A Vendor Risk Management framework is the skeleton of your VRM program. Without it, your Vendor Risk Management program will collapse under a heavy burden of inefficient processes.
This post outlines the anatomy of an effective VRM framework to help you seamlessly manage security risks in your third-party network.
Learn how UpGuard streamlines Vendor Risk Management >
What is a Vendor Risk Management framework?
A Vendor Risk Management framework outlines how vendor security risks should be managed in your VRM workflow.
A VRM framework sets guidelines for mitigating and managing cybersecurity risks across four primary stages of the vendor lifecycle.
- Vendor Due Diligence - Ensuring security teams only consider vendors with an acceptable potential impact on the organization’s security posture.
- Vendor Onboarding - A workflow for securely integrating new vendors into the company's digital footprint.
- Ongoing Third-Party Risk Management - Continuous monitoring of onboarded vendors to ensure their risk profiles always remain within acceptable limits.
- Vendor Offboarding - Ensuring best cybersecurity practices are followed when vendor relationships cease, such as ensuring the company's digital footprint is reduced every time a vendor is offboarded.
Why is a Vendor Risk Management framework important?
A Vendor Risk Management framework provides a roadmap for establishing an efficient VRM program. If a VRM program is implemented without initially considering its framework structure, the processes between each stage of the VRM lifecycle will be disparate, resulting in an inefficient management of vendor security risks.
An inefficient VRM program is likely to miss critical data breach attack vectors in your third-party threat landscape, an error that could cost you USD 4.66 million.
The average damage cost for data breaches involving third parties is USD 4.66 million, $216,441 higher than the global average of USD 4.45 million.
- 2023 Cost of a Data Breach Report (IBM and Ponemon Institute)
By first focusing on the design of a framework for your VRM program rather than specific processes, you're able to devote greater focus to the efficiency aspects of your developing VRM program, which will then naturally lead to seamless process integration.
Related: How to design an efficient VRM workflow.
4-Stage VRM Framework for an Efficient VRM Program
This VRM framework can be used as a template for establishing the groundwork for your own Vendor Risk Management program. If you already have a VRM program in place, this framework could inspire ideas for improving the efficiency of your current VRM workflow.
This is a four-stage framework addressing the complete lifecycle of third-party vendor relationships.
Stage 1: Secure Vendor Onboarding Workflow
The initial stage of the framework sets the structure for the complete vendor onboarding workflow, which consists of two main sub-components:

- Due Diligence - The process of scoping prospective vendors to determine if their inherent risk profile fits within your defined appetite.
- Onboarding - The process of establishing a risk management strategy ensuring onboarded vendors maintain acceptable levels of risk
Vendor Due Diligence
Your due diligence strategy should be based on your business's unique Vendor Risk Management objectives. Ultimately, this is summarized as a risk appetite calculated specifically for Third-Party Risk Management (TPRM).
To set the context for your due diligence standards, establish an overarching objective for your VRM program. If your risk appetite is quantified with security ratings, your overarching objective could be to prevent vendors from dropping below a specific security rating value.
