On Friday, July 18 UpGuard discovered an unauthenticated Elasticsearch database containing about 22 million objects. Each of the objects was a record of a web request containing the domain to which the request was sent, the user’s IP address, and metadata like their location and internet provider. In this case, 95% of the requests were sent to leakzone.net, a “leaking and cracking forum” in the tradition of Raid Forums. This sizeable data set can thus give us an inside view of visitor activity to a very active website used for the distribution of hacking tools, exploits, and compromised accounts.
About Leakzone
Leakzone is part of a long line of forum sites that trade in illicit cyber materials like lists of usernames and passwords, pornography collections, and hacking tools. While law enforcement has shut down many other clearweb leak sites in that time period– the original Raid Forums was seized in 2022, and the founder of its replacement, Breach Forums, was arrested in 2023–Leakzone has survived. Archive.org shows the site beginning to take off in the second half of 2020 and continuing on to the present.

Attribution
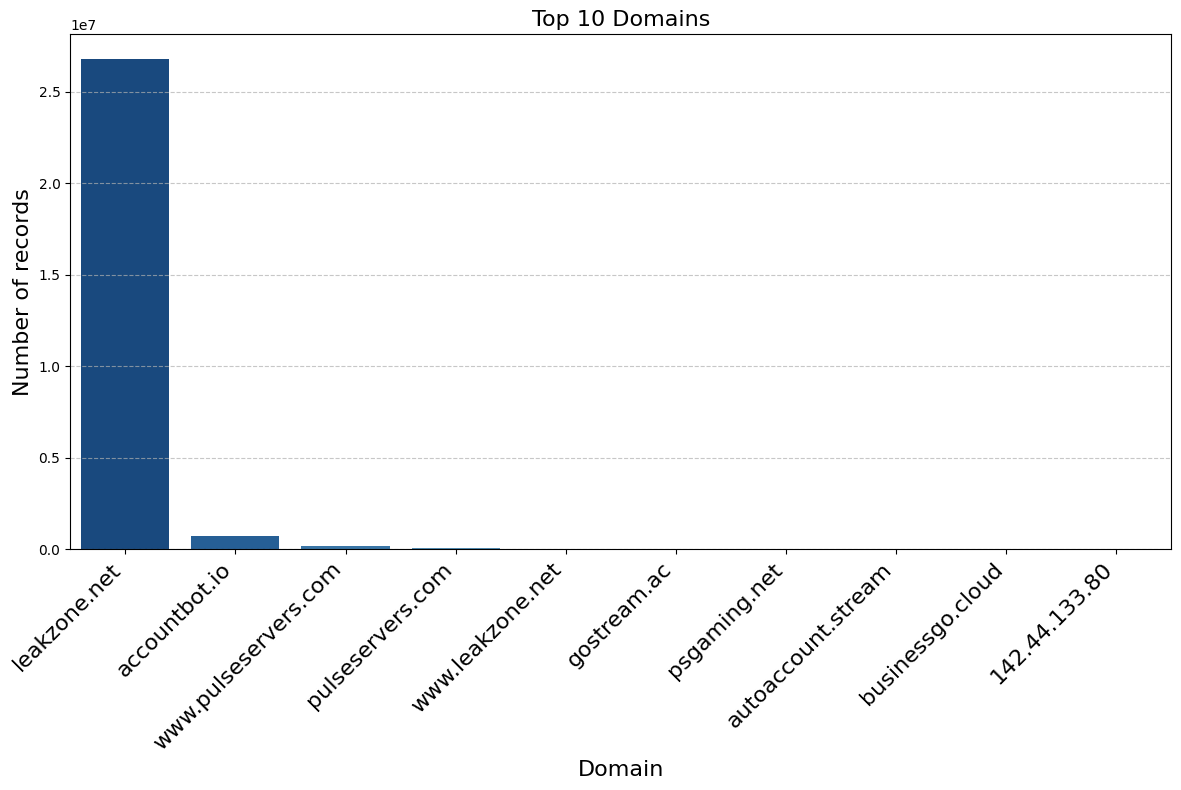
On initial inspection of the exposed data, we saw that “leakzone.net” was mentioned very frequently in the “domain” field of the database schema. After downloading the available data, we were able to confirm that 95% of records named leakzone.net, making this data almost entirely about traffic to that site. The second most common domain, mentioned in 2.7% of records, was accountbot.io, a site for selling compromised accounts. In all, there are 281 unique values, though the other sites have only a fraction of the traffic and include mainstream sports and news sites– unaffiliated sites that may have been mentioned in the logs as part of redirects from Leakzone.
