Vendor Risk Management: Strategies for Protecting Your Business
Vendor Risk Management (VRM) is the process of managing and monitoring security risks resulting from third-party vendors, IT suppliers, and cloud solutions. VRM programs combine continuous third-party attack surface monitoring, risk assessments, and other third-party risk management initiatives to mitigate business disruptions caused by third-party security risks.
As businesses increase their use of outsourcing, the risk of cyber-attacks and data breaches from third-party vendors must be identified and mitigated. While outsourcing has great benefits, if vendors lack strong security controls, your organization is exposed to operational, regulatory, financial, and reputational risk.
Why is vendor risk management important?
Vendor risk management is important because vendors can significantly impact your security posture. If not properly vetted, a newly onboarded third-party service may contain exploitable vulnerabilities, making it highly susceptible to data breaches.
Since many vendors require access to your internal processes, a threat actor exploiting a vendor’s weak cybersecurity could gain access to your sensitive data. Once a vendor is onboarded, their security risks become your security risks. A robust Vendor Risk Management (VRM) program gives organizations complete visibility into their third-party risk exposure, enabling them to make informed decisions about which vendor relationships are safe and which are best to avoid.
The unseen threat: Third-party breaches
In the modern business landscape, outsourcing is a necessity, but it simultaneously increases the risk of cyber attacks and data breaches. A myopic focus on operational risk factors, such as performance and quality standards, is no longer sufficient; increasingly, the biggest risks from third-party vendors are reputational and financial risks, including data breaches.
If a newly onboarded third-party service hasn't been properly vetted, it may contain exploitable vulnerabilities. Since many vendors require access to internal processes, a threat actor exploiting a vendor’s weak cybersecurity could gain access to your sensitive data.
Case study 1: The high-cost vendor failure
One of the most famous examples of third-party risk materializing was the 2013 Target data breach. This massive incident began not with Target's own network, but with a third-party HVAC vendor. The attackers gained access to Target's network credentials through the unsecured HVAC vendor's system, ultimately allowing them to pivot and steal the data of over 40 million customers.
The financial and reputational fallout was staggering:
- Financial impact: The breach cost Target hundreds of millions of dollars in fines, legal fees, and settlement costs. The cost of legal issues, such as lawsuits and class actions, is an example of the risk that vendors can pose.
- Reputational damage: The CEO stepped down, and the company's reputation was severely damaged, highlighting that a vendor's poor security practices can pose a significant risk, regardless of how robust your internal security controls are.
This incident reinforced the notion that a company is legally liable for data breaches that occur within its supply chain, underscoring the importance of rigorous vendor assessments and continuous monitoring. Legal or compliance breaches are a significant risk, particularly for companies in the government or financial services sectors.
Case study 2: Operational resilience in action
In a more recent, high-profile incident, a sophisticated supply chain attack targeted a universal software provider (often referred to as a "fourth party" or sub-processor of many companies). Thousands of organizations that used the provider were technically compromised.
The difference in outcomes among victim companies was determined by their VRM maturity:
- Effective VRM response: Companies with advanced VRM programs were able to:
- Rapidly identify and isolate: Their up-to-date inventory of all third-party vendors, combined with continuous monitoring systems, flagged the compromised vendor immediately.
- Execute contingency plans: They had clear action steps for scenarios where a vendor falls below acceptable standards, allowing security teams to quickly revoke access and isolate the threat.
- Maintain compliance: Because their risk management policies extend to third-party vendors, outsourcers, and contractors (as mandated by regulations like SOX, PCI DSS, and HIPAA), they were able to demonstrate due diligence to regulators and mitigate compliance breaches.
This demonstrates that a strong VRM plan streamlines third-party security risk management, expediting remediation processes and reducing negative impacts on security postures.
What are the benefits of vendor risk management?
