Service Organization Control 2 (SOC 2) is an auditing standard and readiness assessment developed by the American Institute of Certified Public Accountants (AICPA). It is designed to ensure service providers and third-party vendors protect sensitive data and personal information from unauthorized access.
SOC 2 audit reports cover a period (generally 12 months) and include a description of the service organization's system, and test the design and operating effectiveness of key internal controls over a period of time.
Information security and defense-in-depth are important in any organization. The rise of outsourcing key business operations (SaaS companies, their products, and other data center providers) means more third and fourth-party data breaches and data leaks are happening. Additionally, the cost of data breaches and regulatory scrutiny (due to laws like HIPAA and GDPR) has never been higher, necessitating the importance of data security controls.
The purpose of SOC 2 is to provide peace of mind for organizations when they engage third-party vendors. This has led many security-conscious organizations to look for SOC 2 compliance as part of their vendor assessment process to reduce vendor cybersecurity risk.
Why is SOC 2 Compliance Important?
Outsourcing and, in turn, third-party and fourth-party risk have never been higher. Every organization is outsourcing parts of its operations, often to multiple suppliers. Those suppliers are then outsourcing part of their operations to other suppliers.
This is why SOC 2, a Third-Party Risk Management framework, and a Vendor Risk Management program, and general strong security practices are so important. Vendor risk needs to be managed carefully with vendor questionnaires, security ratings, and industry benchmarking. You can read our Third-Party Risk Management buyers guide to learn more.
The most important thing to understand is customers don't care whether data breaches and data leaks are the results of your mismanagement of their data or your vendor's mismanagement. They care that their data was exposed or sold on the dark web. Consider making SOC 2 compliance part of your information security policy and cyber security risk assessment process.
Meeting SOC 2 compliance requirements is one way to determine whether your vendors are implementing secure data protection and data processing protocols. Along with looking for SOC 2 compliance, consider investing in a tool that can automatically monitor your vendors’ security performance and automate security questionnaires. Better yet, look for a tool that is CVE compatible. And look for shared assessments that allow your organization to obtain a detailed report about your service provider's controls and verify that the information in the report is accurate.
Digital forensics isn't always going to give you anything useful, and even if it does, police cyber attacks can be hard due to their distributed nature. It's far better to prevent a data breach than try to clean one up after the fact. As many organizations have found out, once data is exposed, it can prove difficult to recover.
Learn how to prepare for a SOC audit >
What is SOC 2 Compliance? The Trust Services Criteria (TSC)
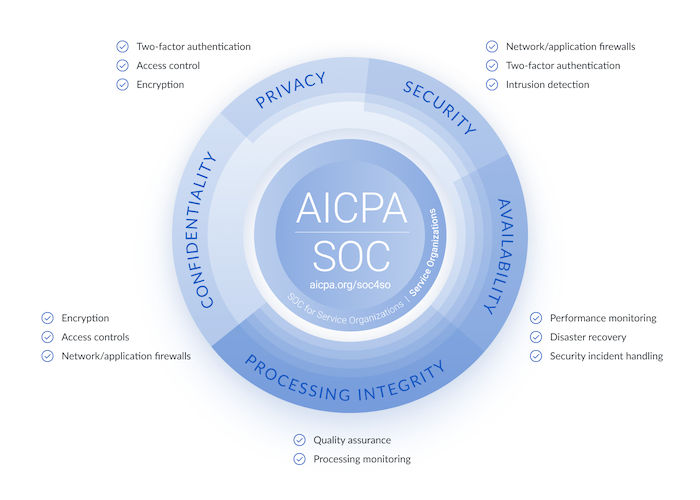
SOC 2 compliance is concerned with how companies manage and store customer data in accordance with AICPA's five Trust Services Criteria (TSC):
- Security: The protection of system resources from unauthorized access. This could include network security, intrusion detection, and other security tools that protect against vulnerabilities, ransomware like WannaCry, and other types of malware. These criteria are concerned with reducing cyber threats and preventing data breaches and cyber attacks.
- Availability: The accessibility of the system, products, or services stipulated in a contract or by service level agreement (SLA). It does not address system functionality and usability but rather security-related criteria that can affect availability.
- Processing integrity: Addresses whether a system achieves its purpose in a complete, valid, accurate, timely, and authorized manner.
- Confidentiality: Addresses whether sensitive data is restricted to specific people or organizations. Encryption, phishing awareness training, SSL certificates, DNSSEC, and preventing man-in-the-middle attacks, domain hijacking, and email spoofing are fundamental to protecting confidentiality.
- Privacy: Addresses the collection, use, retention, disclosure, and disposal of personally identifiable information (PII) and how it aligns with the organization's privacy notice and criteria set out in AICPA's generally accepted privacy principles (GAPP). All PII must be protected from exposure, both accidental and deliberate. Examples of PII data include phone numbers, names, and social security numbers.
Unlike stricter security standards like PCI DSS, SOC reports are unique to each organization. This means organization controls can be designed, in line with specific business practices, to comply with one or more of the trust services principles. These internal reports provide regulators, business partners, suppliers, and your organization with important information about how your service providers manage sensitive data.
Recieving a SOC report isn't the end of your SOC 2 compliance journey. To ensure you get as much value as possible from your SOC 2 investment, it's important to understand the next steps following a SOC 2 audit.
What are the Different SOC Standards?
The American Institute of CPAs (AICPA) has developed three SOC audit standards:
- SOC 1: Evaluates, tests, and reports on the effectiveness of the service organization's internal access controls related to user entities' internal controls over financial reporting. A SOC 1 report is equivalent to a Statement on Standards for Attestation Engagements (SSAE 16) report.
- SOC 2: Evaluates, tests, and reports on the systems and organization controls related to storing information but is not significant to financial reporting or financial controls. SOC 2 was preceded by SAS 70.
- SOC 3: Reports on the same details as a SOC 2 report but is intended for a general audience. They are shorter and do not include the same details as a SOC 2 report but are shared openly, often on a company's website with a seal to indicate compliance.
What are the Different Types of SOC Reports?
There are two types of SOC reports:
- Type I: Describes a vendor's system and organization controls and whether they are suitable to meet relevant criteria.
- Type II: Details the operating effectiveness of the systems outlined in Type I.
A common misconception is to confuse SOC types with SOC standards. Each SOC standard (SOC 1, SOC 2, and SOC 3), can each have a SOC report of Type I or Type II, i.e. SOC 2 Type II.
What is a SOC 2 Certification or Attestation?
A SOC 2 certification is issued by an independent CPA firm and assesses the extent to which a vendor complies with one or more of the five trust principles based on the service organization's controls and processes.
SOC 2 reports consist of the following:
- The opinion letter
- Management's assertion
- Description of the system
- Description of tests of controls and results of testing
- Other information
How UpGuard Helps Organizations Stay SOC 2 Compliant
UpGuard can help organizations and businesses stay SOC 2 compliant by helping them focus on data security using our industry-leading attack surface monitoring and vendor risk management software. SOC 2 security principles have a heavy focus into preventing unauthorized used of digital assets and data and requires organizations to implement access controls to prevent cyber threats, malicious attacks, data theft, data leaks, and the intentional misuse or disclosure of company information.
Additionally, UpGuard has customizable questionnaire templates that organizations can tailor to their vendors to properly assess security postures to stay SOC 2 compliant. The entire questionnaire process is automated to ensure an efficient and effective workflow.




