An efficient Vendor Risk Management workflow compresses the timeline between risk discovery and remediation, significantly reducing your chances of being impacted by a third-party breach.
If you’re currently struggling to manage your vendor security risks, in this post we outline a proven Vendor Risk Management process to help you improve the efficiency and scalability of your risk management efforts.
Learn how UpGuard is streamlining Vendor Risk Management >
6-Stage Vendor Risk Management Workflow
This framework is based on the Vendor Risk Management workflow on the UpGuard platform. For an overview of its application with UpGuard, watch this video:
1. Identify all of your third-party vendors
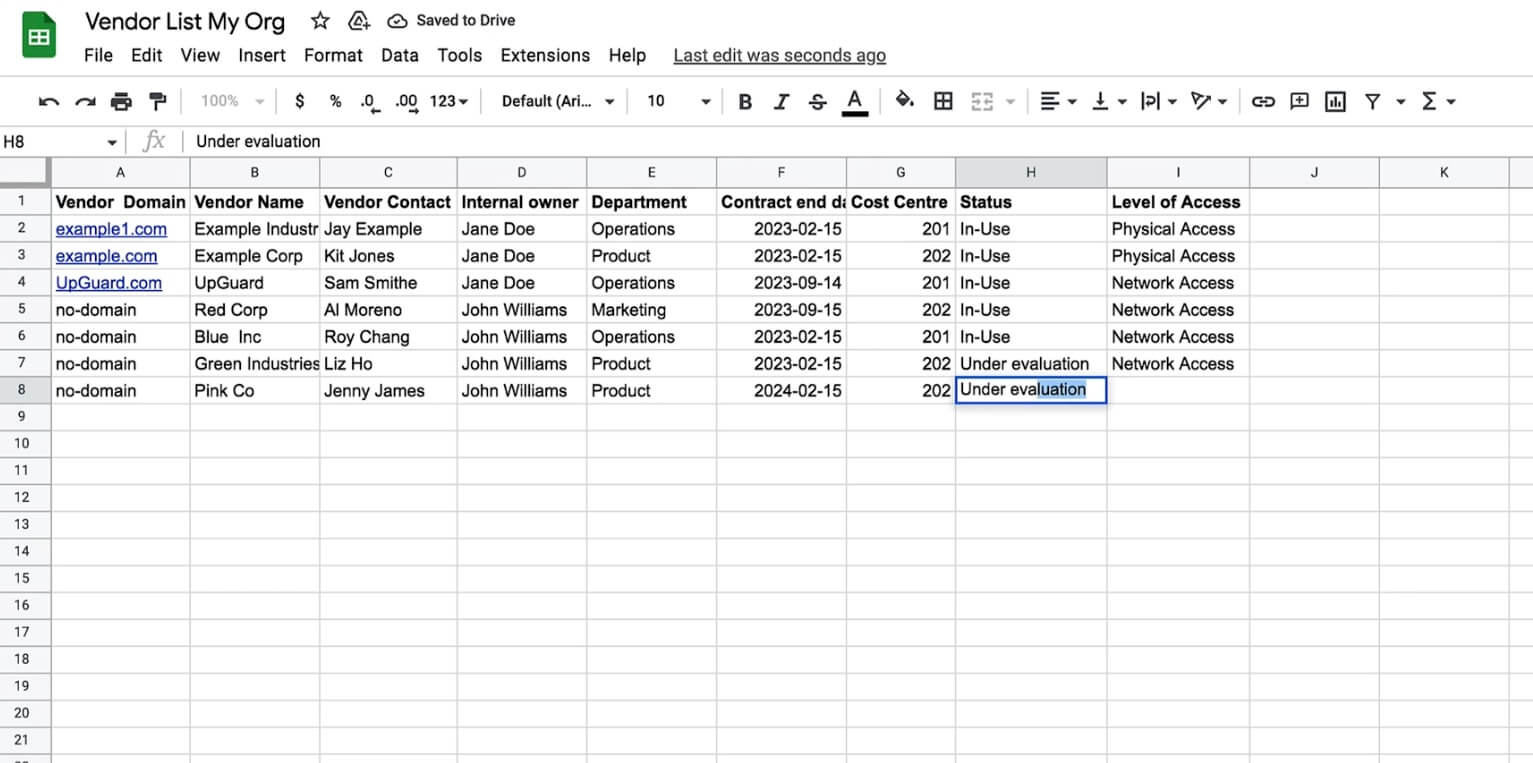
List all third-party vendors and service providers making up your digital footprint in a spreadsheet. This list must be 100% accurate; an overlooked vendor is an overlooked attack vector that could become the reason you suffer a data breach.