A good vendor risk management program will ensure that:
- Addressing future risks takes less time and fewer resources
- Accountability for both the company and vendor is understood
- The quality of your services isn't damaged
- Costs are reduced where possible
- Availability of your services is improved
- You can focus on your core business function
- Operational and financial efficiencies are secured
- Third-party security risks are reduced as long as everyone follows the plan
Even if your organization has a high-risk tolerance, regulations such as the Sarbanes-Oxley Act (SOX), Payment Card Industry Data Security Standard (PCI DSS), and the Health Information Portability and Accountability Act (HIPAA) mandate that risk management policies extend to third-party vendors, outsourcers, contractors and consultants.
Learn about the top VRM solution options on the market >
What is vendor relationship management?
When assessing a vendor, it's important to understand how the vendor fits into the overall context of your organization's projects and goals. Third-party relationships can range from a small one-off project with an independent contractor to an ongoing vendor relationship with a large multinational. Common vendor scenarios include:
- An original equipment manufacturer (OEM) who sells something your organizations needs, like a printed circuit board (PCB), to a computer manufacturer.
- A marketing freelancer sells her services to your company on a one-time or ongoing basis (leading to an ongoing vendor relationship).
- A Software-as-a-Service (SaaS) provider who sells software to your organization for a period of time.
Vendor relationship management is focused on overseeing the relationship with vendors, from due diligence and cyber security risk assessment through the delivery of the good or service onto planning for business continuity. The person who oversees vendor relationships is often called a vendor manager. Vendor managers can sit in any part of an organization, from human resources to the supply chain.
The due diligence process is streamlined if the vendor hosts its security documentation on a tool like Trust Exchange. To start simplifying your Vendor Risk Management process, you can sign up to Trust Exchange for free.
For an overview of the tool, watch this video:
What are third-party vendors?
A third-party vendor is an external party that provides a product or service to your organization. Their connections to your internal technologies and processes make them extensions of your attack surface, ultimately increasing your likelihood of suffering a data breach.
Common third parties include:
- Manufacturers and suppliers (everything from PCBs to groceries)
- Services providers, including cleaners, paper shredding, consultants and advisors
- Short and long-term contractors. It's important you need to manage short and long-term contractors to the same standard and assess the information that they have access to.
- Any external staff. It's important to understand that understanding of cyber risk can be widely different depending on the external staff.
- Contracts of any length can pose a risk to your organization, and the Internal Revenue Service (IRS) has regulations about vendor and third-party relationships that go beyond specific time frames, so even the length of a contract can pose risk. In the IRS's eyes, a vendor working onsite with a company email address for longer than a specific period of time should be classified as an employee and receive benefits.

Why you need to manage your vendor risks
Companies face a host of risks when they engage third parties. Vendors who handle confidential, sensitive, proprietary or classified information on your behalf are especially risky. If your third-party vendors have poor security practices, they can pose a huge risk regardless of how good your internal security controls are.
A myopic focus on operational risk factors like performance, quality standards, KPIs and SLAs is not enough. Increasingly, the biggest risks that come from third-party vendors are reputational and financial risks like data breaches.
Here's a sample of the risk that vendors can pose:
- Legal or compliance breaches, especially if you work in government, financial services or a military contractor
- Breach of the Health Insurance Portability and Accountability Act (HIPAA) that require protected health information (PHI) to be secured correctly
- Legal issues like lawsuits, class actions, loss of work or termination of relationships
- Information security and data security risks. You need to know how much information a vendor should have access to and has access to.
- Loss of intellectual property. If a vendor has access to proprietary information, there is a risk they steal it for themselves or expose it through a data breach
- Relaxed restrictions with long-term vendors can be a big risk, it's important for controls to be as rigorous five years in as on the first day
One key way to reduce risk is to only give vendors access to what data they need to get their job done and no more.
That said, to really reduce risk, organizations need to have an overall risk management strategy which means vendors are constantly measured and evaluated. It's not enough to have subject matter experts who own their vendors. Data breaches can come from any part of your organization.
Without organizational wide practices, departments can pick their own metrics to measure and ad hoc requirements that can result in substandard risk management.
