Update 9/26/25: TechCrunch has received additional comment from a company claiming responsibility. Read more there for ongoing coverage.
UpGuard can now disclose the discovery of a public Amazon S3 storage bucket containing over 273,000 recent documents detailing bank transfers in India. Each file documented a single transaction, revealing unredacted bank account numbers, transaction amounts, and in many of the files, relevant individuals’ names, phone numbers and email addresses. The exposed dataset affected accounts at dozens of Indian banks and financial institutions, as well as thousands of individuals, with thousands of new documents added to the storage repository each day.
Background
In 2016, Indian banks began adopting a clearing service called NACH (National Automated Clearing House) in order to “consolidat[e] all regional ECS systems into one national payment system, thereby removing any geographical barriers in efficient banking.” In 2025, most Indian banks utilize NACH and process transactions using their service.
NACH is used for “making bulk transactions towards distribution of subsidies, dividends, interest, salary, pension etc. and also for bulk transactions towards collection of payments pertaining to telephone, electricity, water, loans, investments in mutual funds, insurance premium etc.” The exposed PDFs discovered in the cloud bucket were all formatted identically, presumably to document such transactions according to the NACH specifications.
Timeline
- August 26th: UpGuard researchers discovered a publicly accessible Amazon S3 cloud storage bucket containing approximately 273,000 PDF documents. UpGuard analyzed the documents and determined they were highly sensitive.
- August 27th: Notified AYEFin, the most represented entity, at corporate@ayefin.com.
- August 28th: Again notified AYEFin, this time at ombudsman@ayefin.com and customer.care@ayefin.com and received an automated customer support message.
- August 29th: Notified NCPI, the organization responsible for NACH, to which all exposed documents were relevant.
- September 2nd: After seeing that the file contents were growing daily, UpGuard escalated to CERT-IN, a government agency responsible for addressing cyber security incidents, and received an automated response.
- September 4th: UpGuard researchers verified that the exposed bucket had been secured.
- September 17th: UpGuard added incident to exclusive threat feed.
- September 24th: UpGuard received a response from NPCI that the data leak was not from their systems.
Data Statistics
To analyze the data, UpGuard downloaded 55K files, a sample of about 20% of the total data set. After notifying AYEFin, UpGuard continued to monitor the bucket. By repeatedly listing the bucket contents, we learned that about three thousand files were being added per day. After parsing the PDFs, we identified thirty-eight financial institutions in our sample as either the debtor or creditor of a transaction.
- 273,160 total files (UpGuard sample: 55K)
- 210GB total size (UpGuard sample: 42GB)
- 38 affected banks discovered in sample
- April 10, 2025 earliest document creation data
- ~3,000 new files added every day
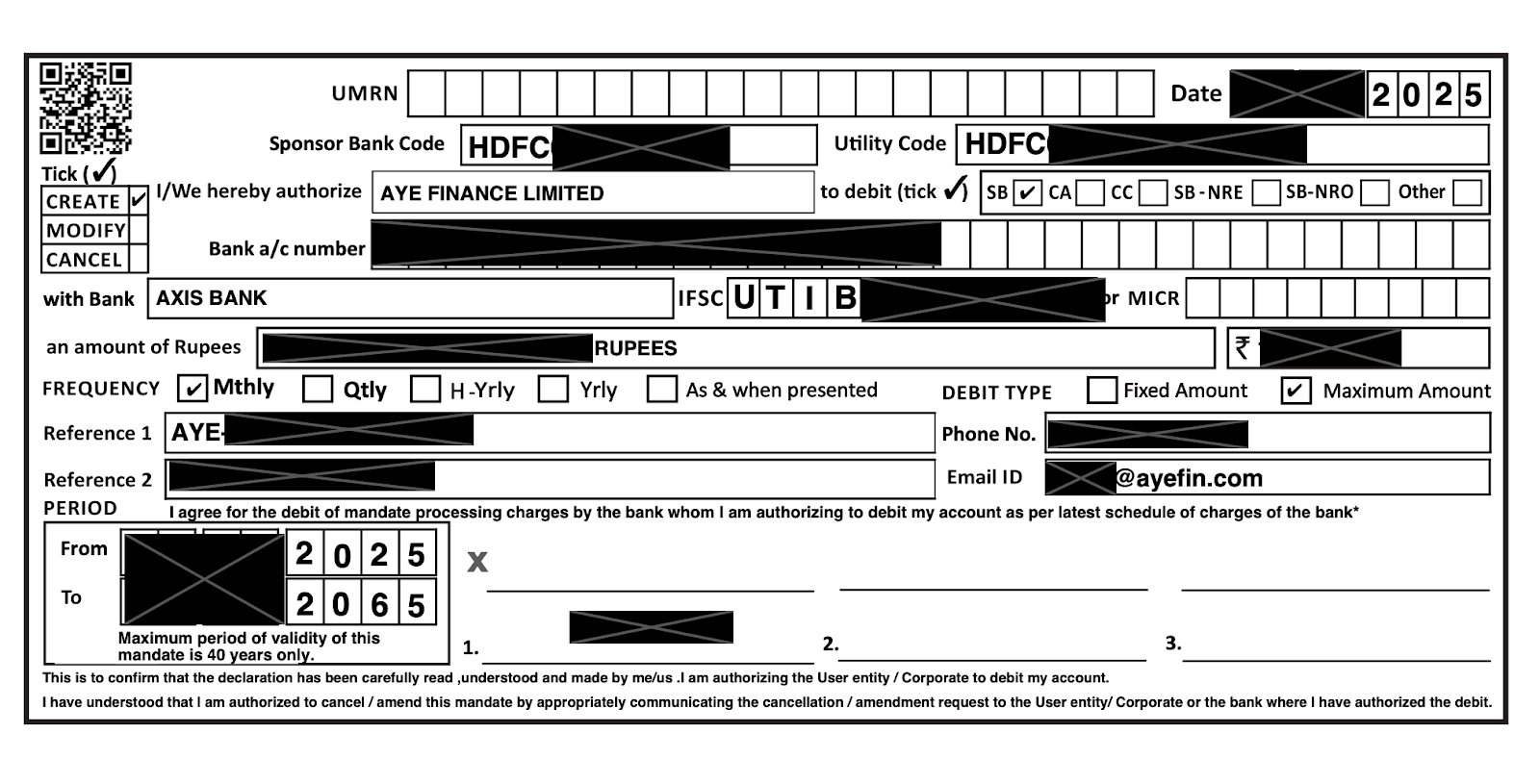
The transaction forms contained typical financial data, such as transaction date, bank codes, institution names, bank account numbers, transaction amount, validity period. On many of the forms, but not all, phone numbers, email addresses and full names of individuals were also present. All of the transactions examined by researchers were well within their validity period, making this active transaction information.
All of the documents were ascribed the metadata title of NACH MANDATE.cdr (although this did not reflect the actual filename.)

