Many organizations use virtual private networks (VPNs) to extend secure access to remote employees. A VPN creates a secure connection between two networks over the public internet, creating a level of online privacy for remote workers. A VPN internet connection will route your web traffic through an encrypted tunnel (even when using public wi-fi), protecting business sensitive data from interception. VPNs require authentication, which can help maintain your network security.
VPNs and cybersecurity concerns
When using a VPN, the user's web traffic and queries are protected through encryption. Your internet service provider (ISP) cannot read the traffic, nor can an adversary-in-the-middle (also called a man-in-the-middle) intercept it. There are a variety of secure VPN protocols that provide authentication, tunneling, and encryption.
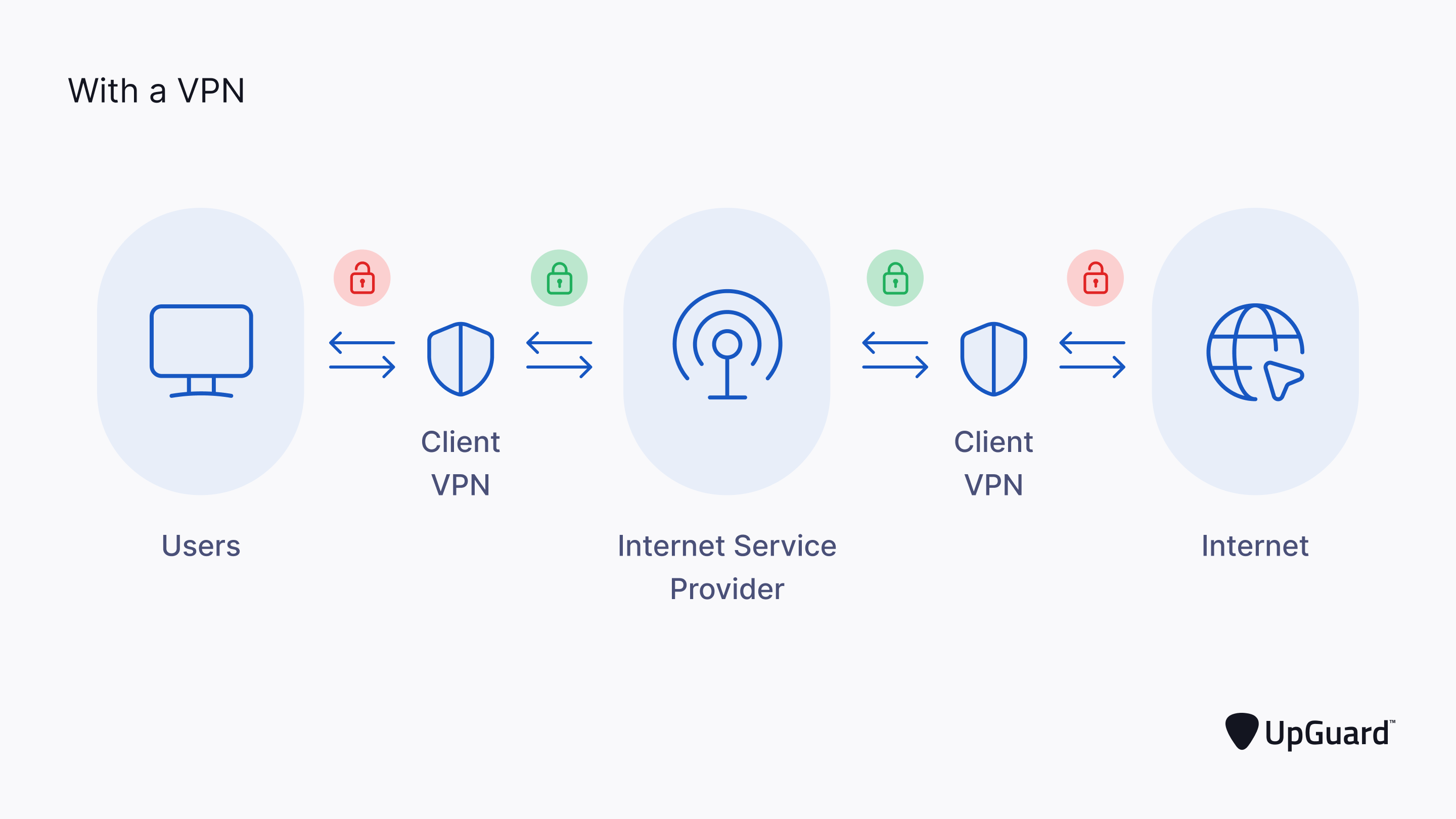
When implementing a third-party VPN service provider, you must account for security risks associated with the VPN solution. VPNs are a prime attack vector for cybercriminals because they can typically leverage access into your entire network through the VPN tunnel.