Learn why VRM is particularly critical for businesses in India >
What is vendor lifecycle management?
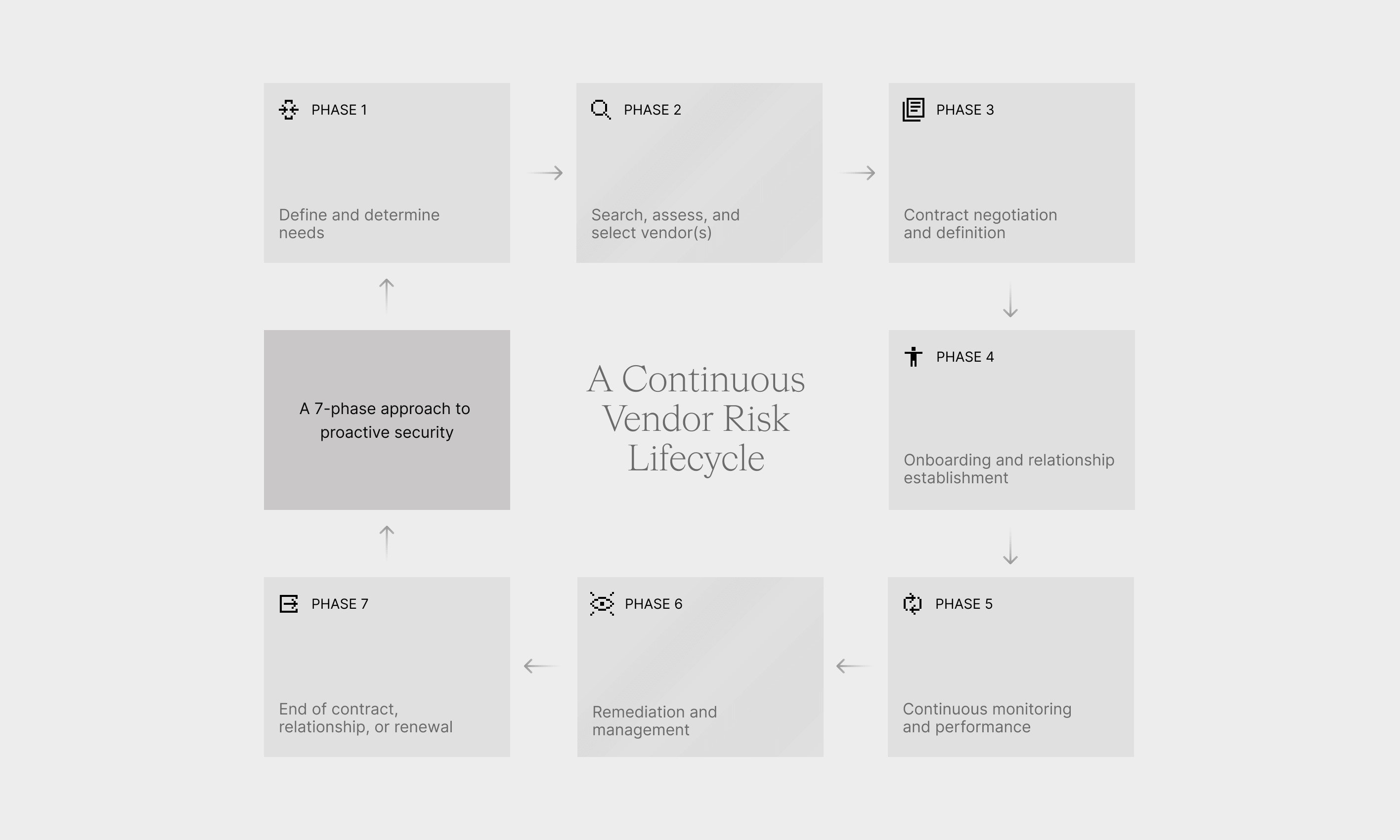
The relationship with a vendor is a continuous cycle, not a one-time transaction. Therefore, Vendor Risk Management (VRM) must also be a continuous, ongoing process. Transitioning from a linear vendor lifecycle style of risk management to an ongoing model is crucial for streamlining the management of vendor partnerships.
