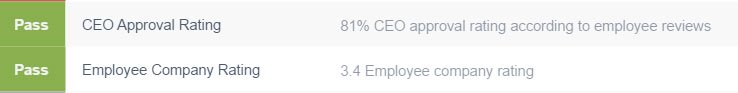
Snagging your data in transit is only one way attackers can access it. Once your information’s on Amazon’s servers, it can also be accessed through a data breach, similar to the massive one LinkedIn experienced recently. A common form of data breach is an insider breach, where someone who already has access to the data, misuses it. We found that there is some correlation between employee happiness and cybersecurity. That’s why UpGuard incorporates CEO approval and company rating from Glassdoor into our security assessment. Disgruntled employees, or employees at odds with executive management and/or business direction are far more likely to either perpetuate an inside breach, or allow a breach to occur through negligence. Amazon does well on both, lowering their risk of an insider incident.
Cybersecurity can be difficult and complex, but only with data integrity and customer confidence in the medium can online business be successful. Prime Day might seem like a good stunt now, but if everyone who signed up for it had their data compromised, it would be a whole different story. Amazon has decent security, but could step it up in just a few more areas. Check out any of your favorite websites with UpGuard’s free external risk grader to see how they stack up against Amazon and others.