To be certain, we registered an account with Leakzone and saw our IP address show up in the logs, confirming that these logs represented traffic to leakzone.net.
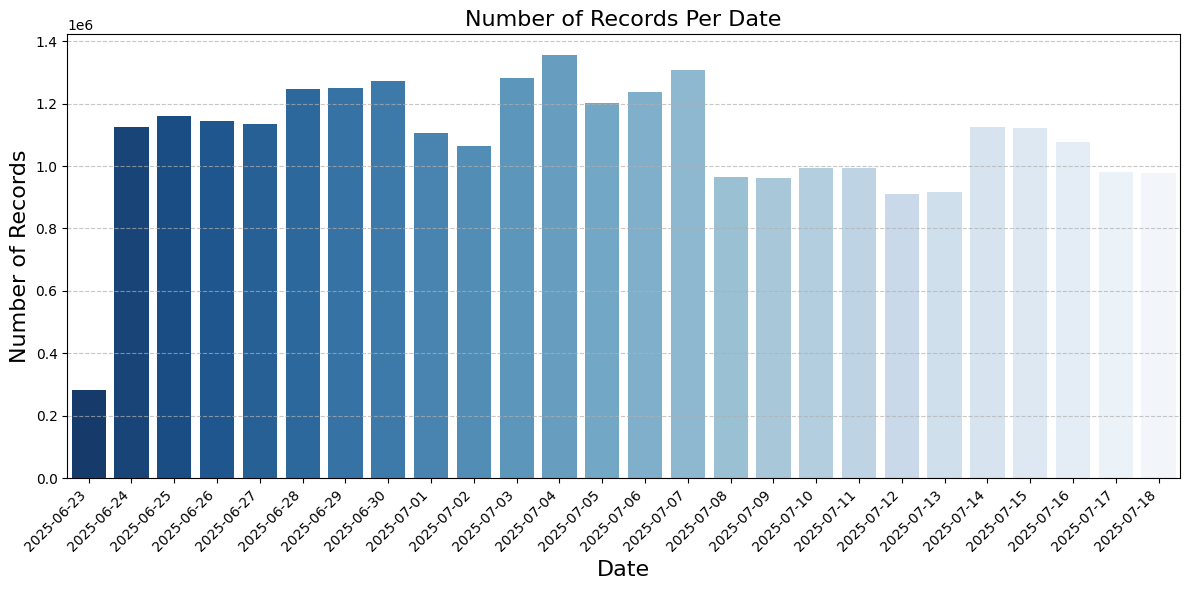
To understand what these records indicated about website activity we plotted them by date. This showed that the records were all quite recent: they began on June 25 and ran up to the time of our download. There were about a million requests per day with a median “request_size” of 2862 bytes– numbers indicative of normal traffic to a reasonably successful website.
Significance
The IP addresses, and what they tell us about visitors to Leakzone and its ilk, are the most interesting part of the collection. GDPR even classifies client IP addresses as PII because of their utility for identifying a person across web properties.
Public Proxies
The data set contained 185k unique IP addresses– more than Leakzone’s entire user base of 109k, which certainly wouldn’t have all been using the site during this time period. (If they had 100% of their users active during a three week period they would be the most successful website of all time). The most likely explanation for the number of unique IPs is that some users were routing traffic through servers with dynamic IP addresses to hide their real IP addresses.
