Top 10 Attack Surface Management Software Solutions in 2026
With many solutions offering attack surface management capabilities, choosing the right tool for your business can be overwhelming. In this post, we cut through the noise to present you with the top 10 ASM tools on the market in 2026.
What is attack surface management?
Attack surface management (ASM) software is a set of automated security tools that continuously discover, monitor, and manage external digital assets that contain, transmit, or process sensitive data. These tools are crucial for identifying misconfigurations and vulnerabilities that cybercriminals could exploit, leading to data breaches or other serious security incidents.
While sometimes confused with vulnerability management, ASM has a distinct and broader focus.
The primary difference lies in their scope. Vulnerability management typically concentrates on identifying, prioritizing, and fixing known vulnerabilities within an organization's inventoried, internal systems. It operates on a list of known assets, scanning them for weaknesses.
In contrast, Attack Surface Management takes an "outside-in" or attacker's perspective. This strategy assumes that an organization has unknown or unmanaged internet-facing assets that are overlooked in monitoring efforts.
The primary goal of Attack Surface Management is to secure all digital assets that could become potential entry points for an attacker, resulting in comprehensive visibility of an organization's entire digital footprint.
Importance of attack surface management
Effective Attack Surface Management (ASM) is a critical component of a modern cybersecurity strategy. By providing a complete and continuous view of all internet-facing assets, ASM enables security teams to transition from a reactive to a proactive cyber security posture management strategy — an essential transition in an age of increasing asset exploitation.
Recent findings highlight the growing risk of unmanaged assets. According to a 2025 IBM report, incidents involving shadow AI — the use of AI-powered tools outside of a company's security policy — accounted for 20% of data breaches.
Some of the key benefits of implementing a robust ASM program include:
- Reduces the risk of Shadow IT: ASM platforms are designed to continuously discover all internet-connected assets, including forgotten test servers, legacy applications, and unsanctioned cloud services. By bringing these assets into view, security teams can apply necessary security controls, patch vulnerabilities, and decommission assets that are no longer required.
- Supports compliance with SOC 2 and ISO 27001: ASM directly supports standards requiring asset inventories be kept up-to-date and regularly maintained. For ISO 27001, ASM provides the continuous asset visibility and risk quantification needed to demonstrate compliance. Similarly, for SOC 2, ASM helps identify and mitigate risks to sensitive data, ensuring access controls are correctly implemented and the constant availability of audit reports.
- Protects brand reputation: By proactively identifying and remediating security gaps before attackers can exploit them, ASM helps prevent the security incidents causing reputational damage.
A strong security posture, demonstrated through diligent management of the attack surface, signals to customers and partners that the organization is a trustworthy steward of their data.
Challenges in attack surface management
While Attack Surface Management (ASM) is a critical discipline, organizations struggle to implement it effectively. These challenges stem from the increasing complexity of modern IT environments, the rapid pace of digital transformation, and constantly evolving cyber threats
Key pain points include:
- Identifying unknown assets and Shadow IT: One of the most significant challenges is maintaining an accurate and up-to-date asset inventory amid shadow IT practices. During security tests, it is common to discover systems and digital assets that security teams were previously unaware of.
- Scaling across distributed environments: The modern attack surface spans multi-cloud deployments, remote work setups, and a growing number of IoT devices. As this fragmented landscape expands, comprehensive monitoring becomes a major operational hurdle in enterprise attack surface management.
