The Medibank hack began with the theft of credentials belonging to an individual with privileged access to Medibank’s internal systems. These credentials were sold and purchased on the dark web by an unconfirmed buyer who used them to gain access to Medibank’s internal system.
Once inside, the threat actor identified the location of a customer database and then used the stolen privileged credentials to write a script to automate the customer data exfiltration process - a similar data theft mechanism was used in the Optus data breach.
This stolen data was placed into a zip file and extracted through two established backdoors. Medibank’s security team allegedly detected suspicious activity at this point and shut down both back doors, but not before 200GB worth of customer data was stolen,
9.7 million Medibank customers were impacted by the breach. Compromised records include:
- Names
- Birth dates
- Passport numbers
- Information on medicare claims
News of the successful attack was published on the dark web blog associated with a ransomware gang tracked as BlogXX (a cybercriminal group believed to be a reformation of the notorious ransomware gange REVil). The hackers posted a sample of the stolen data to prove the legitimacy of their claims and demanded Medibank pay a US$10m ransom to prevent the entire database from being freely published on the dark web.
To force Medibank to pay the ransom, the cybercriminal group will continue posting segments of the stolen database until the ransom is paid completely.

Medibank CEO, David Koczkar, announced that the company has refused to pay the ransom since cybercriminals can never be trusted to follow through with their promises.
“...paying could have the opposite effect and encourage the criminal to directly extort our customers and there is a strong chance that paying puts more people in harm’s way by making Australia a bigger target.”
- Medibank CEO David Koczkar
For a more technical explanation of the Medibank hack, see this post.
Corporate Credential Theft: The Reason the Medibank Breach was Possible
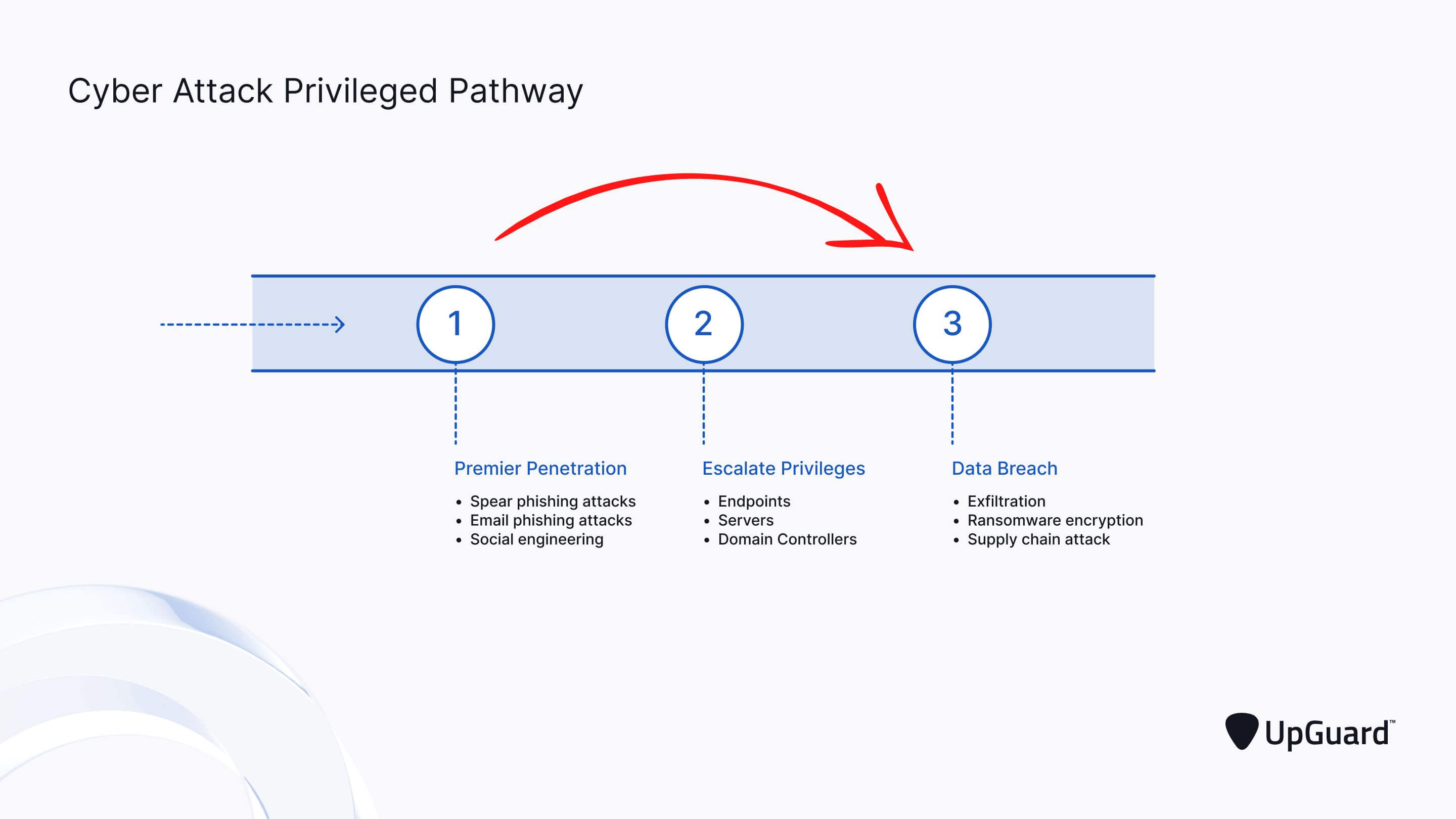
The Medibank data breach was made possible by the theft of internal credentials believed to belong to an individual with privileged system access. Internal credential theft is one of the first objectives of almost every cyberattack. It hasn’t yet been confirmed how the Medibank credentials were stolen, but the most common method of stealing account information is through a tactic known as Phishing - a style of cyberattack where hackers send fraudulent emails with malicious links leading to credential-stealing websites.
When hackers steal “disappointing” account credentials with limited user permissions, they use them to get inside a network and then clandestinely examine every region of it, searching for higher privilege credentials to steal - a process known as ‘lateral movement.’
By instantly getting their hands on privileged account details, the Medibank hackers bypassed the arduous lateral movement stage of the attack and skipped straight to the final data breach stage. This compressed the cyberattack pathway, allowing the breach to be completed much faster.