When selecting a VPN provider, perform due diligence to guarantee that you use a reputable third-party provider. Some free VPN services have greater risk exposure. If necessary, conduct a risk analysis to evaluate your potential exposure with this provider. Evaluate their update cadence and whether the VPN client has recently experienced any zero-day VPN vulnerabilities.
Your VPN provider can log some information, such as your IP address, so you should be aware of their data collection and logging policies. If the VPN provider experiences an attack or data breach, your organization's sensitive information and employees' personal data could be compromised or revealed.
While a VPN connection ensures that internet traffic is encrypted and therefore protected from your ISP, the VPN does not protect against social engineering attacks that hackers use to compromise user credentials. If employees who use the organization's VPN become victims to phishing attacks, then the attacker could leverage the user's credentials for unauthorized use of the organization's VPN. Likewise, a VPN cannot protect against a weak password so users should create secure passwords and implement multi-factor authentication for any device or account that can access sensitive data.
VPNs do not protect against viruses or malware. Data traveling through the VPN will be encrypted, but malicious data can still compromise the account. Viruses like remote access trojans can still transmit through an encrypted VPN server, so users should practice caution when downloading files. Curating a strong security mindset at the company can help prevent workers from inadvertently introducing a ransomware infection or malware infection.
Remain vigilant with your VPN service provider through continuous monitoring and risk assessments. Security features and security protocols should be central in your evaluation of VPN security risks.
How UpGuard can help
With UpGuard, you can perform continuous monitoring for your external attack surface with BreachSight and for your third-party vendor ecosystem with Vendor Risk. UpGuard scanning includes techniques that use standardized and publicly accessible network-based protocols to query hosts across a variety of categories. UpGuard's scanning process identifies the following VPN ports that should be reviewed:
- 'IKE VPN' port open
- 'OpenVPN' port open
- 'NetMobility' port open
- 'PPTP' port open
Additionally, the Detected Products feature identifies software products in use among your assets, including VPN services:
- FortiOS SSL VPN interface has been detected
- Ivanti Connect Secure VPN has been detected
These detection capabilities are especially beneficial for software with critical vulnerabilities, such as Fortigate CVE-2023-27997 and Ivanti Connect Secure CVE-2024-21887. Identifying software in use enables you to secure vulnerabilities quickly to prevent data leaks.
Recommendations for managing VPN use
Using a VPN for encrypted network traffic is a great security measure. To augment that, you can also use the following recommendations to improve security around your organization's use of VPNs:
- Adopt a zero-trust policy for all access outside your network.
- Implement access control using the principle of least privilege for user permissions and require individual authentication that includes a multi-factor confirmation.
- Recommend VPN use for all remote work activities to ensure protected online activity.
- Log high-level session information that can be used for auditing purposes to ensure safe and approved network access. Logging information is risky, so consider the costs associated with even high-level session information that an attacker could access.
- Run regular risk audits and assessments to confirm that the third-party service provider meets your security compliance needs.
- Require a strong encryption protocol and test the VPN's IP and DNS leak protection.
- Consider using a firewall-based VPN software that pairs a firewall's endpoint traffic restriction with a VPN's encryption functionality.




