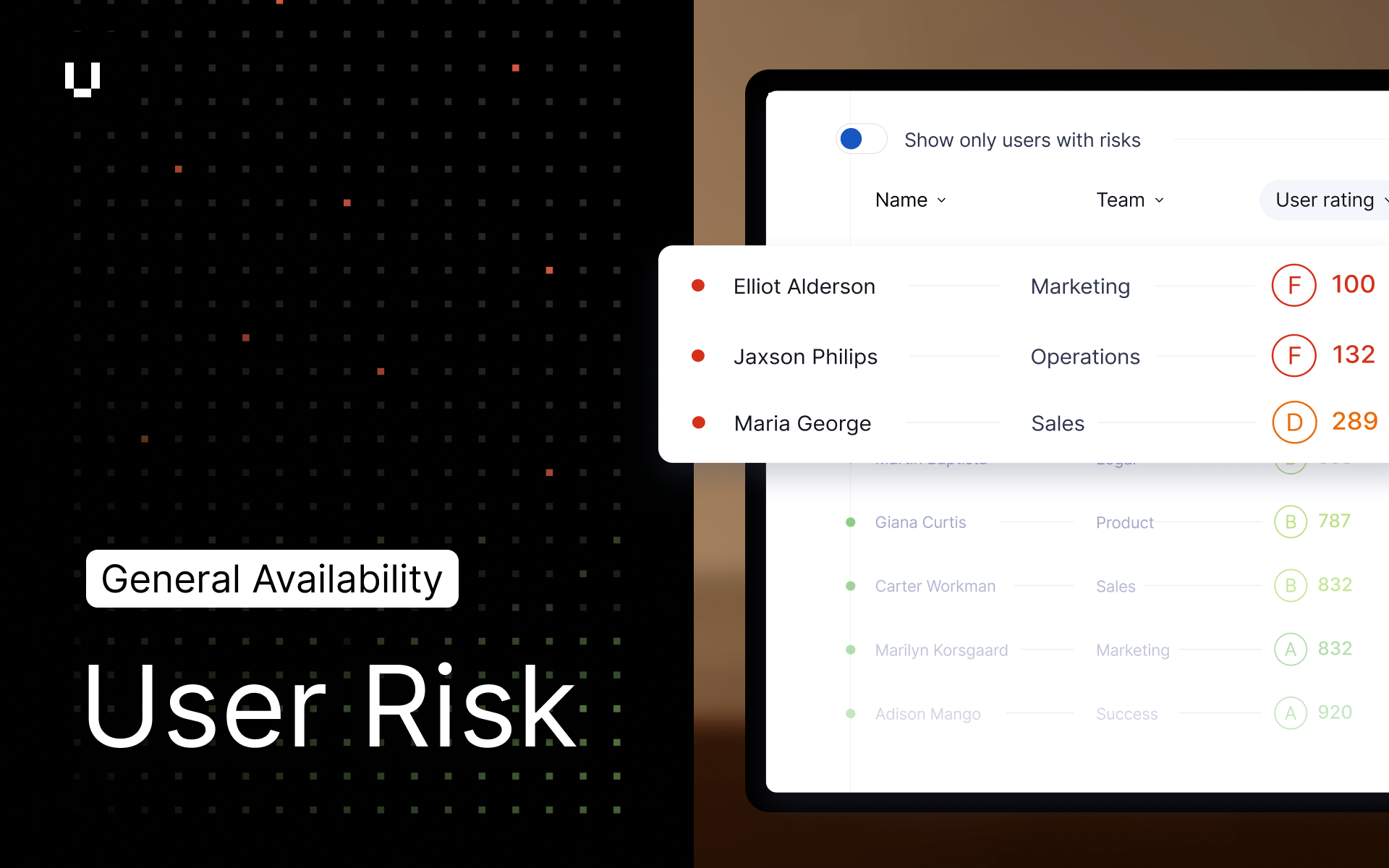
You likely already restrict access to a portion of your UpGuard account to specific users. For example, not every user on your account should have administrative access. But what we’ve heard from you is that as you onboard more users, it gets harder and harder to manage, keep track of, and update the permissions of each user.
That’s why we’re introducing role-based access control. Administrators can now create and manage custom roles, making it easy to ensure each teammate has the right permissions and that your organization is following the principle of least privilege. You can learn more about RBAC and the principle of least privilege on our blog.
Managing roles is as simple as creating a role, configuring your desired permissions, and assigning it to users. If you need to update a role later, any changes will cascade down to the assigned users too.
We also heard that you wanted more granular permissions. That’s why you can now decide whether a user has access to Breach Risk, Vendor Risk, or CyberResearch. This is great for situations where one team manages your attack surface and another separate team manages your vendors.
In addition to these improvements, you can now decide whether a user has read-only or full access to Breach Risk’s or Vendor Risk’s core features, as well as whether a user has access to Identity Breaches and Typosquatting.
Role-based access control is currently in closed beta and only available for certain plans. Please reach out to us if you would like to learn more.
Learn how to create and manage roles.
