A Vendor Risk Assessment (also referred to as a third-party risk assessment) is a critical component of a Vendor Risk Management program. As such, the overall impact of your VRM efforts hangs on the efficiency of your vendor risk assessment workflow.
This post outlines a framework for implementing a streamlined vendor risk assessment process to prevent potential data breach-causing third-party security risks from falling through the cracks.
Learn how UpGuard streamlines Vendor Risk Management >
What is a Vendor Risk Assessment?
A Vendor Risk Assessment is a comprehensive evaluation of a vendor’s security posture and its potential impact on your organization.
A component of Vendor Risk Management - the branch of cybersecurity focused on detecting and mitigating vendor-related security risks - risk assessments consolidate information about a vendor’s cybersecurity posture from multiple sources to form a comprehensive risk exposure profile.
The act of sending a vendor a risk assessment constitutes just a single stage in a complete vendor risk assessment workflow. Technically, the risk assessment process officially begins at the due diligence stage, where high-level cybersecurity performance data is collected to form the basis of an eventual risk assessment.

What's the difference between a vendor risk assessment and a security questionnaire?
A vendor risk assessment is a comprehensive evaluation of a vendor’s cybersecurity performance. Security questionnaires are a component of risk assessments. They are used to gather deeper insights into specific risk categories, such as:
- Data breach risks - Vulnerabilities associated with service provider solutions
- Regulatory compliance risks - Events causing violations of regulatory standards, such as HIPAA and GDPR
- Information security risks - Threats related to unauthorized access to information security systems.
- Supply chain risks - Third-party vendor risks increasing the potential impacts of supply chain cyber attacks
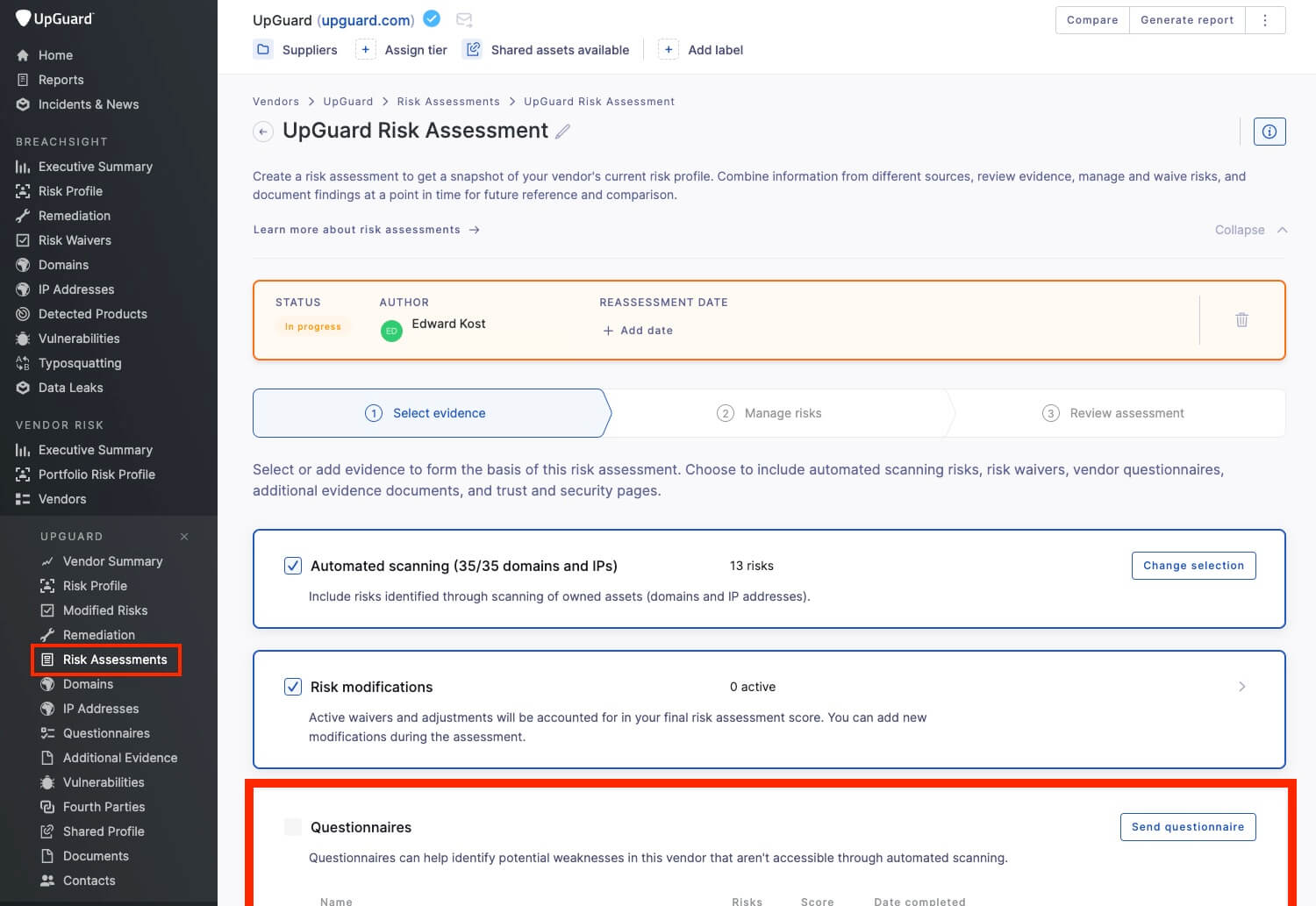
A vendor risk assessment questionnaire is a security questionnaire supporting a broader vendor risk assessment.
5-Step Guide: Designing a Vendor Risk Assessment Process
This framework is modeled against a risk assessment workflow proven to increase VRM process efficiencies on the UpGuard platform. For an overview of this vendor risk assessment lifecycle, watch this video:
Step 1. Establish a due diligence workflow
The first stage of your vendor risk assessment process should prepare the groundwork for an official risk assessment. This is the due diligence phase of a Vendor Risk Management workflow, the process of evaluating the cybersecurity risks of prospective vendors before business relationships are established.
The vendor lifecycle should always start with a due diligence process.