One way to do that is by using public proxies. The data has some information on IP addresses masking real client IPs with this method in the fields for “is_proxy” and “proxy_type,” where the only proxy_type is “PUB”. Around 5% of requests and 2.1% of IP addresses were routing traffic this way, with 1,375,599 total records from 3,983 IP addresses. The use of public proxies to obscure user origins could account for some but not all of the difference between 185k IPs and a plausible number of users.
VPNs
Another way to understand traffic patterns for Leakzone is to identify IPs with the most activity and understand what they are doing. Filtering out the ~5% of IPs that are marked as proxies and focusing on the 100 most active IPs, we see around 8 addresses that are very active, then a long stretch of IPs gradually declining in activity. This distribution is interesting in that it is almost bell-shaped– it would be a half of a normal distribution except there’s a weird cluster of similar IP addresses with around 600,000 records.
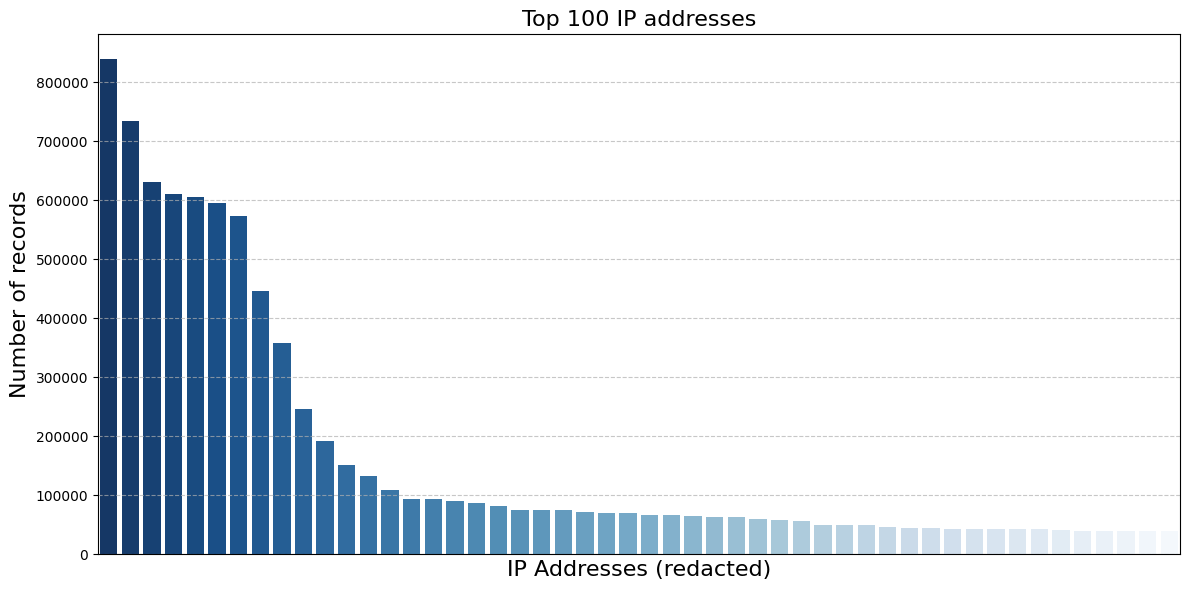
Zooming in on those, the third, fourth, and sixth most common IP addresses are all operated by Cogent Communications, which prominently offers a VPN service. This unusual pattern in our data distribution thus provides evidence that these heavily used IPs are indicative of VPN activity. If the traffic from those three IPs were combined into one, rather than being neatly balanced across three IPs, we would wind up with a normal distribution.
The other IP addresses in the head of the curve are in Lithuania and the UAE, and are also likely VPN exit nodes being used by many users not necessarily located in those countries. Compared to the rest of the distribution, where traffic is spread out across many IPs, these IP address seem like they are rotated much less frequently, which makes them more susceptible to countermeasures like IP blocklists.
Service Providers
After the cluster of heavily trafficked IPs, there is a long middle of IPs doing substantial amounts of traffic spread across many addresses. These IP addresses largely belong to mainstream cloud providers like Amazon, Microsoft, and Google, along with other regional providers.