See how your organization's security posture compares to Medibank's.
View Medibank's security report.
How Could the Medibank Data Breach Have Been Prevented?
Mapping all of the exploits leading to the Medibank bank breach to their corresponding security controls reveals four initiatives that could have prevented the incident from happening.
1. Cyber Threat Awareness Training
Cyber threat awareness training teaches employees how to recognize and correctly respond to corporate credential theft attempts from phishing and social engineering attacks.
We don’t yet know how the Medicare credentials that facilitated the breach were stolen, but by teaching your employees how to recognize a phishing attack, you’ll protect your business from the most common method of credential theft.
Learn more about phishing attacks >
2. Implement the Principle of Least Privilege (POLP)
The principle of least privilege is an account security policy that limits each employee’s account access to the minimum level required to perform daily tasks. This should be a standard security policy for all Australian businesses since excessive privileges present a significant security risk.
By reducing the chances of hackers bypassing the privilege escalation phase of an attack, a POLP policy forces the entire attack to take longer, which increases the chances of vigilant security teams detecting and intercepting the breach attempt. The Medibank event proved that it’s possible to disrupt a cyberattack while it's still unfolding, reducing its potential damages.
According to Medibank, its systems were not encrypted during the attack, which is odd considering the attackers were likely a ransomware gang. A possible reason for this is that by promptly shutting down the backdoors established by the cyber criminals to facilitate the breach, Medibank disrupted the attack before it reached its final encryption phase.
Learn more about the Principle of Least Privilege >
3. Segment your Network
A network segmentation strategy separates a network into different segments or “zones” to make sensitive data more difficult to locate and access. In case a sensitive zone is located, connection requests to this region should be passed through a jump server (a hardened system used to manage connection requests to sensitive zones) to further reduce the potential for compromise.
Learn more about network segmentation best practices >
4. Use Multi-Factor Authentication (MFA)
It hasn’t yet been confirmed whether multi-factor authentication was bypassed during the Medibank hack. MFA is one of the most effective measures against account compromise attempts.
According to Microsoft, Multi-Factor Authentication could prevent up to 99.9% of account compromise attacks.
All employee accounts, including privileged access accounts, should be protected with MFA - ideally, adaptive MFA since it’s the hardest to bypass
When a cybercriminal attempts to connect to a network with an account protected with MFA, they’ll be unable to complete the login process unless they also pass a series of user identity verification steps. These additional verification requirements are difficult to bypass and could be enough to stop an attack from progressing.
Note: Even though bypassing MFA is difficult, it’s still possible. If you’re implementing MFA, make sure you’re aware of these common bypass methods.

How UpGuard can Help
Every organisation is at risk of corporate credential compromise, but not every organisation will suffer the same devastating outcome as Medicare when these events occur. UpGuard has developed a data leak detection solution to help organisations rapidly detect sensitive credential dumps on popular dark ransomware blogs. Rapid detection means that compromised accounts can be secured much faster, decreasing the chances of follow-up cyberattacks targeting impacted businesses.

Each detected leak is manually reviewed by cybersecurity experts to eliminate false positives and support the efficiency of data leak remediation efforts.