Due diligence isn’t a formal vendor risk assessment. Think of it as a filter for prospective vendors where only those meeting your specified inherent risk tolerance criteria are passed through to onboarding and official risk assessment protocols.
Vendor due diligence is considered an “evidence gathering” process. Evidence about a vendor’s security performance is collected from multiple sources to create a picture of their inherent risk exposure.
An excellent time-saving trick is to reference a vendor’s Trust and Security page, a page on their website showcasing all of their cybersecurity initiatives. These pages could be a treasure trove of helpful information outlining the vendor’s efforts in specific areas of information security and compliance.
The following information could be included in a company’s Trust and Security page:
- How the business is meeting regulatory requirements (could include specific security control strategies)
- How the business’s data security and data privacy initiatives ensure its business operations and sensitive data are protected from security breaches.
- Alignment with cyber frameworks and standards, such as SOC 2 and NIST CSF version 2.
- Environmental, Social and Governance (ESG) frameworks and policies
- Initiatives mitigating risks impacting SLAs of third-party relationships (events that could result in regulatory violations) across associated risk categories, including financial risk, reputational risk, operational risk, natural disasters, and business continuity.
- A list of the company’s security and compliance certifications.
Here’s an example of a Trust page by Google.
Depending on how comprehensive a vendor’s Trust and Security page is, and whether they're considered a low-risk or high-risk vendor, regularly referencing these pages may be all that’s required in their risk management strategy.
An external attack surface scanning tool can provide additional invaluable information about potential risks associated with vendors public-facing IT assets. Leveraging such automation technology in due diligence processes will significantly improve the speed of vendor onboarding workflows, helping you scale your business faster and more securely.
All consolidated cybersecurity data for prospective vendor relationships needs to be compared against your inherent risk threshold, which should already be defined.

If you haven't yet defined your risk appetite, the process can be expedited by using a security rating tool specifying a minimum security rating a vendor must meet to be considered safe to onboard.
For more information about using security rating in your risk appetite strategy, refer to this post about calculating a risk appeite specific to Third-Party Risk Management.
Security ratings are real-time quantifications of a vendor’s security posture based on multiple attack vector categories.
