Risk clarity for your attack surface, workforce, vendors, and customers
Take control of cyber risk with the only platform that spans your supply chain, attack surface, workforce, and trust relationships.
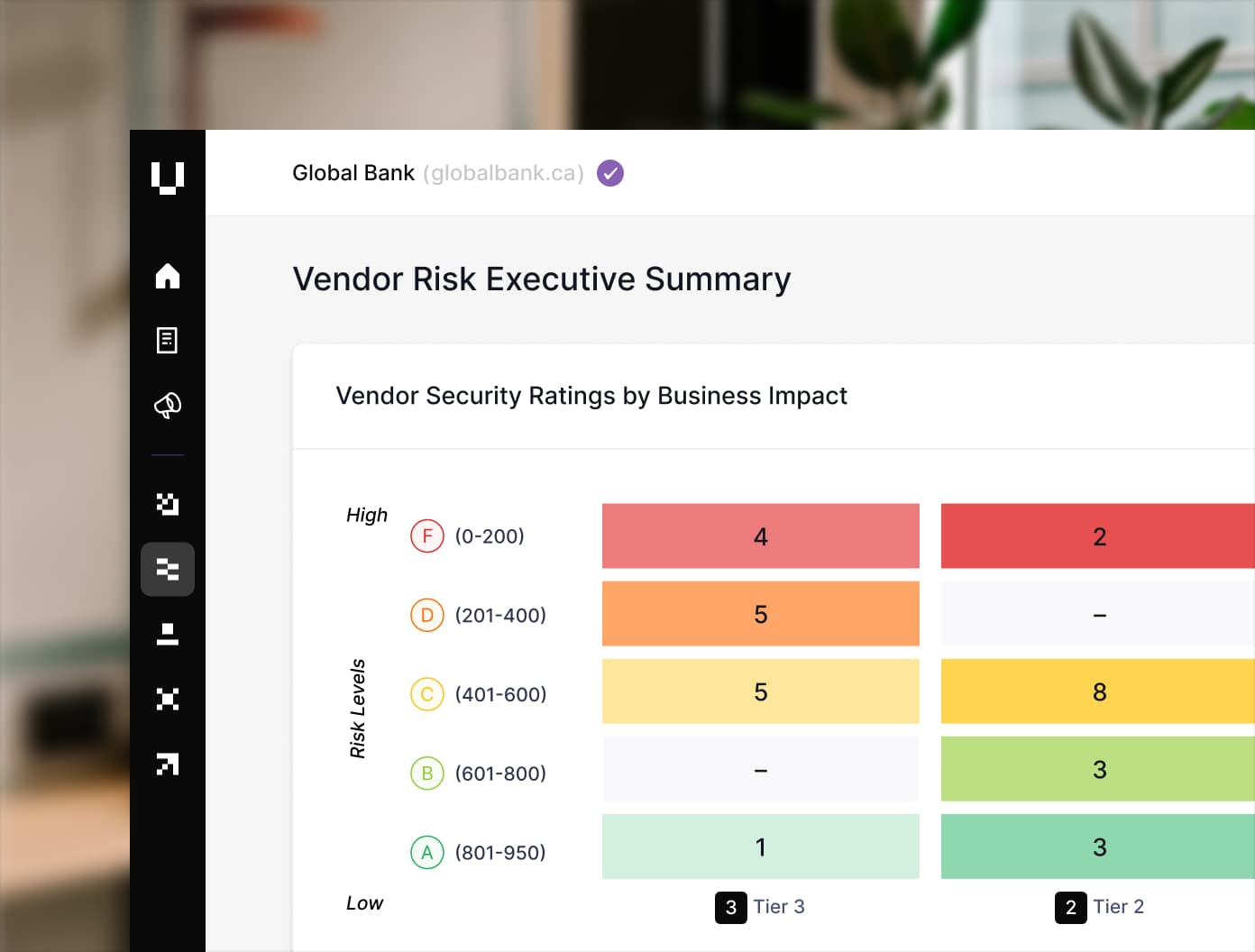
Vendor Risk Management
The holistic TPRM platform that delivers continuous vendor insights, 360-degree assessments, and efficient AI-powered workflows.