- Managing third-party and supply chain risk: An organization's attack surface extends to its partners, vendors, and suppliers. These third parties often have access to internal systems or provide critical services. Yet, tracking the individual impacts of all cyber risks across this network on your organization's security posture is difficult.
- Overcoming the human element: Technology is only one part of the attack surface; the people within an organization are also a critical component. Addressing human factors in cybersecurity while not neglecting the role of technology in this complex risk category is a difficult challenge that conventional awareness programs alone cannot solve
- Lack of inter-team coordination: Effective attack surface management requires strong collaboration and communication between security and technology teams. Poor inter-team coordination delays remediation of identified risks, leaving critical assets vulnerable to cyberattacks.
To address some of these challenges, organizations should choose an ASM solution with the following features:
- Automation and continuous monitoring: Platforms that automatically map an organization's digital attack surface enable the level of continuous monitoring required to keep up with a constantly expanding attack surface, ensuring security teams prioritize the most critical risks to an organization's sensitive data.
- Integrated vendor risk management workflows: ASM platforms integrating VRM workflows extend their scope of cyber risk monitoring to include the broader supply chain network, giving security teams advanced awareness of the impact of vendor-related risks on an organization's level of data breach resilience.
- External attack surface scanning: Scanning external attack surfaces with a Vendor Risk Management tool discovers vulnerabilities common in multi-cloud deployments, such as open FTP servers, misconfigured cloud storage buckets, and exposed databases.
Many of the key challenges of Attack Surface Management can be addressed by shrinking your attack surface. Watch this video for an overview of this process.
Top 10 attack surface management solutions in 2026
Refer to this table for a quick comparison of all the ASM tools in this list:
1. UpGuard
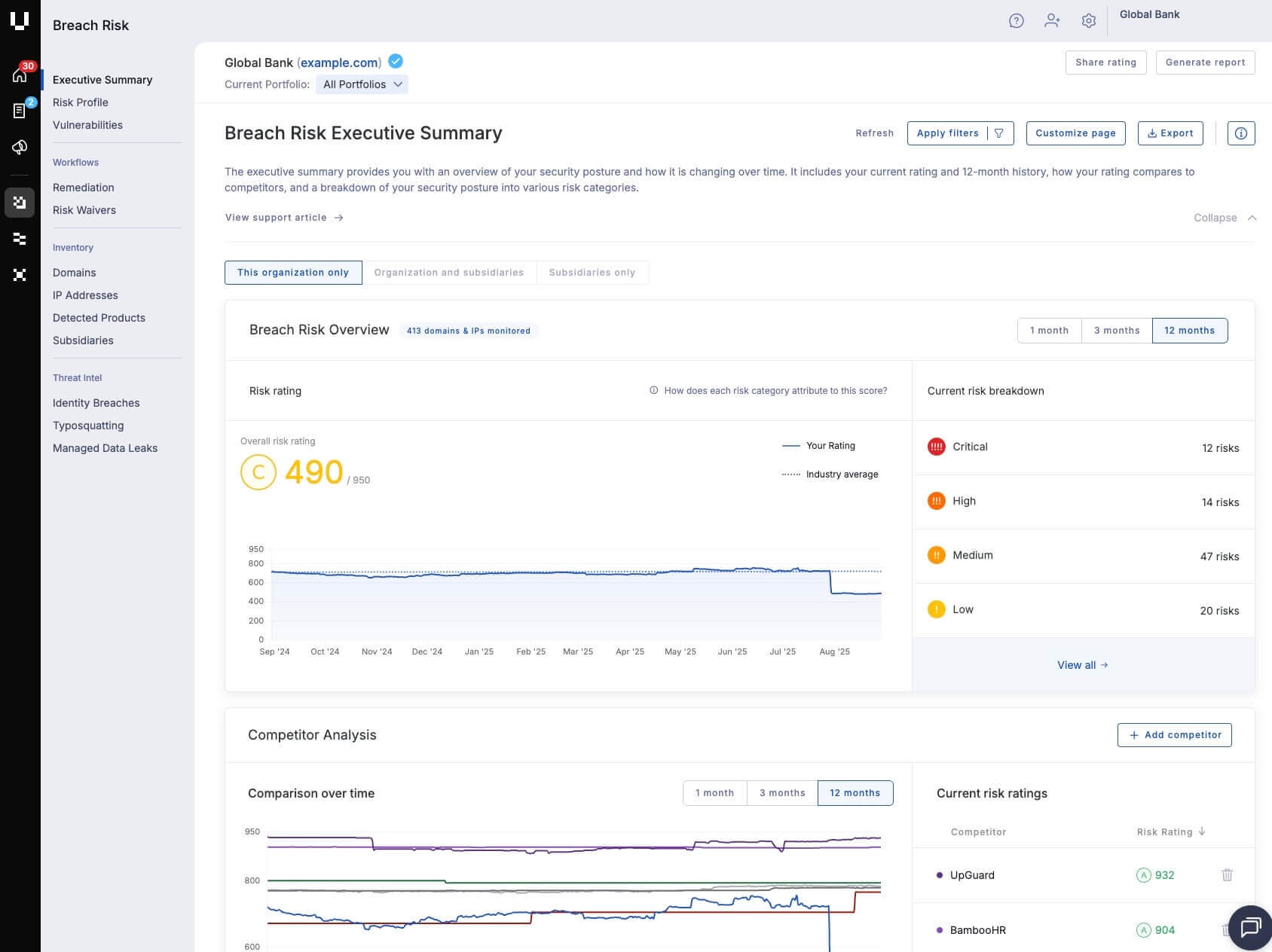
Key attack surface management product features
- Scans external attack surfaces to identify vulnerabilities such as open FTP servers, misconfigured cloud storage buckets, and exposed databases.
- Integrates data from these automated scanning results into a unified workflow for assessing and managing vendor risk profiles.
- Continuously scans vendor domains and IP addresses to identify automated risk findings, with applied risk modifications like waivers or fixes being tracked.
- Automatically populates up to 30% of a vendor's security profile by continuously scanning public security documents, provided evidence, and data from UpGuard's automated attack surface scans.
- Tracks remediation progress based on a 24-hour scan cadence and updates risk status automatically once remediated.
- Allows on-demand rescans for immediate status updates of remediated risks.
Why UpGuard?
UpGuard offers continuous attack surface monitoring of an organization and its vendors. Paired with data leak detection capabilities, the platform offers complete attack surface protection against misconfigurations and vulnerabilities that could facilitate data breaches.
Who uses UpGuard's attack surface management services?
UpGuard is a cybersecurity platform that helps global organizations prevent data breaches, monitor third-party vendors, and improve their security posture. Using proprietary security ratings, world-class data leak detection capabilities, and powerful remediation workflows, we proactively identify security exposures for companies of all sizes.
Start your free UpGuard trial >
External asset discovery
With UpGuard’s attack surface management features, you can keep an accurate and always up-to-date inventory of all external facing assets. UpGuard’s automated asset discovery process maps domains and IP address mapping to your organization based on active and passive DNS and other fingerprinting techniques.
You can also specify IP address monitoring ranges for IT asset detection. This will automatically acknowledge any new devices connected within these ranges once they become active, keeping your asset inventory updated.