Label vendor and subsidiary domains, IP addresses, and IP ranges plus support for labelling in tree-view
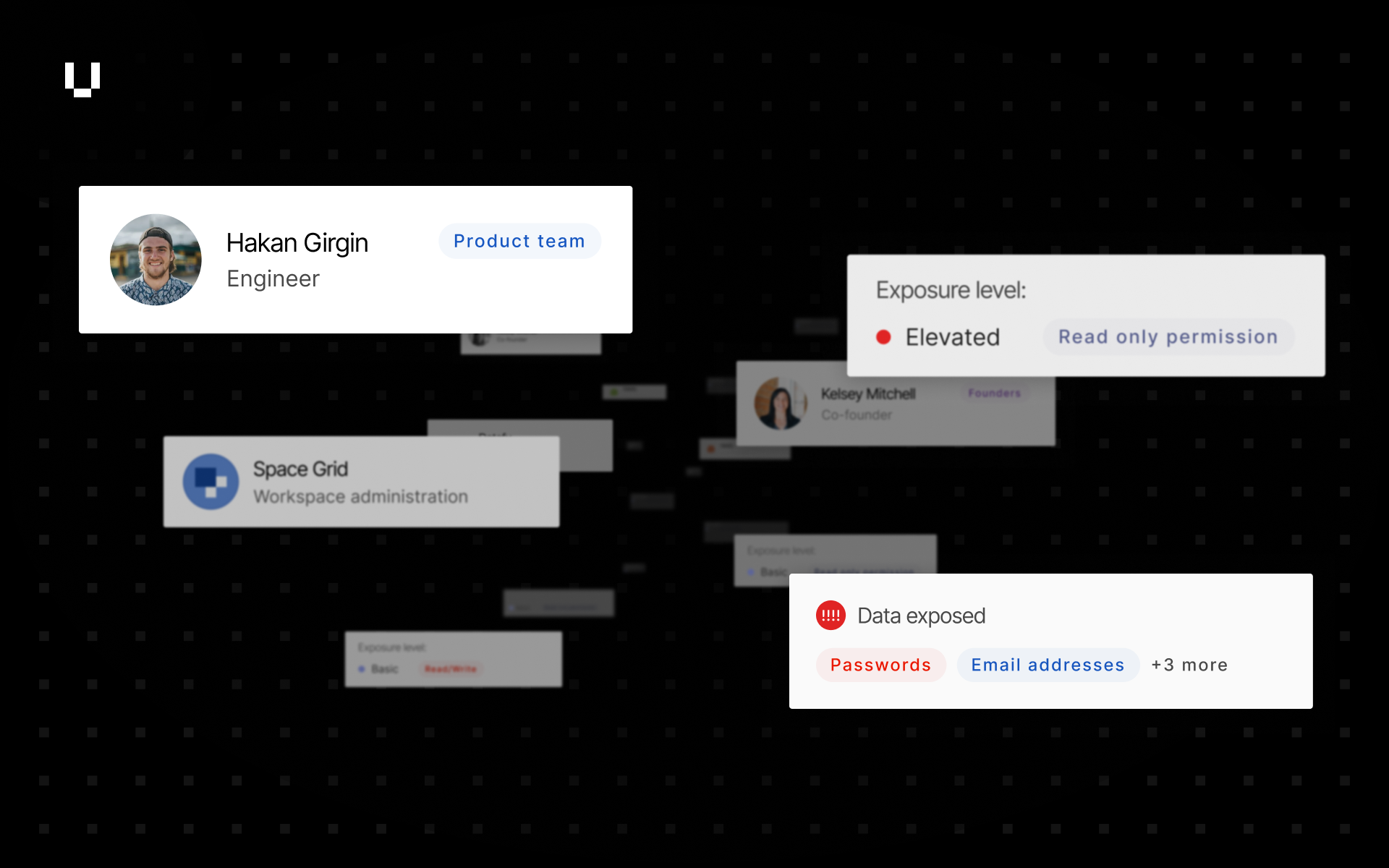
Another frequent bit of feedback we receive is that you want to be able to label your vendor’s or your subsidiary’s domains, IP addresses, and IP ranges so you can drill down into the specific assets that mean something to you. Now you can.
Next time you’re on a vendor’s or subsidiary’s Domains or IP Addresses page, you’ll see an Add label on the far right of the table. Clicking Add label will allow you to add an existing or create a new label. For context, labels in UpGuard are broken down into vendor and assets labels. This means that domain and IP address labels are shared across Breach Risk and Vendor Risk.
As part of these improvements, we’ve refreshed the design of the labels modal, moved the management of labels to Settings under the Labels tab, and added support for labelling domains in tree view across Breach Risk and Vendor Risk.
These improvements make it easier than ever to track your and your vendors’ assets and to keep your team’s labels under control.
Learn how to label your vendor domains, IP addresses, and IP ranges and your subsidiary’s domains, IP addresses and IP ranges as well as how to manage your labels.
Trigger webhook calls from audit log events
Administrators can now push Audit Log events into other platforms using our Integrations feature. For background, Integrations uses webhooks to notify your other applications when an event happens in your account. Examples of these events include when an identity breach or data leak is detected, the score of a watched vendor drops below a threshold, and now any Audit Log event of your choosing.
Learn how to integrate UpGuard with other services.
Other fixes and improvements
- Added an exception for Kubernetes clusters that sit behind AWS Elastic Load Balancing. This means that scores won’t change unexpectedly when Kubernetes stops and starts.
- Fixed bug causing Excel report generation to break for large exports
- Vulnerabilities that have been waived will no longer produce notifications
- Improved design of domain side panel to indicate when a risk is coming from www or the root domain
UpGuard Release Notes
See UpGuard In Action
Free instant security score
How secure is your organization?






.png)