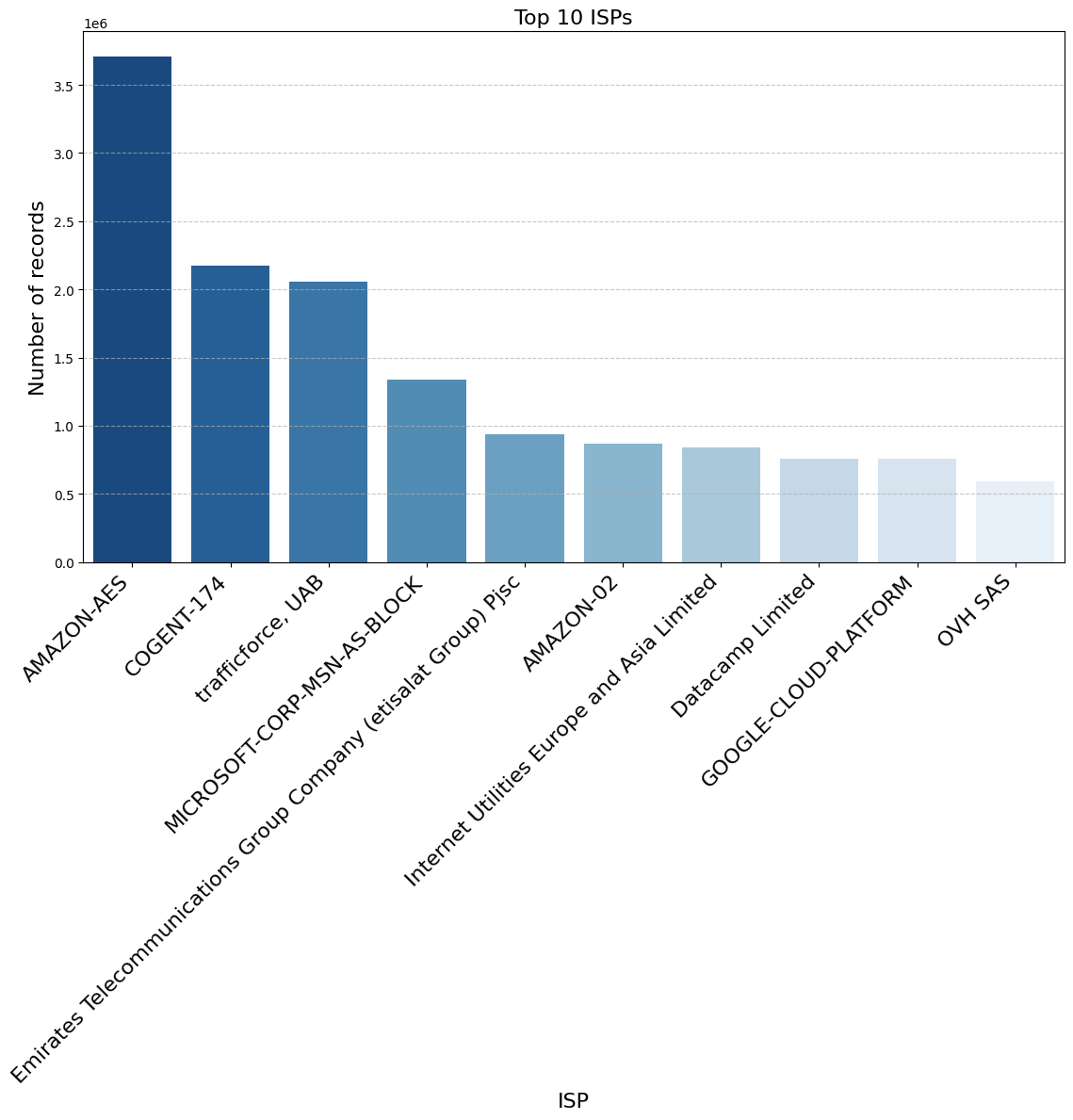
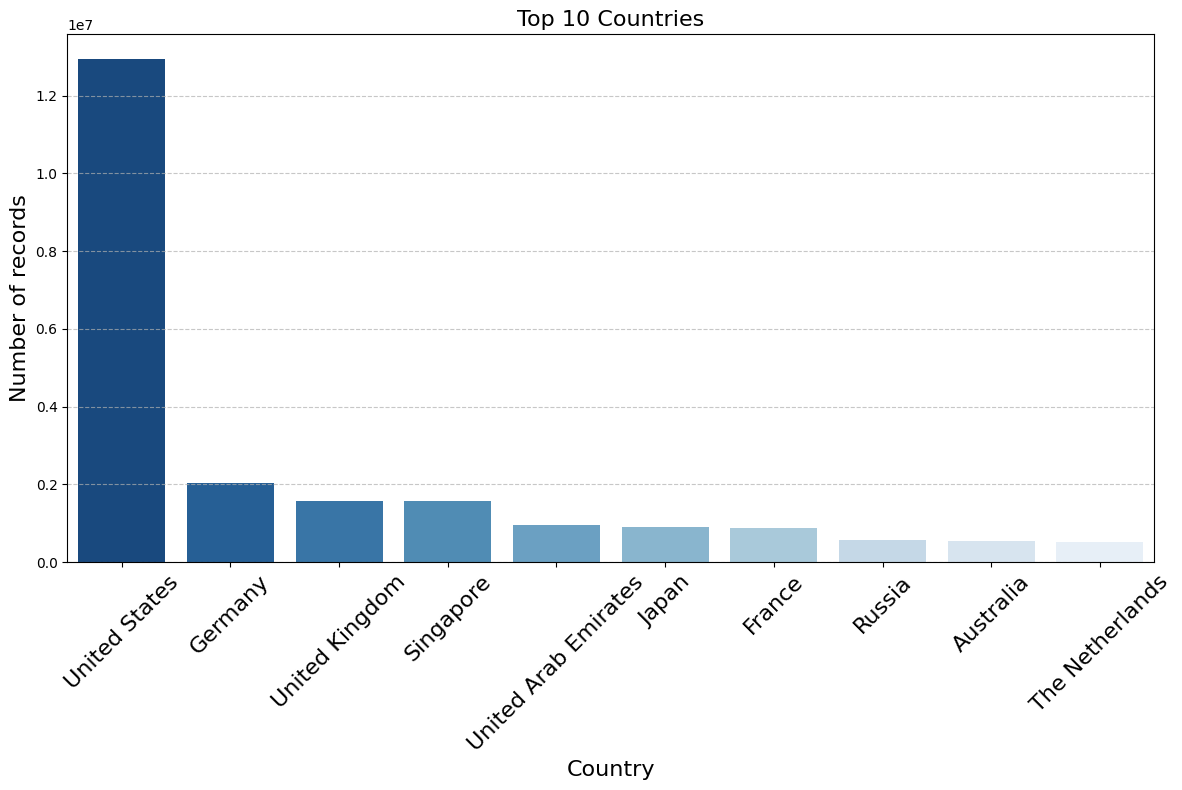
As those service provider names suggest, this traffic comes from all over the world, with the notable exception of China. Any traffic from Chinese users is presumably being routed through proxies in other countries. For example, Huawei Clouds shows up amongst the top twenty ISPs, but its “country” value is Singapore. And of course, given that much of the traffic is being routed through VPNs, the geographic location of the IP addresses tells us little about the location of the users. The distribution of countries in these logs looks very much like the distribution of all IP addresses across the globe minus China.