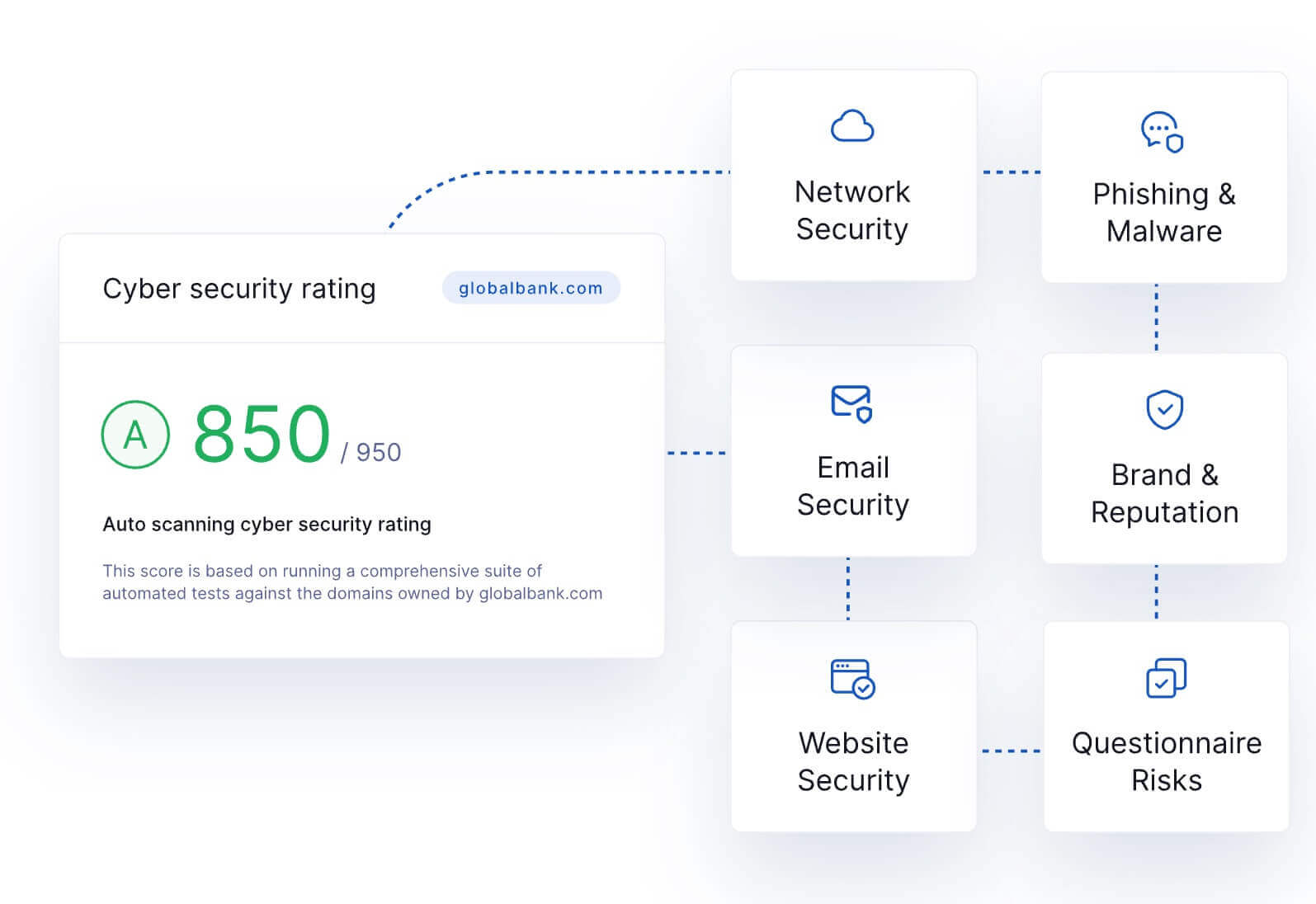
Example of overarching VRM objective:
“Our vendors will not fall below a security rating value of 750.”
Related: How UpGuard calculates its security ratings.
In addition to an overarching VRM objective, establish objectives and goals for each category of vendor risks you aim to mitigate. The added benefit of clearly defining your VRM objectives is that it also outlines VRM performance metrics to potentially track in stakeholder reports.
Related: How to report third-party risks to the board.
Here are some VRM objective + goal examples for four vendor risk categories
Information Security Risk
- Goal: Minimize the risk of third-party data breaches by strengthening the information security frameworks of vendors.
- Objective: Conduct quarterly risk assessments to track alignment with information security best practices outlined in NIST CSF.
Compliance Risk
- Objective: Map current vendors' risk profiles to the regulatory requirements of PCI DSS.
- Goal: To achieve zero compliance violations due to vendor security issues.
Operational Risk
- Objective: Establish a business continuity plan that accounts for disruptions in vendor services supporting critical business functions.
- Goal: Ensure minimal operational impact during disruptions to critical vendor services.
Supply Chain Security Risk
- Objective: Implement a means of continuously monitoring the vendor supply chain for vulnerabilities that could facilitate a supply chain attack
- Goal: Prevent data breaches originating from supply chain security risks.