Related: How UpGuard calculates its security ratings.

Risk appetites can also be calculated using qualitative methods, which process security decisions based on different threat scenarios rather than with a numerical value.
Your final choice of risk measurement methodology should be the option that best helps you achieve your specific cybersecurity objectives and expectations of stakeholders.
Step 2. Choose a criticality rating system
One of the most significant mistakes cybersecurity teams make at this point of the workflow is importing vendors into a single list with no attributes distinguishing low-risk from high-risk vendors. Making this error will set you up for a highly inefficient and ineffective Vendor Risk Management program.
Some vendors will require a more detailed risk assessment than others, and these vendors need to be easily distinguished in a criticality grouping strategy.
Your criteria for determining vendor criticality should be, first and foremost, based on whether the vendor will be processing highly sensitive information. Such vendors should be automatically assigned to your most critical tier.

Other contributing factors depend on the metrics and risk management strategies of your unique business goals. For example, healthcare industries may choose to prioritize factors impacting alignment with the third-party risk management standards of the HIPAA regulation.
Step 3. Setup a vendor risk assessment management system
For vendors given the green light to progress to onboarding, their completed evidence-gathering processes form the basis of their initial risk assessment. If a vendor is considered high-risk, a more in-depth risk assessment should be carried out by including security questionnaires.
A security questionnaire could either map to a specific framework or regulation relevant to your risk management goals or, depending on how specific your risk assessment needs to be, they could be custom-designed.
An ideal Vendor Risk Management platform, like UpGuard, offers both options - a library of editable questionnaire templates mapping to popular regulations and standards; and a questionnaire builder for a more focused evaluation of specific risks.
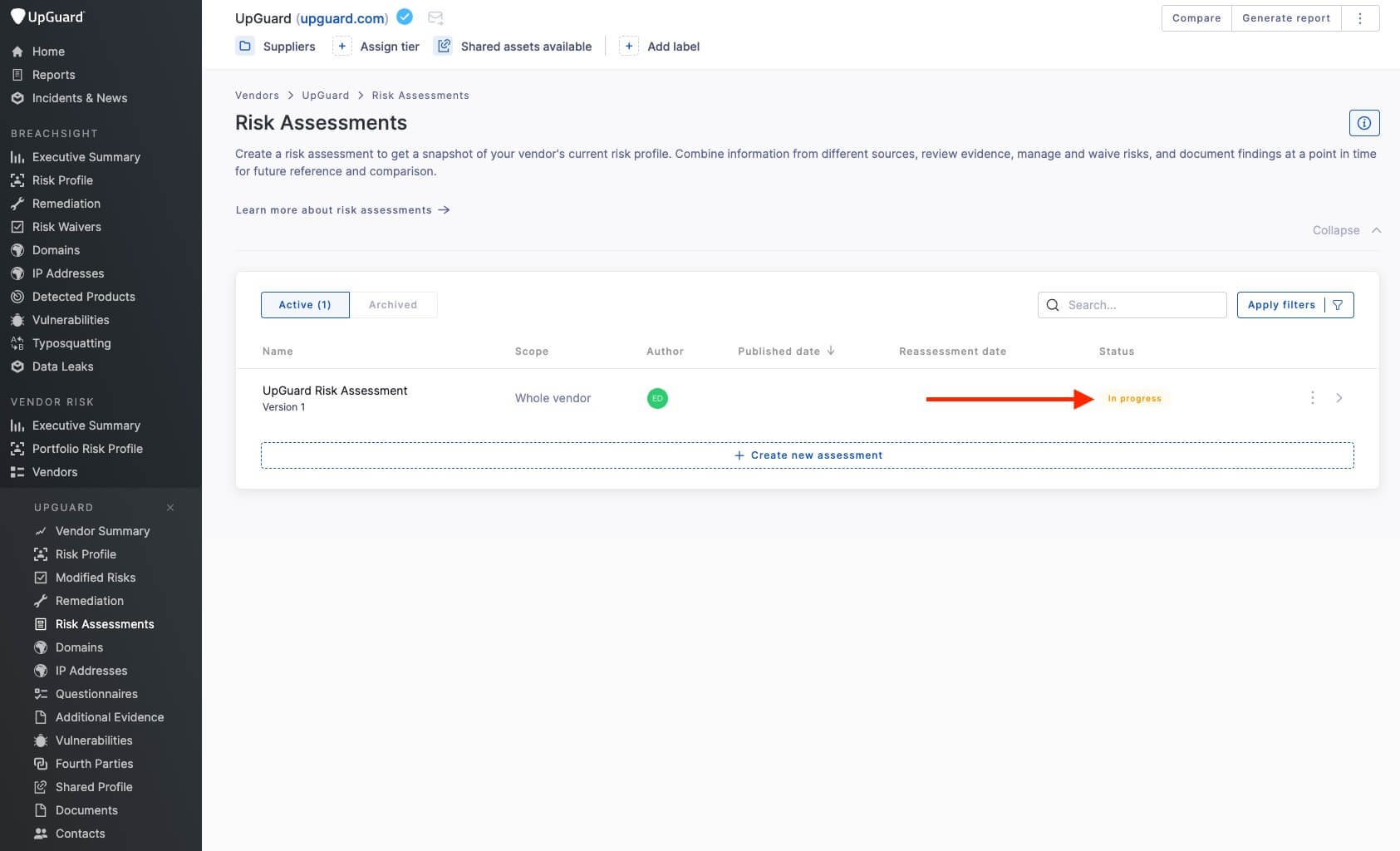
The progress of every vendor risk assessment you commence should be tracked. Overlooked risk assessments could hide potentially dangerous attack vectors from the radar of your continuous monitoring efforts, significantly increasing your risk of suffering a data breach.
Rather than tracking risk assessment progress in spreadsheets, establish a foundation for a scalable VRM program by managing your assessment in a VRM tool.
For inspiration for further streamlining your risk assessment workflow, watch this video:
Step 4. Set a risk management framework
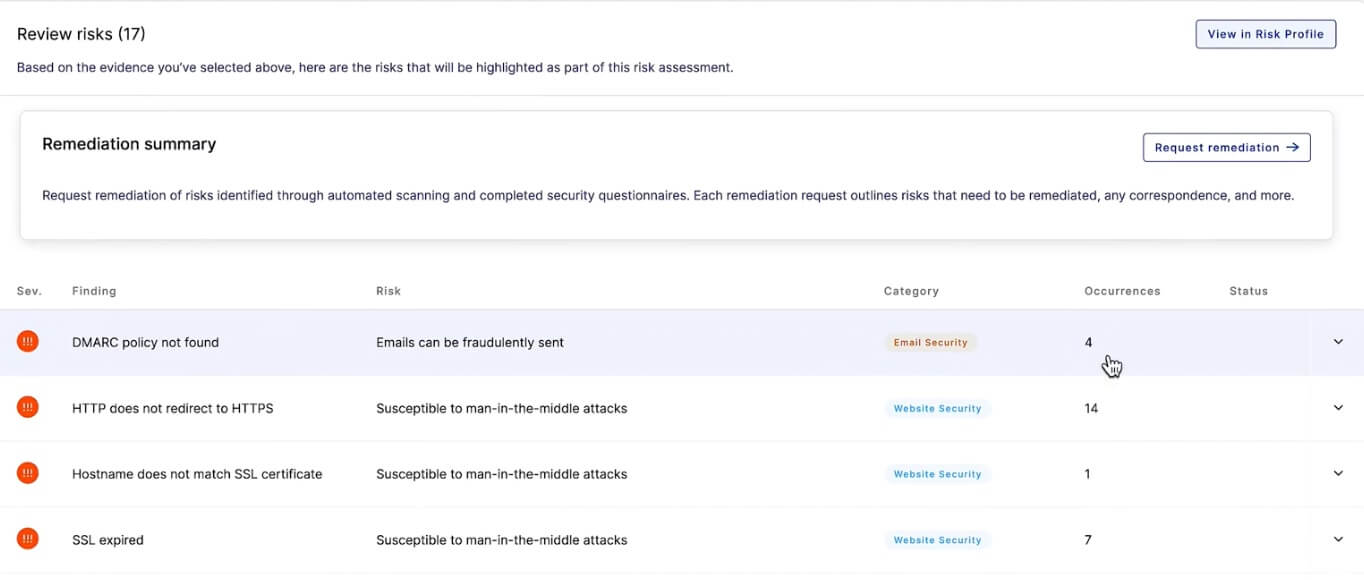
All risks detected in the risk assessment process must be acknowledged, starting with the most critical risks. This effort is simplified when automatic attack surface scanning data is augmented into risk assessment processes, as critical risks requiring follow-up actions are highlighted and prioritized.