The general lifecycle of a vendor relationship starts with defining needs and ends with termination or renewal. The continuous VRM lifecycle integrates risk management activities—from initial due diligence to final offboarding—into these seven key stages.
Phase 1: Define and determine needs
The process begins by clearly defining the business need and the scope of the vendor relationship. It’s important to understand how the vendor fits into the overall context of your organization's projects and goals.
Phase 2: Search, assess, and select vendor(s)
This phase focuses on identifying potential vendors and vetting them for risk.
- Create vendor assessments: Define the criteria for evaluating all vendors.
- Due diligence: The due diligence process is critical as it has a significant impact on an organization's security posture. This is where the vendor's security documentation (e.g., certifications) should be reviewed.
- Select vendor(s): Choose the most suitable vendor based on the risk assessment and business need.
Phase 3: Contract negotiation and definition
Contract terms and timeframes are defined in this stage.
- Define contract terms: Contracts should outline what security controls and requirements the supplier has in place.
- Right to audit: Ensure your contracts include the "right to audit" clause.
Phase 4: Onboarding and relationship establishment
Vendor onboarding is one of the most delicate phases of a VRM program. Poor onboarding practices will overlook different types of risks and security vulnerabilities, adding them to your risk profile. Proper onboarding requires a thorough assessment of cyber threats and other risks, such as compliance requirements, that are unique to each type of vendor.
Phase 5: Continuous monitoring and performance
Vendor risk management is never “set-and-forget”. New vulnerabilities emerge daily, and vendors’ security postures can change over time. This phase focuses on monitoring the relationship and performance.
- Monitor risk exposures: Outline how vendor risk monitoring will occur, when it will occur, how reviews and feedback will be conducted, and how risk exposures will be identified and mitigated.
- Assess compliance: It is vital to consistently assess each vendor’s compliance throughout the vendor lifecycle, as an organization remains liable for its data even if a breach occurs within its supply chain.
Phase 6: Remediation and management
This phase involves addressing any risks identified during the monitoring phase. A VRM plan should aim to streamline third-party security risk management, thereby expediting remediation processes and reducing negative impacts on security postures. Advanced techniques, such as vendor tiering, are very effective at improving remediation efficiency.
Phase 7: End of contract, relationship, or renewal
The relationship must be managed through its conclusion.
- Offboarding: For high-risk vendors, steps may even result in early termination of a contract.
- Data control: Crucially, only give vendors access to the data they need to complete their tasks and no more. Make sure the secure revocation of all access and the return or destruction of data occurs during the offboarding process.
Learn how to get vendor questionnaires completed faster >
Building a robust vendor risk management framework
A comprehensive Vendor Risk Management Plan is the organization-wide initiative that outlines the behaviors, access, and service levels a company and its vendors agree upon. The VRM Framework is the underlying policy structure that makes certain the plan is applied consistently and effectively across all third-party relationships.
The core principle of an effective framework is applying the same criteria to all vendors, adapted to the specific risks associated with the products or services they provide. Without organization-wide practices, departments may select ad hoc requirements that result in substandard risk management.
Step-by-step guide: Creating your VRM framework and plan
Step 1: Inventory, classify, and tier all vendors
Before you can manage risk, you must know what you're managing.
Depending on the vendor and services provided, the relationship may be spelled out step by step with Vendor Risk Management checklists or in a more casual manner.
- Maintain an up-to-date inventory of all third-party vendors.
- Assess and segment vendors by potential risk. This process, known as vendor tiering, categorizes vendors based on two main factors:
- Data sensitivity: Do they handle confidential, sensitive, proprietary, or classified information? (e.g., PHI, PII, intellectual property).