Related: 11 ways to prevent supply chain cyberattacks.
Your set of objectives and goals should offer a window into how rigorously your due diligence efforts need to be.
When performing vendor due diligence, the following data sources will help you build a high-level risk profile mapping to your VRM objectives and goals.
- Trust and Security Pages - A web page outlining a vendor's cybersecurity efforts, such as certifications, regulatory compliance, and general cyber risk exposure minimization efforts - here’s an example.
- Automatic Scanning Results - Vendor security risks are discovered with an external attack surface scanning tool, identifying threats that could potentially facilitate a data breach.
A non-invasive scan of a vendor’s superficial external IT ecosystem is an excellent way of commencing your vendor due diligence, as it allows you to instantly disqualify vendors failing to meet your minimal security rating requirements.
For your Vendor Risk Management program to hold to its ultimate goal of reducing data breach risks, the pathway to securing a partnership with your business should be intentionally narrow, only permitting access to vendors essential for supporting key business objectives. Your sensitive data is your business's most precious commodity and shouldn’t be made liberally available to any vendor.

Only vendors that pass a series of security checks should have the option of accessing your sensitive data.
Here’s a framework for determining the necessity of a potential vendor:
- Identify the specific operational challenges the vendor will resolve.
- Map these potential operational benefits to your organization’s overall strategic objectives.
- Decide whether the positive impact on your strategic objectives is significant by quantifying it as a dollar value.
- Estimate the potential financial risks of onboarding the vendor due to reputation risks or compromise of outsourced processes involving high-risk internal data.
- Determine how much sensitive data access will be required to support the vendor’s performance.
Vendor Onboarding
The onboarding portion of this workflow should define the following vendor attributes.
- Vendor Lifecycle - Proposed length of the vendor relationship, marked by contract start and end dates.
- Roles and Responsibilities - Details of internal owners and their roles and responsibilities during all risk management processes, including ongoing monitoring and remediation.
- Compliance Requirements - Any specific regulations or industry standards impacted by the vendor’s potential risks, such as ISO 27001, NIST CSF, and HIPAA for healthcare industries.
- Service Level Agreements (SLAs) - The minimum service requirements the vendor agrees to deliver to support your business objectives. Clearly defined SLAs establish a benchmark for terminating vendor relationships, making the process faster and, therefore, more secure.
- Criticality level - All onboarded vendors should be assigned to a criticality tier so that high-risk vendors can be prioritized in risk management efforts.
To streamline the gathering of relevant vendor information to support onboarding administrations, send each new vendor a Relationship Questionnaire.

Related: Learn about the questionnaires available on the UpGuard platform.
These attributes will structure your vendor list so that it's optimized for importing into a VRM platform.
Stage 2: Establish a Vendor Risk Assessment Process
For an overview of an ideal end-to-end vendor risk assessment flow, watch this video:
Initial Risk Assessments
The security evidence gathered during the due diligence portion of this framework forms a basis for your initial risk assessment for onboarded vendors, defining the baseline security postures for all new third-party relationships. The initial risk assessment will potentially be your most comprehensive assessment for each vendor. Besides detailing each new vendor's impact across all the cyber risk categories you're tracking, an initial assessment will also guide the design of each new vendor's risk management strategy.
While completing each initial risk assessment, consider whether the vendor should be upgraded to a higher criticality tier, as this will streamline the establishment of your regular risk assessment cadence.
Ensure your initial risk assessment covers the following details:
- Any cyber frameworks the vendor is currently implementing - such as ISO 27001, NIST CSF, SOC 2, and Essential Eight.
- Any regulatory standards the vendor is bound to - such as PCI DSS, HIPAA, and GDPR.
- Details of the vendor’s current regulatory compliance efforts as documented in compliance reports
- Any compliance gaps between a vendor’s current state of compliance and your ideal state.