Affected Organizations
Of the 38 institutions discovered, a few of the larger banks accounted for most of the transactions, as would be expected in a system such as NACH. However, one institution stood out as the most frequently mentioned, and especially disproportionate to its size.
AyeFin
By far the most common institution mentioend in the data sample was Aye Finance, a small and micro-enterprise business lender. Present in nearly 60% of the sampled documents, AyeFin’s microlender status entails many such small, repetitive transactions, for which NACH was specifically designed. AyeFin offers “a range of financial solutions through 499 branches in 387 districts across 18 states and 3 union territories of India.”
As of 2025, AyeFin serves 500,000 active clients with over 9,000 employees and has 5,535 crore ($627M USD) of assets under management. From 2024-2025 they produced 1,460 crore of revenue ($165M USD) with a profit of 171 crore ($19M USD).
While impressive, Aye Fin is dwarfed in size by the other banks at the top of the list. The State Bank of India is around $790B USD AUM; Punjab National Bank is around $220B USD AUM. Aye Fin’s disproportionate representation amongst the transactions in this data set led to the hypothesis that they would be able to secure the data and/or identify the entity responsible for the bucket.
NPCI
Because all the documents were for money transfers and carried the “NACH MANDATE” document title, we thought that NPCI, the organization overseeing the NACH mandate, could identify which organization would have access to this data set.
On August 29, UpGuard wrote to NPCI, “An Amazon S3 cloud storage bucket, located at <bucket address> is currently configured for public access. In reviewing this publicly accessible data, it is not clear what organization this bucket belongs to, but it is clear that the data is all NACH mandate documentation. I hope that with your oversight powers, you can help identify the responsible party and secure the data.”
On September 23, the NPCI CSIRT replied, “A detailed verification and review have confirmed that no data related to NACH mandate information/records from NPCI systems have been exposed/compromised. The data in question does not belong to NPCI. NPCI operates a robust and secure technology infrastructure aligned with the highest standards of data security and governance.”
A leak from NPCI itself never seemed likely– if it were, we would expect to see banks mentioned more or less in proportion to their size. Thanks to NPCI’s investigation and communication, we can confirm they were not responsible.
Unresolved Attribution
Ultimately, the question of attribution remained unsolved, aside from confirming that NPCI was not reponsible. Given the immediacy of the risk– about three thousand new financial transactions exposed every day– we did not want to let this exposure linger. Rather than wait longer for a response, we notified CERT-IN, after which the bucket was quickly secured.
So what now? When a company is responsible for a data security incident, they are also responsible for notifying affected customers and institutional clients. But when there is no public acknowledgement of an incident, who is responsible for cleaning it up? At a minimum, the bucket owner would be responsible for informing affected entities whether there is evidence of additional third party access to the data. The implications of such black box data leaks for third party risk management are unsettling. Companies are left to rely on a whisper network for information sharing, without clarity on the impacts to their supply chain and their residual risk.
Relevance
The implications for the exposed data should be clear. The bank account numbers and other details in the transaction forms present opportunities for fraud at a large scale, across thousands of transactions at dozens of banks. While services like NACH prevent many problems with non-standard data structures, the companies involved are still responsible for securing their transaction information. The very nature of an aggregate service like NACH creates a centralized means of accessing data. When centralized collections of that data are exposed, the stakes are much higher than they might be for an individual institution. With LLMs and other automation tools, a directory full of forms such as these could be easily scanned, collated and deployed for campaigns of fraudulent transactions
Another risk made clear is that even specialized services, even governmental and financial services, rely on the same back end infrastructure as other, less sensitive services. NACH and the banks who take part in it have a protocol and technology to perform these transactions. However, there is still some part of the process where transactions are scanned into PDFs and stored in the cloud, with its attendant dangers. In these backend reliances, an entire infrastructure’s worth of protections can be undermined by a single misconfiguration.
Protect your organization
Related breaches

Student Applications: How an Education Software Company Exposed Millions of Files

By Design: How Default Permissions on Microsoft Power Apps Exposed Millions
Sign up for our newsletter
Free instant security score
How secure is your organization?




.jpg)
.jpg)