Don’t blindly trust a vendor list saved in a document. Always confirm your actual network of vendors with additional discovery methods.
Some additional methods of identifying your vendors include:
- Digital footprint mapping - The processing of identifying all of your internet-facing assets and comparing them to your external attack surface. When implemented alongside sensitive data flow diagrams, digital footprint mapping could uncover blind spots between customer data flows between your assets and potentially overlooked vendor services.
- Automatic detection through a VRM platform - Some VRM platforms can automatically detect vendors in your network to expedite the process of third-party service discovery. Ideally, a VRM solution should be capable of automatically detecting your third-party vendors (your vendor’s vendors) since the impact you could potentially suffer from a compromised vendor extends to the fourth-party attack surface.

Get a free trial of UpGuard >
Your final list of vendors should be structured to include all relevant information and metrics required to manage each vendor effectively.
Some vendor attributes that could help you locate and manage vendors more efficiently include:
- Vendor contract start and end dates
- Name of internal owner
- Details of primary contact
- Departments being serviced by the vendor
- Which business operations are being supported
- Any major integrations that are dependent on a vendor for uninterrupted service levels
- Which procurement function a vendor is associated with
- Whether or not a vendor is required to maintain business continuity
- Whether a vendor processes sensitive information
Time-saving tip:
If you’re using a Vendor Risk Management tool, your list of vendors can be imported instantly and organized into your VRM workflow.

2. Group your critical vendors separately
To establish a foundation for an efficient vendor risk assessment process, high-risk vendors - those processing sensitive customer data - should be assigned to a higher criticality tier. These service providers will likely require full risk assessments, including questionnaires more regularly, and grouping them separately is an efficient method of quickly identifying vendors with more comprehensive assessment requirements.
Lower-risk vendors may not require a full risk assessment. Usually, regular review of their automated security risk scanning results or publicly available security and trust information is all that’s required during their relationship lifecycle.
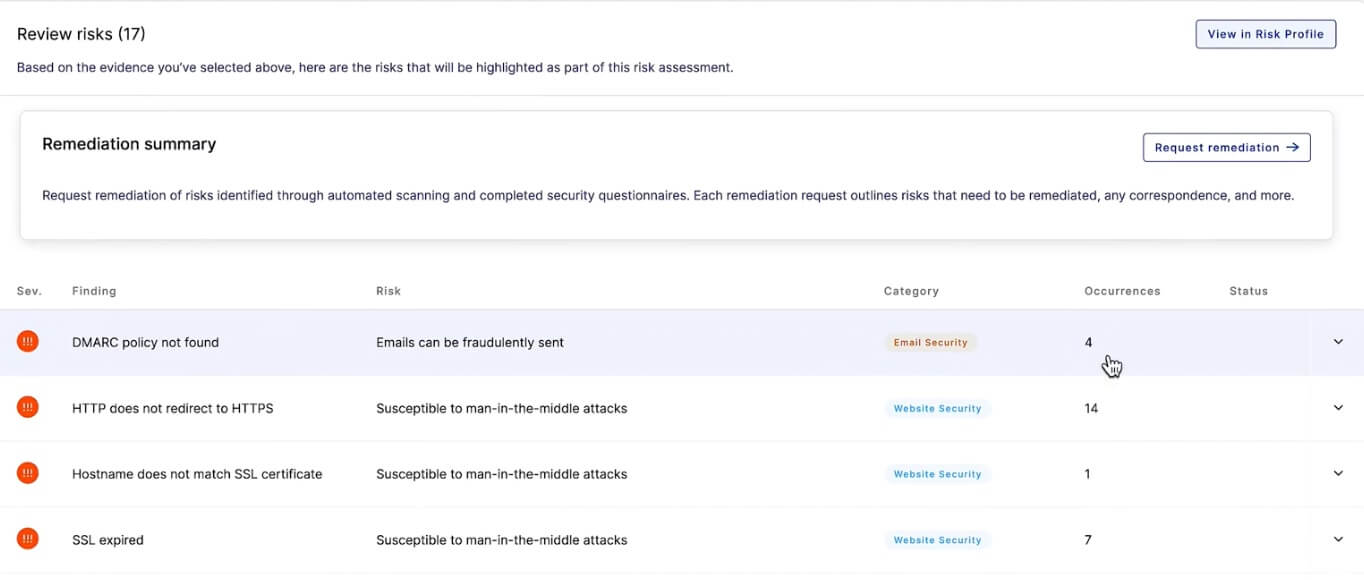
Vendor tiering helps security teams quickly identify which vendor assessments must be prioritized.