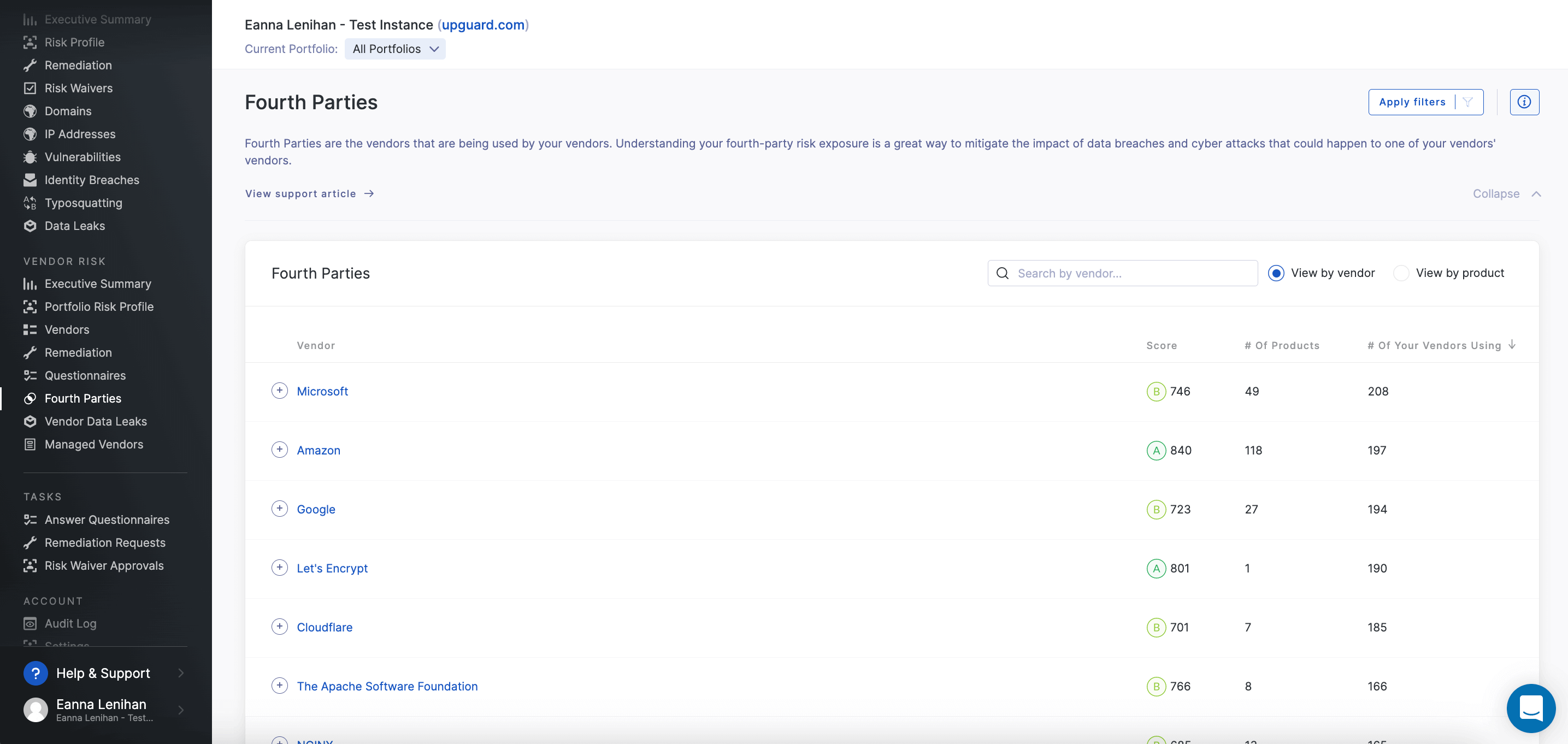
Your initial risk assessment should also aim to identify each vendor’s fourth-party vendors so that these entities can also be addressed in your risk management strategy. Your potential of suffering a data breach is determined by secuirty risks originating as far as your vendor’s service provider network.

Related: What is Fourth-Party Risk Management (FPRM)?
If you're using a VRM platform with automatic vendor detection capabilities, the tool could expedite the process of fourth-party entity detection by analyzing third-party vendor footprints.