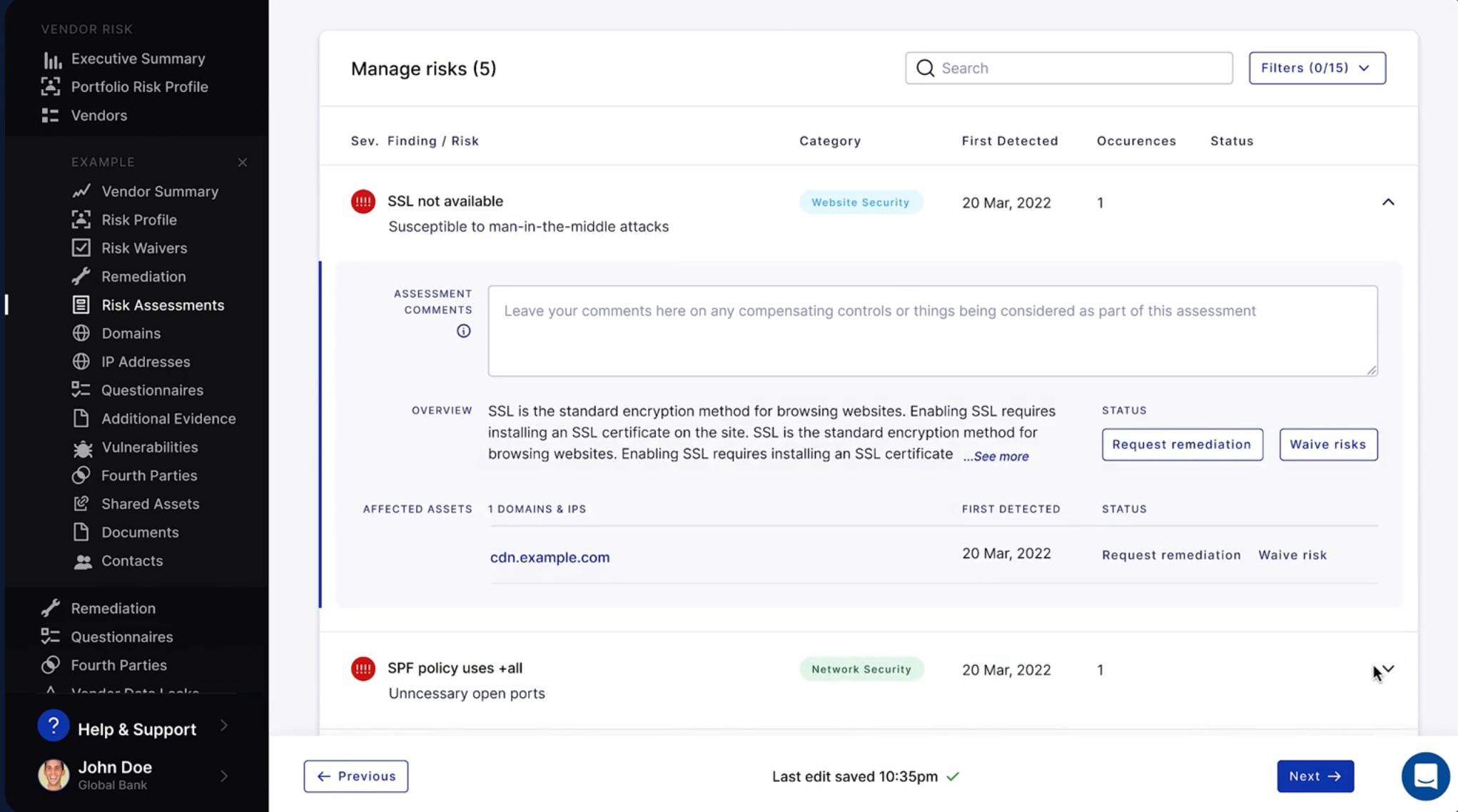
To support efficient remediation efforts, security personnel overseeing risk assessment workflows should have the option of waiving detected risks that don’t apply, such as risks associated with low-risk vendors with no access to sensitive customer data.
