Your Password Was Exposed in a Non-Google Data Breach: How to Respond
If you’re a Google Chrome user, you may have received the pop-up alert “Your password was exposed in a non-Google data breach” in your web browser. The alert informs users of any recent security breaches which may have compromised their account passwords.
Follow this quick 3-step guide to to secure your Google account and your personal data.
Step 1: Use Password Checkup to See which Password was Compromised
The very first thing you should do is to check the security status of all your saved password in Google’s Password Manager. This feature
Follow this process:
If you have any compromised passwords, you will see a message like this (it will also show the number of passwords that have been compromised):
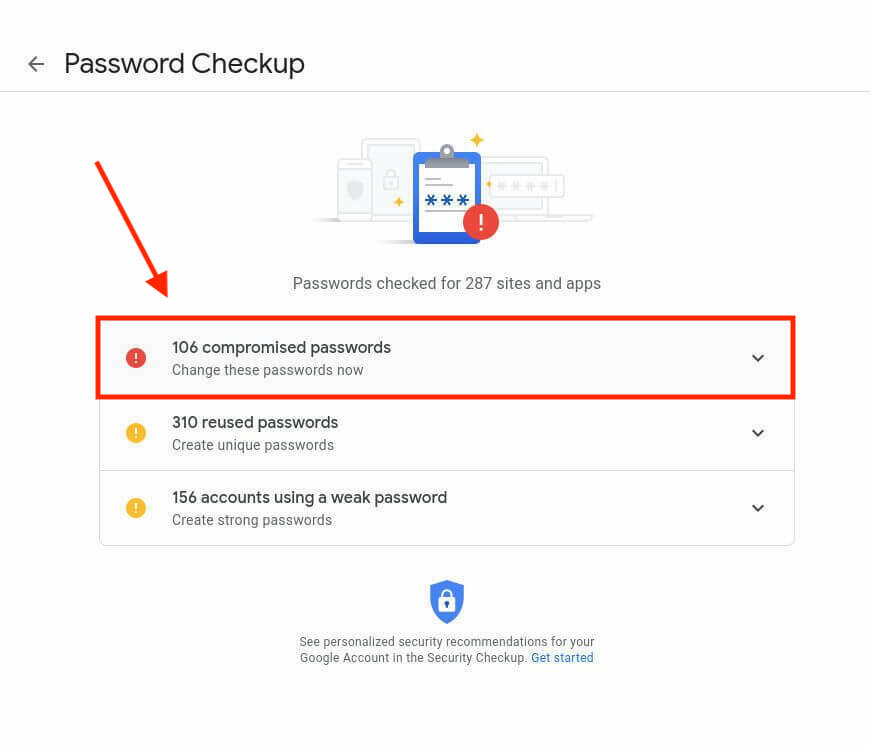
- Click the drop-down to see all of your comprised passwords.