To establish a template for your initial risk assessment, refer to this post on how to perform a cyber risk assessment.
Related: What is a Third-Party Risk Management Framework?
Ongoing Vendor Assessments
Beyond this initial risk assessment, a regular vendor risk assessment cadence should be established. In most circumstances, ongoing full-risk assessments will only apply to high-risk vendors - those entrusted to process sensitive data. For lower-risk vendors, regular review of their Trust and Security pages and automated scanning results is likely sufficient.
A full risk assessment involves security questionnaires for a deeper evaluation of emerging enterprise risks and the risk mitigation impacts of security controls.
Despite being the most detailed form of a vendor risk assessment, full assessments are considered point-in-time assessments because they can only evaluate security postures at a single point in time. This approach alone is very limited, as it fails to account for vendor security risks emerging between assessment schedules.
For the most comprehensive coverage of your Vendor Risk Management / Third-Party Risk Management program, point-in-time assessments should be combined with real-time monitoring.

Augmenting point-in-time assessments with real-time Attack Surface Management removes risk exposure blind spots between scheduled assessments, providing security teams with greater awareness of their actual third-party breach potential at any point in time.

Attack Surface Management is an excellent feature to integrate into this stage of your VRM framework.
Watch this video for an overview of the key features and capabilities of Attack Surface Management:
See UpGuard’s ASM features in action >
Stage 3: Establish An Efficient Vendor Collaboration Process
Sluggish vendor collaboration processes are the primary cause of inefficient VRM performance. These events aren't negligible frustrations; they could lead to costly regulatory violations due to delays in addressing compliance issues.
Poor vendor collaboration can be mapped to three likely causes:
- Lengthly and Questionnaires - Lengthy questionnaires require a significant investment of time to complete accurately. As such, questionnaires usually keep getting pushed behind more critical tasks.
- Repetitive Questionnaires - When multiple business partners send similar security questionnaires to a vendor, the frustrations of repeatedly answering the same questions often leads to a growing backlog of incompleted questionnaires.
- Poor Questionnaire Clarification Pathway - When vendors require clarification about specific security questionnaire items, these requests usually get sent via email, where they’re likely to be overlooked.
- Lack of a Centralized Questionnaire Hub - Without a centralized hub, all security team members don't’ have visibility into which questionnaires have been sent and completed, resulting in unnecessary back-and-forth clarifications with vendors.
All of these VRM efficiency-impeding issues can be addressed by integrating UpGuard Trust Exchange into your VRM framework, which is available for free to anyone.
UpGuard Trust Exchange combines the following features:
- Questionnaire Automation - An AI-powered engine empowering vendors to quickly answer repeated questionnaire items by referencing data from previously completed questionnaires.
- Central Questionnaire Management Hub - A centralized questionnaire storage hub to streamline collaboration between multiple parties required to complete each questionnaire.
- Vendor Shared Profile - A summary of a vendor’s security posture to expedite due diligence and risk assessment processes.
For an overview of UpGuard Trust Exchange, watch this video.
Get started UpGuard Trust Exchange >
Stage 4: Secure Vendor Offboarding Workflow
Your VRM lifecycle should be tied off with a secure offboarding workflow. The primary objective of vendor offboarding should be to remove access to all of your sensitive resources as quickly as possible. Expediting this process will reduce your risk of suffering a data breach should an offboarded member fall victim to a cyber attack.
Your offboarding protocol should be outlined in an official offboarding policy, outlining a multi-department effort to remove all points of access between the vendor and your business. These departments should include legal, procurement, cybersecurity, and compliance teams.
Related: Vendor Offboarding Best Practices
Compliance teams are especially critical to involve in offboarding as they will confirm whether all sensitive resource access has been revoked, mitigating the risk of non-compliance with data protection regulations like the GDPR.
If your vendors were imported into your VRM platform with a proper attribute structure, tracking all instances of data access will be easier.
An Attack Surface Management tool (mentioned in Stage 2 of this framework) could also support the offboarding stage of your VRM framework, identifying regions in your digital footprint where pathways with offboarded vendors are still in place, such as residual connections with third-party cloud services.