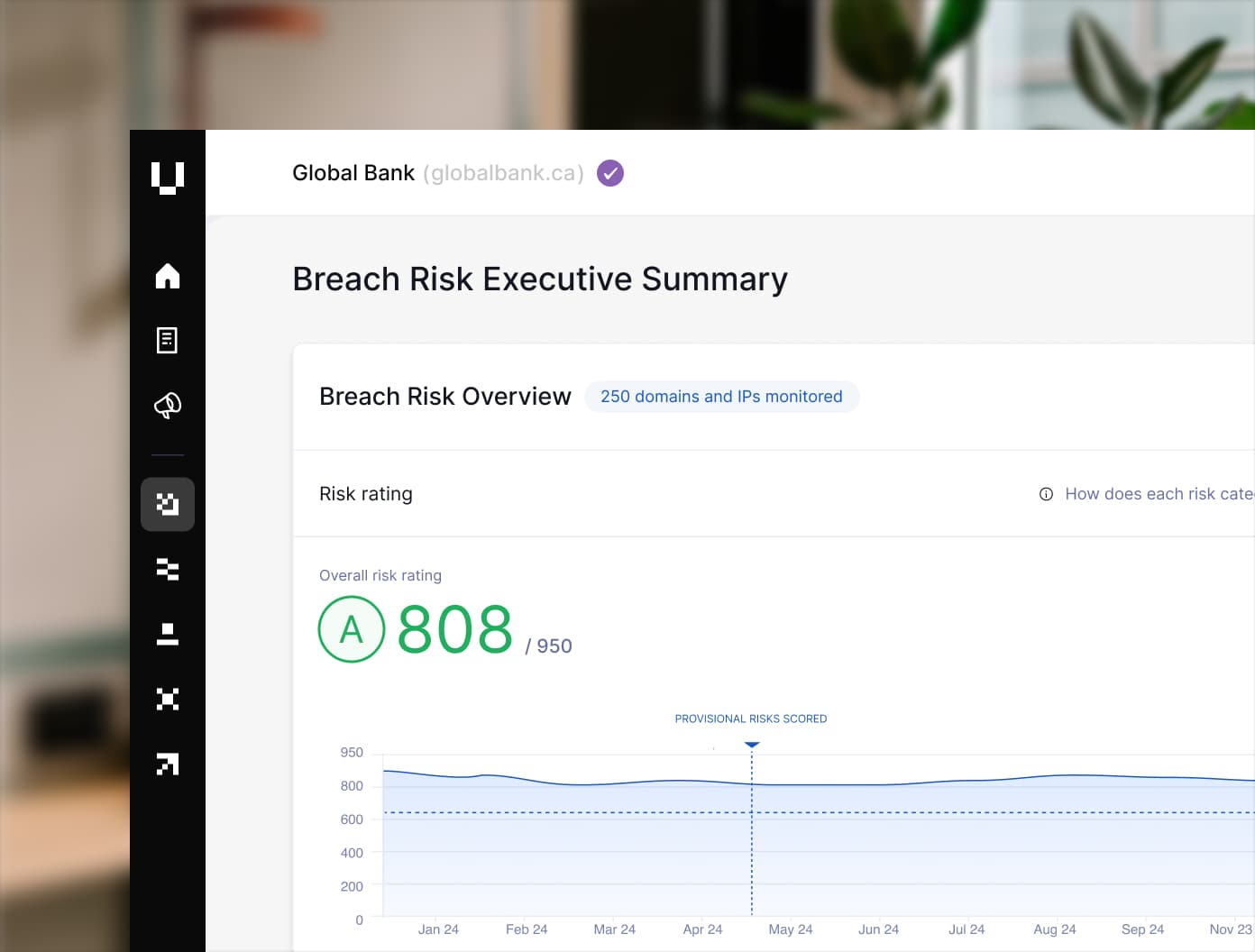
Attack Surface Management
Unlock continuous visibility into your digital footprint to detect real threats, know your full attack surface, and strengthen your cybersecurity posture—before attackers have the chance to strike.