Step 5. Review the output of your risk assessment
By this stage, your vendor risk assessment is complete. Before it’s finalized, a risk assessment must pass through a rigorous review process to ensure accuracy. During review, comments and risk management recommendations should be added for each type of risk requiring a management strategy.
A finalized risk assessment outlines the design of an ideal risk management strategy for that vendor.
Finalized vendor risk assessments can also be shared with stakeholders to give them visibility into your expanding third-party attack surface and subsequent plans for managing it effectively.
The UpGuard platform can help you accelerate the finalization of each risk assessment by generating a risk assessment template consolidating all relevant data gathered from the assessment workflow, with the inclusion of pre-populated commentary.

Best Practices Vendor Risk Assessments in 2024
To ensure your established risk assessment processes remain impactful and efficient as you scale, be sure to follow these best practices:
- Segment Vendors by Risk Level: Attribute a criticality rating to each vendor based on the level of risk they post to your organization. This will allow high-risk vendors to be readily prioritized in continuous monitoring and ongoing risk assessment processes.
- Implement Comprehensive Due Diligence: Conduct a thorough security posture evaluation for each potential vendor to determine whether they’re safe to consider onboarding. Consider all risk categories relevant to your business operation objectives, such as regulatory, cybersecurity, and financial risks.
- Standardize Contracts with Security Clauses: Ensure all vendor contracts specify your security requirements, compliance obligations, data protection standards, and breach notification procedures.
- Use Technology to Enhance Attack Surface Visibility: Leverage third-party attack surface scanning technology to track emerging third-party risks that could trigger a risk assessment process.
- Develop Vendor Termination Policies: Establish vendor termination policies specifying criteria for rapidly terminating vendor relationships, emphasizing circumstances threatening the safety and integrity of your sensitive data.
- Establish Incident Response Protocols: Define clear procedures for collaborative incident response efforts with vendors in the event of a third-party data breach or major security incident.
- Leverage Industry Benchmarks and Standards: Align your Vendor Risk Management practices with a proven industry-standard cybersecurity framework, such as NIST Cybersecurity Framework version 2.0.
- Keep stakeholders in the loop: Involve stakeholders in regular VRM performance reviews to foster a culture of vendor risk awareness.
FAQs about Vendor Risk Assessments
How often should vendor risk assessment be conducted?
For high-risk vendors (those processing sensitive data), risk assessment could be performed as often as on a monthly basis. Some factors may trigger a risk assessment sooner, such as sudden changes in vendor security postures, changes in vendor services, or updates to industry regulations.
Who should be involved in conducting a vendor risk assessment?
Risk assessment processes usually involve compliance and security teams. Depending on the scope of the assessment, other departments could be involved, including IT, Legal, and Procurement.
What are the key differences between initial and periodic vendor assessments? is
An initial risk assessment is used to outline a risk management strategy for newly onboarded vendors. Ongoing risk assessments ensure each vendor’s risk profile doesn’t exceed specified thresholds.
What tools can be used to automate the vendor risk assessment process?
VRM tools like UpGuard leverage automation technology into their risk assessment workflows.
What should be included in a vendor risk assessment?
All discovered risks potentially impacting the cybersecurity, regulatory compliance, and strategic objectives of your business.
What are common mistakes in vendor risk assessments?
- Insufficient data collection during due diligence resulted in vendors with poor security performance being onboarded.
- Not following up on incomplete security questionnaires delayed risk assessment processes.
- Poor risk assessment management obscures visibility into risk assessment progress.
How should I update my risk assessment strategy to cope with new technologies like AI?
Choose a risk assessment tool that’s continuously being improved alongside advances in new AI technology.




