SIG Lite Questionnaire
Gain high-level insights into your vendors' information security controls. SIG Lite is ideal for organizations that want basic assessment due diligence and to conform to a recognized industry standard.
Combine the Shared Assessments’ Standardized Information Gathering (SIG) Lite Questionnaire with UpGuard’s robust security ratings and risk assessment workflow to streamline your processes, make informed decisions, and build more robust business relationships.
100,000
More than 100,000 SIGs are exchanged yearly
128
SIG Lite contains 128 risk control questions
What is the SIG Lite Questionnaire?
Maintain compliance and show due diligence in vendor assessments by using the SIG Lite Questionnaire.
- Designed to help organizations standardize the assessment of third-party vendors.
- Covers a range of IT security and risk management topics, including data privacy, network security and vulnerability management.
- Aligned with other security standards, frameworks and industry-specific regulations such as NIST, ISO, and GDPR.
Have a comprehensive understanding of your vendors
Know your third parties and perform vendor risk assessments.
- Gain instant insights into your vendors’ security measures and potential vulnerabilities
- Automatically detect risks and understand your vendors with security ratings that reflect the responses in UpGuard’s risk-mapped SIG Lite Questionnaire
- Implement accurate vendor risk assessments with the option of a standard or customized SIG Lite questionnaire
Simplify risk information collection
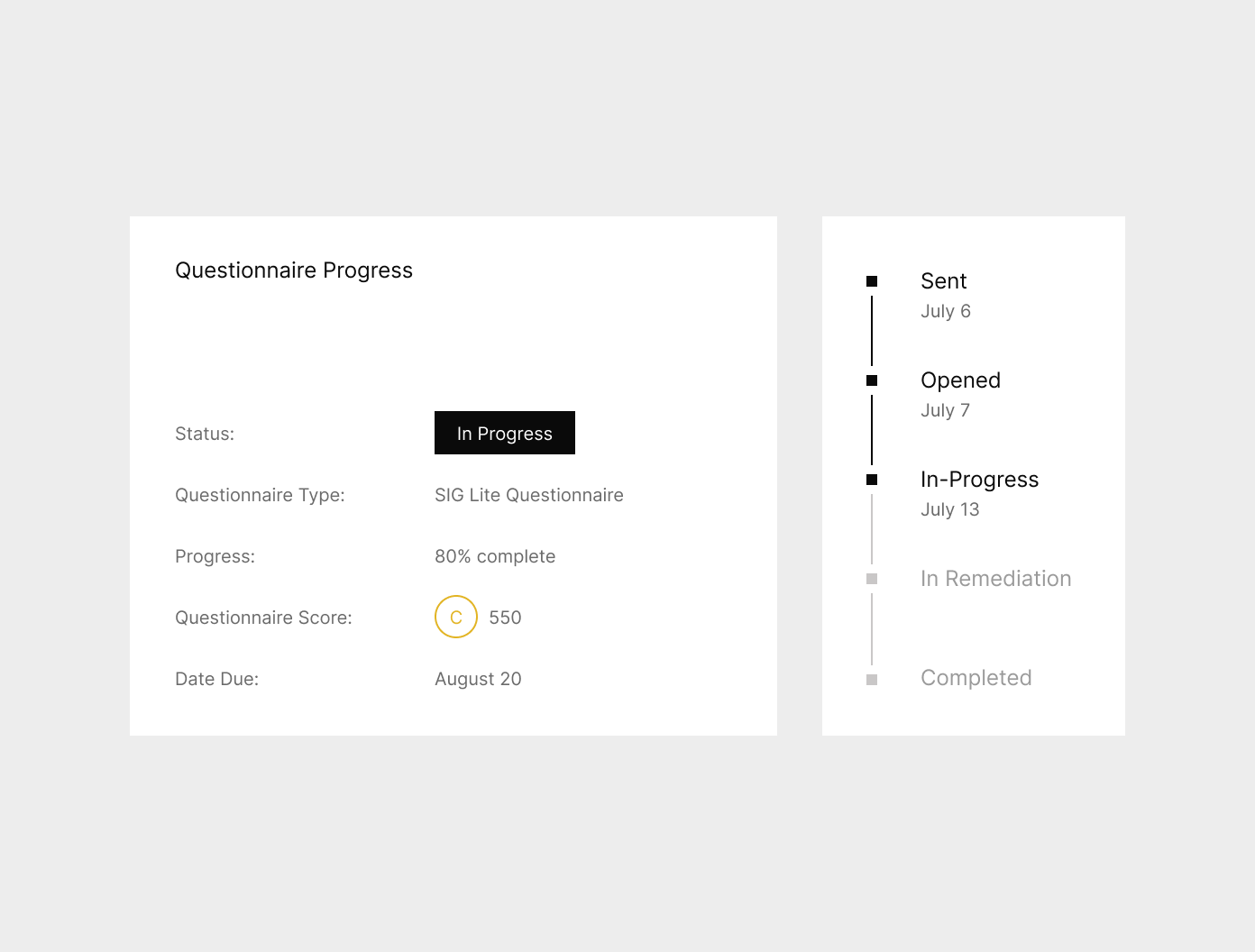
Streamline data collection and vendor risk assessments.
- Simplify risk information gathering and vendor assessment, for enhanced efficiency and greater accuracy
- Save time and resources with UpGuard’s pre-built SIG Lite Questionnaire instead of creating your own.
- Automate the process of collecting and analyzing responses with the SIG Lite questionnaire
Standardise
Ensure consistency in vendor data collection and risk assessments
Automate
Automate the collection and analysis of vendor responses
Remediate
Proactively identify and address risks with vendors
Comply
Ensure adherence to frameworks and regulations