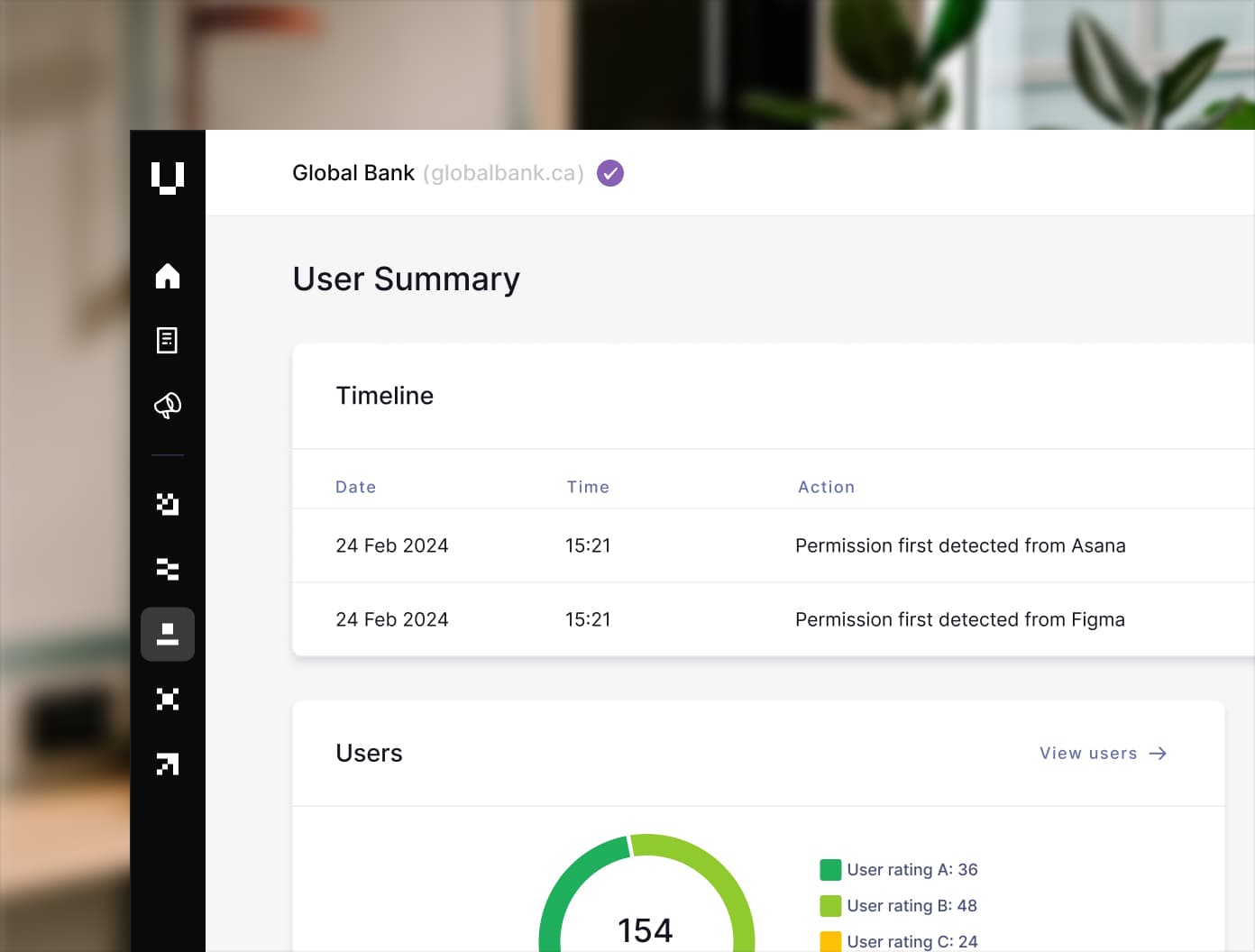
Human Risk Management
User Risk secures your workforce by giving you comprehensive visibility into your human risk, enabling safe AI adoption, and driving a security-first culture.
Trust Management
Build trust (and close deals) faster with AI-powered questionnaire automation, your own Trust Page, and collaboration-friendly features.