Learn how to scale your VRM program with automation >
3. Identify which vendors impact your regulatory compliance efforts
Third-party vendor security risks could significantly impact your level of regulatory compliance. Revise all the regulations and industry standards applicable to your organization, and how each vendor could impact alignment efforts. After this review, some vendors with a potentially high compliance impact may need to be escalated to a higher criticality tier.
Some popular regulations and standards with third-party risk management standards include:
Learn how to communicate third-party risks to stakeholders >
4. Conduct an Initial Vendor Risk Assessment
With all your vendors identified, it’s time to complete an initial risk assessment. For newly onboarded vendors, the initial assessment should involve an Internal Relationship Questionnaire - a questionnaire that helps consolidate all of the information you currently know about the vendor.
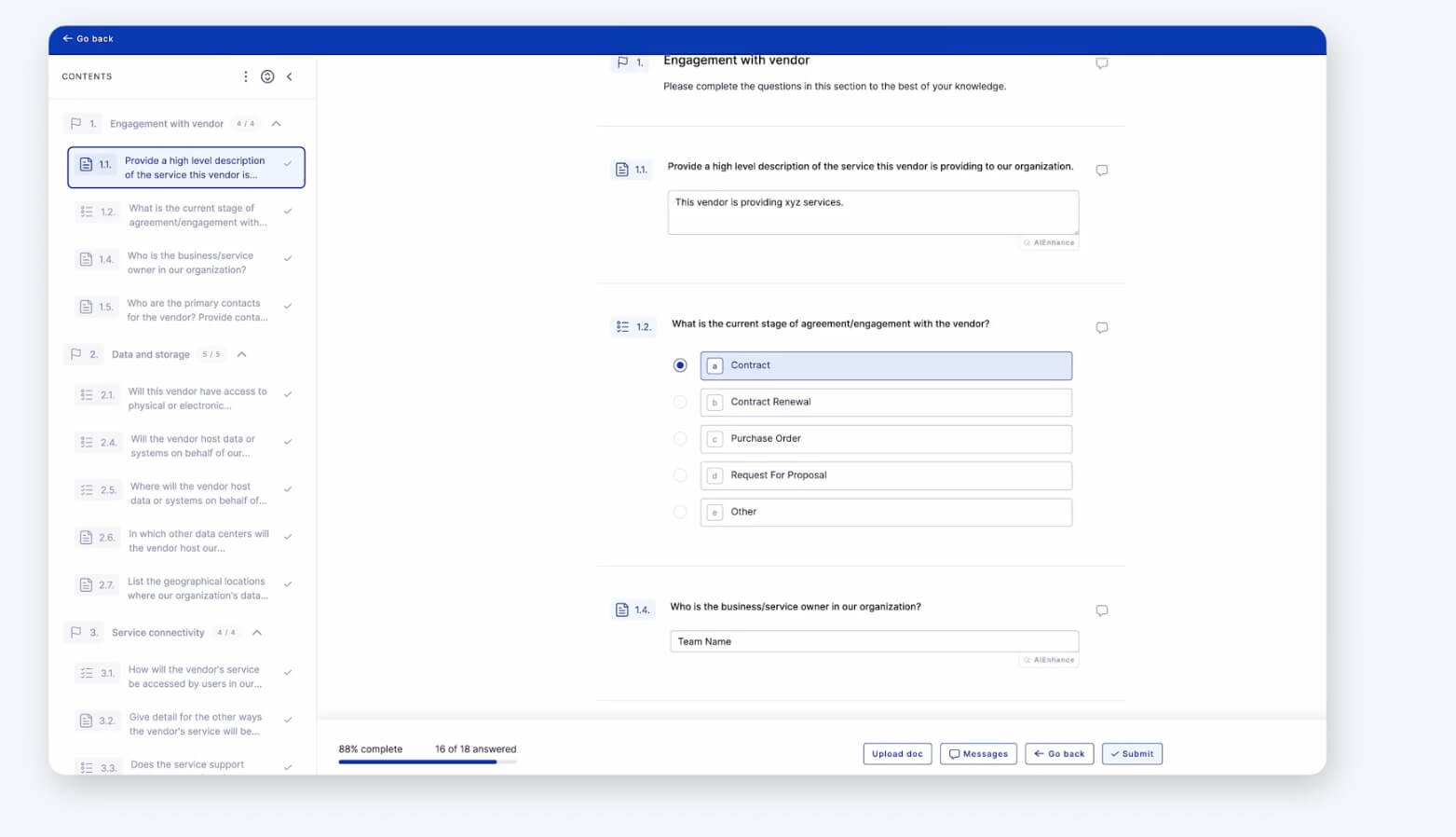
The final composition of each business’s risk assessment will vary depending on which industry standards and regulations they are bound to. Your investigation into applicable regulatory standards completed in the previous will establish the groundwork for which security questionnaires need to be included in your assessments.