- Click the Check Passwords button on the Password Checkup page.
Step 2: Immediately Update all Compromised Passwords
Click ‘Change Password’ for all compromised passwords. When you click this button, you will be directed to the website associated with that account.
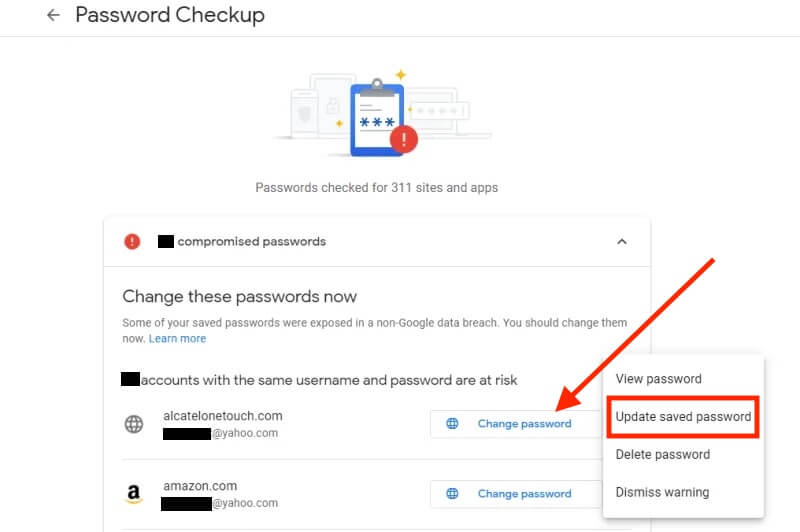
Log into the website that loads and immediately change your password. Make sure you choose a strong password to maximize cybersecurity.
Once updated, click the Check Remaining Passwords button to return to your compromised passwords list in Google’s password manager.
Continue until all compromised passwords have been updated.
Step 3: Update all Weak and Reused Passwords
Weak and reused passwords put you at a very high risk of getting compromised in a data breach. Even if a strong password is reused, if it was involved in a previous data breach, cybercriminals could find it on the dark web and compromise all of the accounts that use it.
Follow the same process in step 2 to update all weak and resued passwords:
- Click on the drop-down arrow.
- Click on Change Password
- Log into the website that loads and create a new password.
- Return to Google’s password checkup page and work down the list.
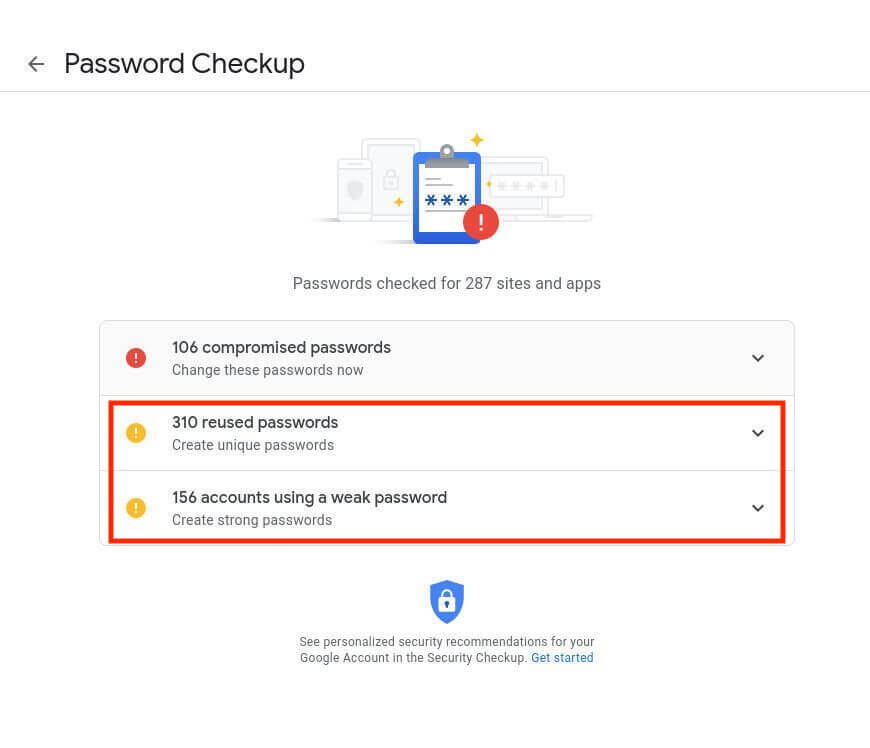
Never reuse passwords. It’s good security practice to always create unique strong passwords for all of your accounts.
Get a free evaluation of your organization's data breach risk, click here to request your instant security score now.
Confirming Compromised Passwords on the Have I been Pwned Website
You can sometimes confirm that a password has been compromised by submitting it in the pwned passwords search engine.
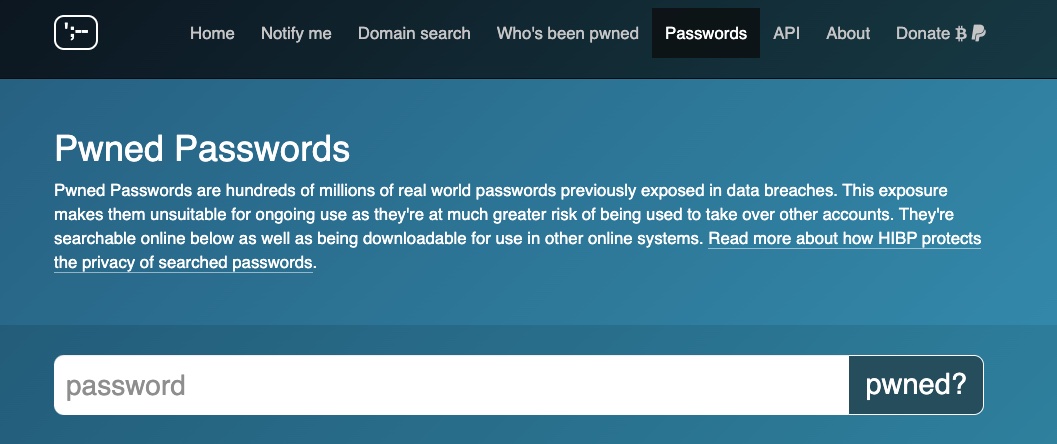
The Have I Been Pwned data breach website compares all search queries against a database of known breaches. However, If a breach associated with your compromised password is very recent, you may not yet be added to the Have I Been Pwned data breach database. If this the case, check again in a few days.
What is Chrome’s Password Checkup Feature?
First introduced as a Chrome extension in February 2019, Chrome’s Password Checkup checks your username and password against over 4 billion credentials that Google has recognized as unsafe. Similar to haveibeenpwned.com, Google identifies Gmail accounts affected by third-party data breaches and accounts where users are re-using their Gmail passwords, to prevent further compromise.
Google released this feature as part of its broader defense in depth strategy that aims to prevent, detect, and mitigate account hijacking caused by third-party data breaches.
You’ll need to access Password Checkup to check if your login credentials are unsafe and take further action.
What Should I Do If My Password Has Been in a Data Breach?
If your password has been exposed in a data breach, you should immediately change the password on all affected accounts. Data breaches often occur as a means of obtaining sensitive information to commit further cybercrimes, such as identity theft or fraud.
Many countries now have data breach notification laws, which means organizations must inform their customers and immediately resolve breaches. Google’s Password Checkup feature ensures you have additional notification of any data breaches which affect your email account.
What is a Data Breach?
A data breach is a high-risk security incident where sensitive data is compromised by an unauthorized individual. The hacker could exploit this data by accessing, copying, transmitting, viewing, or stealing it.
Data breaches commonly involve the exposure of valuable sensitive information, including:
- Financial information, like credit card numbers and bank account details
- Protected health information (PHI)
- Personally identifiable information (PII), including personal info like full names, addresses, phone numbers, and social security numbers
- Trade secrets
- Intellectual property
Cybercriminals can also discover and exploit existing data leaks and cloud leaks to cause data breaches.
Learn about the differences between data breaches and data leaks.
How Do Data Breaches Happen?
Data breaches can occur in a number of different ways – either intentionally or accidentally. There are 8 main causes of a data breach:
1. Exploiting System Vulnerabilities
3. Spyware
4. Phishing
6. Broken or Misconfigured Access Controls
7. Physical Theft
8. Third-Party Vendor Breaches
How to Protect Yourself From Data Breaches
Follow these best practices to improve your chances of avoiding a data breach incident.
1. Secure Your Internet Connection
Hackers can use specialized tools and techniques to intercept internet traffic – this is especially easy to do over public wi-fi networks. Securing your internet connection provides an added layer of protection when sharing sensitive information over the web, which helps prevent data breaches caused by accidentally exposed data.
- Only use HTTPS sites. HTTP sites run on unsecured connections, which means hackers can eavesdrop on all incoming and outgoing traffic. For example, if you make a payment transaction on an HTTP site, a cybercriminal could steal your credit card details effortlessly. You should only browse HTTPS sites, which require SSL certification, enabling encrypted connections and greater data security.
Learn more about HTTPS.
- Use a Virtual Private Network (VPN). A VPN adds an extra layer of protection for internet users by encrypting all sent and received data. VPNs also conceal users’ IP addresses, further anonymizing all incoming and outgoing traffic.
Learn more about VPNs.
2. Use Unique Passwords
Using the same password across multiple accounts has a domino effect in a data breach. If your username and password are compromised via one website, they are also compromised anywhere else that uses the same credentials. Setting different passwords across all your accounts ensures that any security issues will likely remain contained to the first compromised account.
It’s difficult (and unsafe) to manually track all of your passwords to ensure they’re never recycled. The most secure method of keeping all of your passwords strong and unique is with a password manager such as 1Password.
Learn more about how to create a secure password.
3. Turn on Additional Authentication
Many online account services now offer two-factor authentication (2FA) and multi-factor authentication (MFA). They offer extra security by requiring two or more types of authentication before allowing users access to their accounts.
Learn more about two-factor authentication.
4. Educate Yourself
Gaining awareness of common tactics used to compromise is the first line of defense against accidentally exposing your personal information. You can learn about popular attack vectors, like email phishing scams and malware-infected pop-ups, through online tutorials.
Learn more about how to recognize phishing scams.
5. Implement Security Controls
If you own a business, you should be very concerned about the damaging financial impact of data breaches. The following security controls will help you minimize the likelihood of data breaches and, consequently, their associated damage costs.
- Implement a cyber program focused on discovering and mitigating third-party security risks, officially known as Vendor Risk Management.
- Ongoing vulnerability and penetration testing.
- Malware protection.
- A Zero Trust Architecture.
- A Data leak detection solution for both the internal and third-party attack surface.
- Security Awareness training for staff (to prevent successful phishing attacks)
- Use of a Third-Party Risk Management software for a complete attack surface monitoring solution
Get a free evaluation of your organization's data breach risk, click here to request your instant security score now.
Well-Known Examples of Data Breaches