Outliers
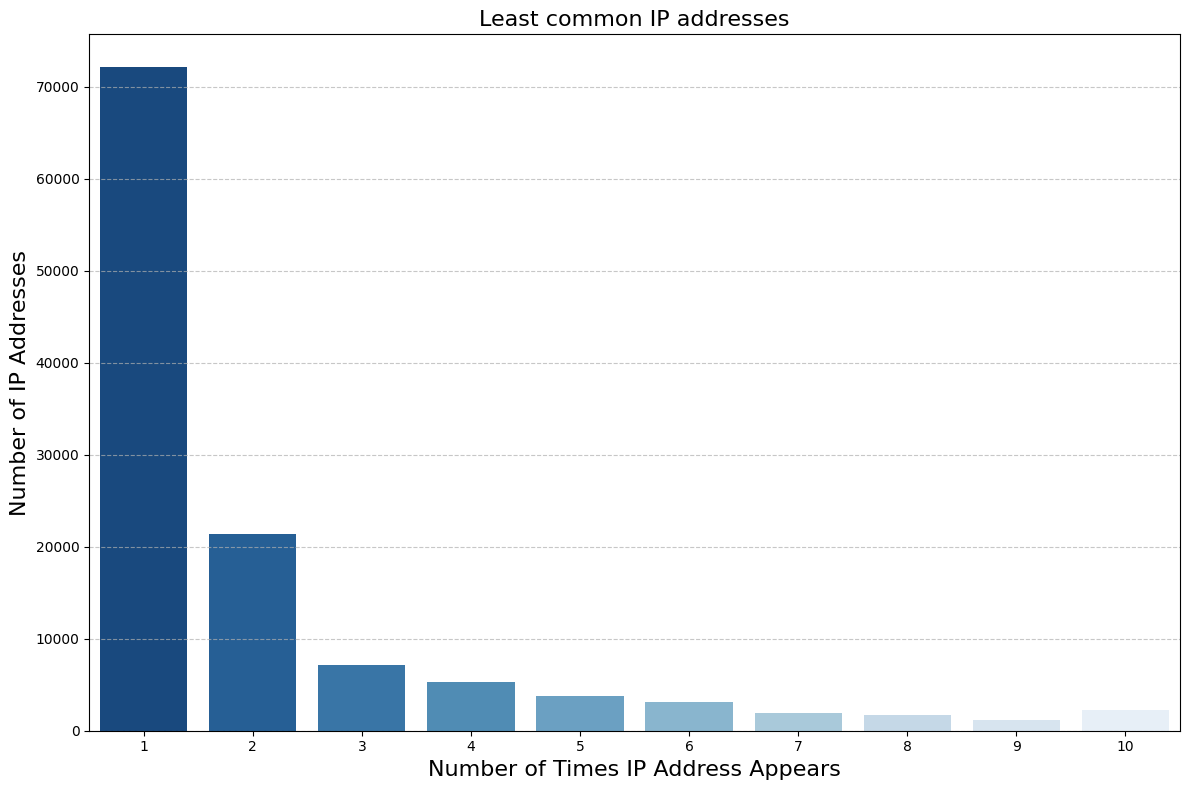
Looking at how the majority of traffic is routed tells us about the behavior of heavy users: they consistently route traffic through VPNs hosted on standard cloud infrastructure. We can also approach the problem from the opposite end: how many users are accessing from IP addresses that show up infrequently?
As it turns out, 39% of all IPs show up only once– and thousands more show up only a few times. Amongst these stray IPs are likely the actual client IPs of users connecting without a VPN.
Conclusion
While Leakzone offers a forum for the exchange of illicit cyber goods, their website notes that they do not host any of the data themselves. It’s likewise important to note that visiting leakzone.net does not mean someone is a hacker or has malicious intent. Insomuch as the data being offered on sites like this is valuable as threat intelligence, it draws the attention of many observers working to track that information to prevent abuse. In fact, it’s entirely possible that the concentrated traffic emerging from certain IP addresses is the result of bots scraping the site on behalf of cybersecurity companies.
This leak should stand as a reminder that anonymity on the internet only lasts so long. Just this week, the suspected administrator of the infamous XSS.is forum was arrested. The law of entropy for the digital universe is that Information wants to be free, and that includes browsing activity linked to client IP addresses. The leak zone becomes a lot less fun when it’s your data that’s leaking.
Protect your organization
Related breaches

Student Applications: How an Education Software Company Exposed Millions of Files

By Design: How Default Permissions on Microsoft Power Apps Exposed Millions
Sign up for our newsletter
Free instant security score
How secure is your organization?




.jpg)
.jpg)