Questionnaires could map to regulatory standards of popular cybersecurity frameworks. Some examples include:
- Modern Slavery Questionnaire
- PCI DSS Questionnaire
- Health Insurance Portability and Accountability Act (HIPAA) Questionnaire
- Essential Eight Questionnaire
- NIST Cybersecurity Framework Questionnaire
- California Consumer Privacy Act (CCPA) Questionnaire
- Web Application Security Questionnaire
- GDPR Security Standard Questionnaire
- NIST SP 800-53 Rev. 4 Security Standard Questionnaire
- Physical and Data Centre Security Questionnaire
- Infrastructure Security Questionnaire
All of these questionnaires and more are available as templates on the UpGuard platform.
All risk assessments begin with an Evidence-gathering stage - the process of collecting security information to paint a comprehensive picture of each vendor’s security posture.
Evidence Gathering could be performed during the vendor selection process, as part of a due diligence strategy, or during onboarding. In both circumstances, you’re evaluating the potential risks a vendor could introduce to your organization (inherent risks) and how these risk profiles compare to your risk appetite.
For potential service providers with risk exposures exceeding your business’s risk appetite, the journey ends here, at the Evidence Gathering stage. They should be immediately disqualified from onboarding considerations. New vendors with acceptable risk profiles will then proceed to have their risks managed through security controls throughout the entire vendor relationship lifecycle.
Learn these tips for completing risk assessment faster >
Four primary data sources collectively create the most comprehensive picture of a vendor’s inherent risk profile. They are:
- Automatic scanning results - External scans of a vendor’s internet-facing assets and their associated security risks, with the result quantified as a security rating.
- Security Questionnaires - A point-in-time evaluation of a vendor’s security posture and alignment with relevant regulatory standards.
- Publically available security and trust information - A public page listing all of the vendor’s main cybersecurity initiatives.
- Additional Evidence - Any extra evidence collected about the vendor that could provide greater context about their security posture, such as completed questionnaires and certifications.
If a prospective vendor demonstrates critical risks during the Evidence-Gathering stage, they should not progress to onboarding.
Some vendor risk categories to consider during the Evidence Gathering stage include:
- Regulatory Compliance Risks - Regulations are increasing their emphasis on third-party risk management. A vendor’s poor compliance efforts could result in costly violation fines for your business. Vendor compliance requirements should be assessed against the following popular regulations:some text
- HIPAA (for the healthcare industry)
- GDPR (data privacy and data security)
- PCI DSS (for cybersecurity deficits causing financial risks)
- Supply Chain Risks - Specifically in the context of service provider cybersecurity risks, increasing your potential of being impacted by a supply chain attack.
- Reputational Risks - A potential vendor’s poor public reputation may be the result of a major cyber attack.
- Operational Risks - These risks could disrupt alignment with the standards of popular cybersecurity frameworks (such as NIST CSF 2.0), which could negatively impact a third-party vendor’s information security efforts
Learn how to choose an effective Vendor Risk Management solution >
5. Establish a vendor risk assessment routine
With all initial risk assessments complete, you should now understand what information (such as security questionnaire type) is required in each vendor’s risk assessment process and how comprehensive theirassessment needs to be.
If your Vendor Risk Management program offers a tiering feature, your risk management lifecycle becomes intuitive - complete risk assessments for critical tiered vendors much more often.
A vendor risk matrix makes this process more efficient, indicating lapses in vendor performance as measured through security ratings. This allows security teams to instantly identify vendors with potentially critical security vulnerabilities requiring investigation with risk assessments.

Learn how to create your own vendor risk matrix >
Knowing when to send a risk assessment is pointless if you’re not tracking their completion rates. A backlog of incomplete risk assessments means your security teams aren’t operating with an accurate understanding of your vendor attack surface, severely limiting the impact of your vendor risk assessment processes.
With VRM tools like UpGuard, you can easily track all incomplete risk assessments by filtering your dashboard view to all in-progress assessments.