- Business criticality: How important is the service to your core business function?
- Prioritize your high-risk vendors to ensure your information security team invests the most resources in higher-risk relationships.
Step 2: Define risk appetite and acceptance
Establish clear, standardized criteria to assess future vendors in real time.
- Establish a formal risk appetite: A defined level of risk that your organization is willing to tolerate.
- Develop a rule-based system for vendor evaluation: This ensures consistency, for example, by requiring all Tier 1 vendors to provide a SOC 2 Type II report.
Step 3: Formalize the assessment process
The document should outline how your organization tests and gains assurance of vendor performance.
- Ask for references from the vendor's other clients.
- Determine that the vendor is financially solvent.
- Verify they have liability insurance.
- Review security controls by determing whether the vendor has proper security controls, technology, and expertise to properly manage your sensitive information.
- Verify licensing and training, if you operate in a regulated industry, make sure that they possess the necessary licenses and training (e.g., HIPAA training or security clearance).
Step 4: Define contractual security requirements
Poor vendor risk management can result in a contract that doesn't adequately protect your organization.
- Outline security requirements: Detail what security controls and requirements the supplier must have in place.
- Breach protection: Outline how the vendor will ensure your organization's regulatory compliance and prevent customer data exposure in the event of a security breach.
- Review the contract: Go over terms, renewals, required service levels, and termination requirements.
Step 5: Establish governance and accountability
An effective plan requires the cooperation of multiple departments, including compliance, internal audit, HR, and legal teams. This starts by assigning an owner for vendor risk management and defining three lines of defense:
- First line: Functions that own and manage risk (e.g., the department that hired the vendor).
- Second line: Functions that oversee or specialize in risk management and compliance (e.g., the VRM team).
- Third line: Functions that provide independent assurance, typically internal audit.
Read our guide on how to select a third-party risk management framework.
Step 6: Continuous monitoring and reporting
It's not enough to have subject matter experts who own their vendors; a successful strategy means vendors are constantly measured and evaluated.
- Outline how vendor risk monitoring will occur and how reviews and feedback will be conducted.
- Practice continuous monitoring: Ongoing assessments and continuous monitoring help your security team detect and address third-party risks before they escalate.
- Provide an overview of critical third-party security risk exposures in Vendor Risk Management reports for senior management.
Learn how to implement TPRM into an existing security framework.
This ongoing monitoring model is optimized to keep stakeholders informed of an organization’s vendor risk management efforts. And the emphasis on continuous monitoring helps regulated industries, such as those in healthcare, rapidly identify and address emerging risks impacting regulatory compliance. If the vendor risk visibility component of your VRM program requires development, refer to this post ranking the top vendor risk monitoring solutions on the market.
For an illustration of this framework being implemented in a Vendor Risk Management workflow, watch this video:
What is a Vendor Risk Management Maturity Model (VRMMM)?
A vendor risk management maturity model (VRMMM) is a holistic tool for evaluating maturity of third-party risk management programs including cybersecurity, information technology, data security and business resiliency controls.
A VRMMM allows organizations to develop a strategy before building out a program and to identify where and how goals will be set to make the program robust.
Any VRMMM must have two important parts:
- A way to identify and evaluate needs and potential risks
- A way to measure the relative development of maturity in components of the overall risk management framework, such as determining how each department is managing risks, where resources need to be moved and how improvements can be made
What are the vendor risk management maturity levels?
There are six levels of a vendor risk management maturity model:
- Startup or no third-party risk management: new organizations beginning operations or organizations with no existing vendor risk management activities.
- Initial vision and ad hoc activity: third-party risk management activities performed on an ad hoc basis and considering how to best structure third-party risk activities.
- Approved road map and ad hoc activity: Management has approved a plan to structure activity as part of an effort to achieve full implementation.
- Defined and established: Organizations with fully defined, approved and established risk management activities where activities are not fully operationalized with metrics and enforcement lacking.
- Fully implemented and operational: Organizations where vendor risk management activities are fully operationalized with compliance measures, including reporting and independent oversight - to understand how to apply VRM to different vendor risk contexts, refer to this list of Vendor Risk Management examples.
- Continuous improvement: Organizations striving for operational excellence with clear understanding of best-in-class performance levels and how to implement program changes to continuously improve the process.
Understanding where your organization's vendor risk management maturity level is a key part of understanding how to best manage vendor risk and where you can improve.
How to create a third-party or vendor risk management checklist
When your organization is preparing to hire or onboard a new vendor, you need to work through a due diligence checklist to ensure they are fit. This is also known as a vendor assessment.
The critical parts to a vendor assessment are as follows:
- Ask for references from the vendor's other clients.
- Determine that the vendor is financially solvent, you may need to request financial statements.
- Verify they have liability insurance.
- If you operate in an industry with regulatory requirements, verify that they have the correct licensing and training, such as HIPAA training, security clearance or financial licence to provide the service.
- Conduct background and criminal checks.
- Assess whether the vendor will be able to meet your required service levels.
- Determine whether the vendor has proper security controls, technology and expertise to properly manage your sensitive information.
- Review the contract, including terms, renewals, required service levels, and termination requirements.
- Provide an overview of critical third-party security risk exposures in Vendor Risk Management reports for senior management.
For inspiration, refer to this VRM checklist for CISOs and this generic VRM checklist.
Read our full guide on how to use a vendor risk management checklist here.
Vendor risk management best practices in 2025 and beyond
Vendor risk management is continually evolving, demanding a shift from reactive security checks to proactive, continuous defense.
In 2025, the best practices center on automation, visibility into the extended supply chain, and integrating risk into the full vendor lifecycle.
Learn more on our vendor risk management assessment matrix here.
Modern best practices for VRM
Learn how UpGuard helped Schrödinger shave hours from its vendor security program by eradicating spreadsheets.
Read the case study >
Breaches by vendors are almost always caused by failure to enforce already existing rules and protocols. You and your vendors need to be transparent about what you expect from each other and what risks are posed.
Read more about vendor risk management best practices >
Emerging trends and technologies
The future of VRM is driven by technologies that offer efficiency, scale, and deeper visibility into the entire supply chain.
The extended attack surface: Fourth-party risk
It's no longer simple enough to ensure your organization's systems are secure; your risk management program must address third and even fourth-party risk.
- Identifying the supply chain attack surface: Include both third-party and fourth-party vendors in your VRM program.
- Automation for discovery: Manual inventories are prone to inaccuracies and make it difficult to discover fourth parties. An automated VRM solution centralizes vendor tracking and enables the automatic discovery of fourth-party relationships.
Automation and scalability with GRC solutions
Organizations striving for operational excellence leverage technology to support VRM scalability by automating vendor risk management.
- Move beyond spreadsheets: Ensure your VRM program is supported by scalable processes by leveraging dashboards, GRC software, or automation-focused questionnaire managers—instead of manual tasks like spreadsheets.
- AI-powered due diligence: The use of AI to streamline the VRM process—from instantly assessing a prospective vendor's cybersecurity efforts with external attack surface scans to automating questionnaire analysis—is becoming standard.
Integrating security ratings and external data
Objective, outside-in data provides a continuous risk signal, complementing point-in-time assessments.
- External attack surface scans: Quickly quantify a prospective vendor's security posture.
- Data leak detection: Utilize proprietary data leak detection engines to identify sensitive data leaks on both the surface and dark web.
How to address a vendor breach
While comprehensive VRM reduces the likelihood of an event, vendors can still be targeted by cybercriminals or accidentally leak confidential information due to poor configuration.
By having and following a vendor risk management framework, your organization will be able to act quickly and follow a protocol if a vendor breach does occur. This can include anything from having your vendor pay the financial damages to terminating the contract.
Watch the video below to learn how UpGuard leverages AI to streamline Vendor Risk Management.