Microsoft
In January 2021, Microsoft Exchange’s email servers were involved in one of the US’ most significant cyberattacks to date. More than 60,000 companies were affected worldwide, 30,000 of which were based in the US. The attackers were able to gain unauthorized access to emails containing sensitive data by exploiting four zero-day vulnerabilities. The email accounts were connected to a range of organizations, including small businesses and local governments. The software flaw allowed the hackers to remain active in the vulnerable systems for three months.

In April 2021, hackers performed an illegal data scrape of LinkedIn’s user base, revealing the personal details of over 700 million users. This exposure enabled additional cybercriminals to take advantage of the breached data. One threat actor reportedly tried selling a set of LinkedIn data on a public forum for $7000 in Bitcoin.

Yahoo
Between 2013 and 2016, Yahoo was hit by several cyber attacks. A team of Russian hackers exploited Yahoo’s database, stealing records containing personal information from about 3 billion user accounts in total. Yahoo’s delayed reaction to the attack and failure to disclose one of the security incidents to its users resulted in a $35 million fine and 41 class-action lawsuits.

Equifax
In September 2017, primary credit reporting agency Equifax reported a significant data breach that compromised the publicly identifiable information (PII) of 148 million US citizens. The breach exposed its victims to financially-motivated crimes, including identity theft and fraud. Equifax eventually faced penalties to the tune of $575 million to be paid to numerous authorities, states and territories due to their poor network security.