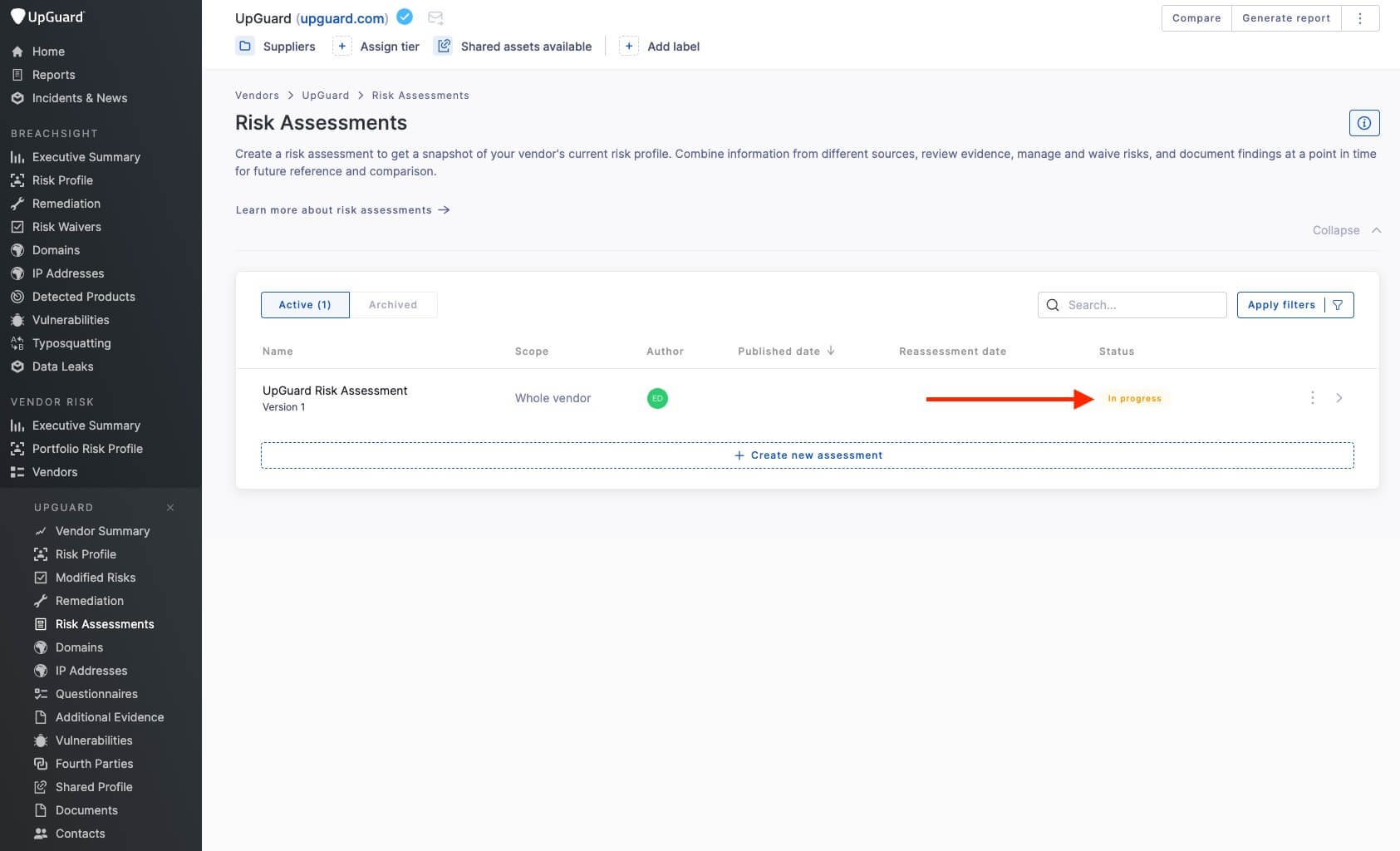
Watch this video to learn how UpGuard streamlines risk assessment workflows.
6. Establish a notification system
A notification system prevents important risk mitigation tasks from being overlooked in the vendor lifecycle. They can also be set up to notify your security team when a vendor’s security posture drops below a specified threshold, simplifying your continuous monitoring efforts.
Some suggestions for notifications to set up as part of an ongoing monitoring strategy include:
- When a vendor’s security ratings drop below a specified value
- When important security breach information about a vendor is detected
- When remediation tasks are submitted.
Third-party risk integrations with risk assessments, such as JIRA and ZAPIER, automatically trigger notifications to remediation teams when requests are submitted, replacing the frustrating and outdated method of tracking remediation tasks via email.

For more vendor collaboration improvement suggestions that will elevate your VRM workflow efficiency far above that of your competitors, watch this video:




