Cisco has released a Product Security Incident Response Team (PSIRT) advisory regarding a zero-day vulnerability in the web UI feature of Cisco IOS XE software. Cisco has stated that the web-based user interface should never be accessible through the public internet, yet research indicates that a large number of Cisco devices have been exploited by an unknown threat actor.
This critical vulnerability is being tracked as CVE-2023-20198 and is currently undergoing investigation for active exploitation. At the original time of publication, there was no software patch available for affected devices with vulnerable systems exposed to the internet or to untrusted networks, but Cisco released a software update for version 17.9.4a on October 25, 2023, with forthcoming updates for versions 17.6, 17.3, and 16.12.
What is CVE-2023-20198?
CVE-2023-20198 is a critical, unpatched vulnerability impacting Internet-facing IOS XE systems. The web UI provides a graphical management system for networking deployment on Cisco devices, such as routers and wireless controllers. All Cisco networking devices running the IOS XE service with the web user interface feature enabled are at risk of the web UI privilege escalation vulnerability.
"This vulnerability allows a remote, unauthenticated attacker to create an account on an affected system with privilege level 15 access. The attacker can then use that account to gain control of the affected system," reported in the Cisco security advisory.
If successfully exploited, this vulnerability enables unauthorized attackers to create new accounts with full administrator privileges through a privilege escalation issue. The unauthorized administrator accounts are persistent, which means they remain in the system even if the device is restarted.
Cisco, in the Talos Intelligence report, identified initial privilege escalation with unauthorized administrator accounts that later deployed a configuration file and exploited the previously patched CVE-2021-1435. The attacker can leverage this implant to achieve arbitrary command execution if the implant is successfully installed. The web server must be restarted for the implant to function. With heightened administrator privileges and the potential to achieve arbitrary code execution, an attacker could gain control over the system.
Cisco's PSIRT advisory sets a critical CVSS score of 10. The vulnerability is still undergoing analysis in the National Vulnerability Database and does not yet highlight which common weakness enumerations (CWEs) are present in the vulnerability.
This vulnerability has been added to CISA's Known Exploited Vulnerabilities catalog. US federal agencies impacted by this vulnerability must adhere to the requirements of CISA's Binding Operational Directive 23-02.
CVE-2023-20198 follows an existing input validation and injection attack vulnerability identified in September 2023 impacting the same software. Cisco has released software updates for the September vulnerability, which is tracked as CVE-2023-20231.
How to Detect Cisco IOS XE Software Web UI with UpGuard
If you use the IOS XE software with an internet-facing administrative management portal, your system may be at risk.
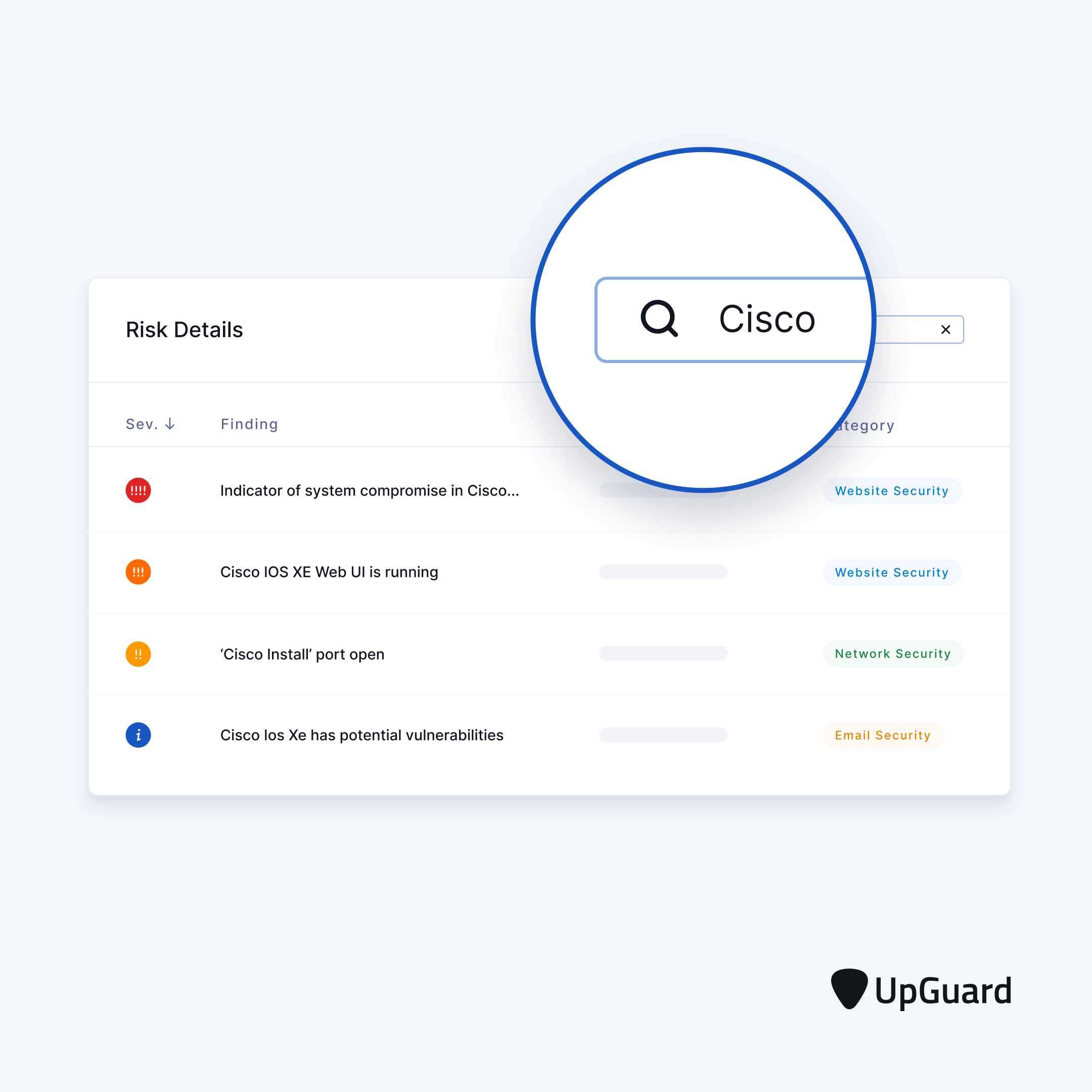
UpGuard has added the following risk detection findings related to CVE-2023-20198:
- Known exploited vulnerability for CVE-2023-20198
- Cisco IOS XE Web UI is running
- Indicator of system compromise in Cisco IOS XE Web UI
By adding these three risks to our scanning capabilities, UpGuard can notify users of potential exposure in your attack surface resulting from your use of Cisco IOS XE Software Web UI and the current vulnerability. You can review your risk profile within UpGuard to identify whether you or a vendor are using Cisco IOS XE Software Web UI exposed to the internet.
If you receive any of these risk findings, you should take immediate action to set up protections against potential compromise as this vulnerability is being actively exploited.
Recommended Mitigations
Cisco advises customers to upgrade the system to a fixed software release. The update for version 17.9.4 has been released, with more versions to follow in the near future. Per the Cisco security advisory, you should immediately disable the HTTP Server feature if it is currently in use.
Consult with your security team and follow your cybersecurity incident response plan as you work to mitigate potential security impacts and protect against potential malicious activity resulting from this vulnerability.
Disable the HTTP Server Feature
To disable the HTTP Server feature, determine whether the feature is enabled by running this command in your terminal:
[.rt-script]show running-config | include ip http server|secure|active[.rt-script]
If your command-line terminal returns the [.rt-script]ip http server[.rt-script] command or the [.rt-script]ip http secure-server[.rt-script] command, then your system is affected. One or both commands indicates that the web UI is enabled on your system.
Note that if you are able to access the web-based user interface, your system is likely affected by this vulnerability.
Cisco recommends using the [.rt-script]no ip http server[.rt-script] or [.rt-script]no ip http secure-server[.rt-script] commands in global configuration mode to disable the web interface. If both are in use, both commands are required to disable the feature.
If you run services that require continued access, restrict those services to trusted networks while you evaluate whether your system has been exploited.
Check for Indicators of Compromise
Cisco's PSIRT advisory includes actionable commands to identify potential compromise and access control issues among Cisco devices on your system. Review the following indicators of compromise (IOCs) on your internet-facing systems.
Inspect administrative users for any unauthorized or newly created users. Threat actors have used [.rt-script]cisco_tac_admin[.rt-script] and [.rt-script]cisco_support[.rt-script] for local user accounts in an attempt to evade detection.
In addition to reviewing administrator accounts, Cisco recommends checking system logs for evidence of any configured, local user unknown to your network administrator. Review the user in the following two log messages for instances of compromise:
- [.rt-script]%SYS-5-CONFIG_P: Configured programmatically by process SEP_webui_wsma_http from console as user on line[.rt-script]
- [.rt-script]%SEC_LOGIN-5-WEBLOGIN_SUCCESS: Login Success [user: user] [Source: source_IP_address] at 03:42:13 UTC Wed Oct 11 2023[.rt-script]
Compromised users may include [.rt-script]cisco_tac_admin[.rt-script], [.rt-script]cisco_support[.rt-script], or any unknown local user. Investigate any new or unknown usernames that appear.
Because file implantation by threat actors has been identified in compromised systems, you can also review system logs for any unexpected filename installation in the following message:
[.rt-script]%WEBUI-6-INSTALL_OPERATION_INFO: User: username, Install Operation: ADD filename[.rt-script]
Additionally, Cisco Talos recommends assessing whether the impact is present on your system by running the following command (replacing systemip with the IP address for the system you want to check):
[.rt-script]curl -k -X POST "https://systemip/webui/logoutconfirm.html?logon_hash=1"[.rt-script]
Cisco advises that the implant is present on the system if the request returns a hexadecimal string.
If you cannot find the aforementioned indicators of compromise, evidence of the malicious implant may have been hidden following the news of the vulnerability. Fox IT has released a supplemental script to investigate the implant’s presence through a fingerprinting method. As with all scripts from external organizations, review your security measures before running new code.