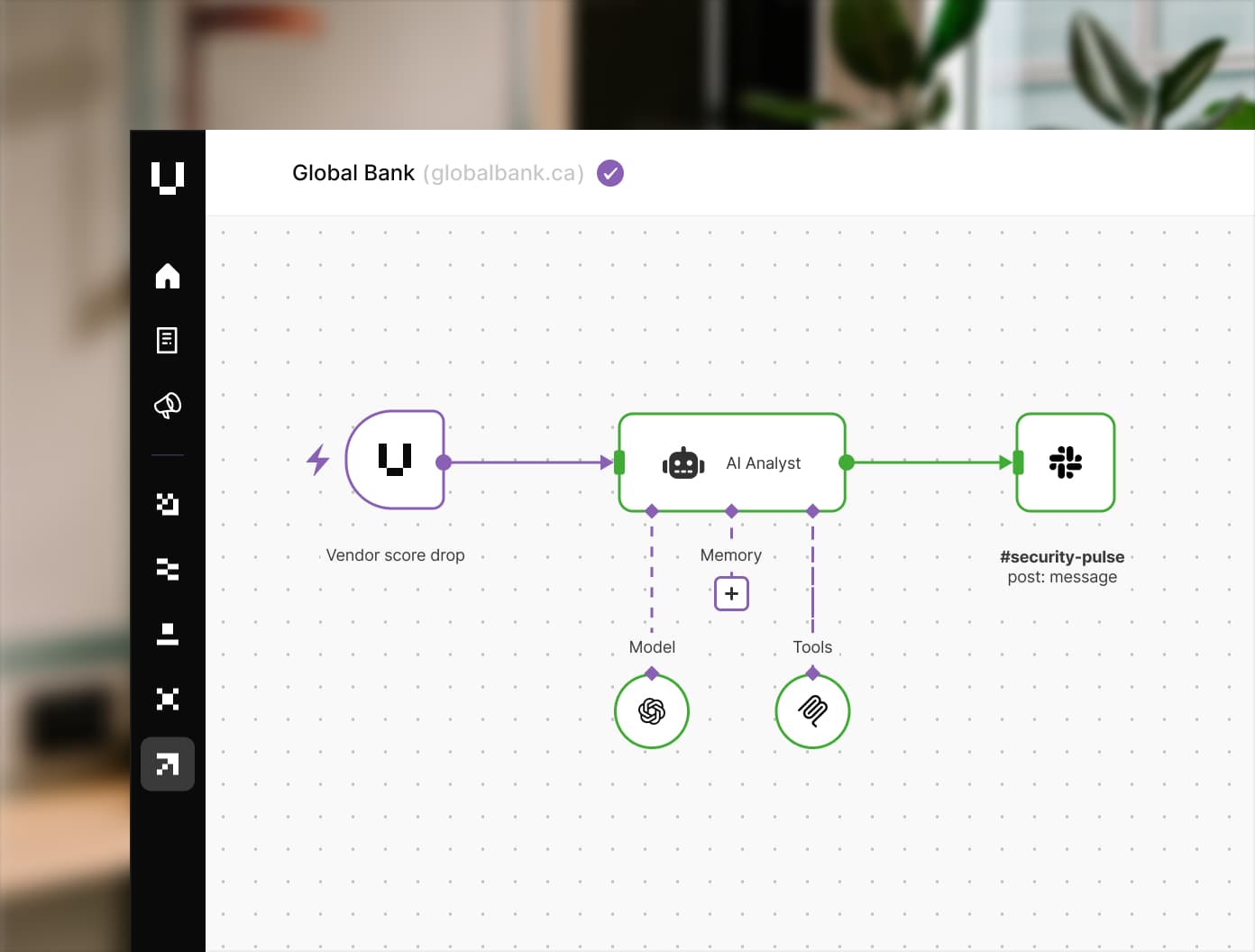
Risk Automations
Connect your risk stack to system APIs to automate discovery, notification, and remediation, enabling immediate and measurable action on every risk you find.
One posture.
One platform.
01 Unified
Take control with a unified view of cyber risk across your organization.
02 Continuous
Stay ahead of compliance by detecting control lapses as they happen.
03 Actionable
React faster with AI powered detection, prioritization and orchestration.
04 Measurable
Monitor performance through a single real-time posture loop.
Trusted by teams like yours


