Watch this video to learn how UpGuard can help you detect obscure technologies in your external attack surface:
Third-party cyber risk detection
UpGuard’s risk profile feature detects a vast range of potentially exploitable attack vectors in the external attack surface, including complex risks like unmaintained web pages, end-of-life web server software, and vulnerabilities in Microsoft Exchange server software.

Vendor security posture tracking
UpGuard’s security ratings feature offers an accurate and unbiased representation of each vendor’s security posture.
Security teams can leverage UpGuard's security rating technology to project the impact of remediation tasks associated with third-party risks detected through automated scanning processes. This feature makes it easier to decide which remediation tasks should be prioritized to maximize the effectiveness of an external attack surface management program.

Dashboards summarising vendor risk exposure offer a single-pane-of-glass view of your entire third-party attack surface. With continuous monitoring of third-party attack surfaces, these dashboards can help you track security posture improvements in real time

Integrated risk management workflows
The UpGuard platform offers integrated workflows addressing both the analysis and risk management aspects of Attack Surface Management. The platform's risk assessment workflow bridges the gap between these two components, allowing users to conveniently track all relevant cyber risk lifecycles from a single operational perspective.
Watch this video for an overview of UpGuard's risk assessment workflow.
For keeping stakeholders informed of your attack surface management efforts, UpGuard's reporting workflow references a library of customizable reporting templates, that can be generated based on your attack surface manegement insights with a single click.
UpGuard's reporting library includes a board summary report template and PowerPoint slides to streamline board presentations about ASM efforts.
Start your free UpGuard trial >
2. Bitsight

Key attack surface management product features
- Security ratings
- Attack surface analytics
- Continuous third-party monitoring
Learn how Bitsight compares with UpGuard >
Why Bitsight?
Bitsight is a cybersecurity ratings platform that continuously monitors the security postures of organizations and their vendors. In addition to risk monitoring, Bitsight employs analytical forecasting to estimate future security performance and integrates with platforms like ServiceNow and JIRA for advanced workflows.
However, the platform has notable drawbacks. Its pricing structures can quickly escalate operational expenses for third-party risk management programs. Customers have also cited attribution challenges for risks and assets within shared IP and cloud environments, which require support submissions to address.
In addition, Bitsight's monitoring and assessment capabilities are licensed separately, which can complicate purchasing and limit end-to-end risk coverage.
Who uses Bitsight's attack surface management services?
Bitsight is used by companies in finance, healthcare, technology, and government sectors. Security and risk management professionals primarily leverage its platform for third-party risk management, security performance benchmarking, and cybersecurity performance reporting.
3. Panorays

Key attack surface management product features
- Third-party security ratings
- Cyber risk monitoring
- Dark web insights
Learn how Panorays compares with UpGuard >
Why panorays?
Panorays is an IT Vendor Risk Management solution that combines external attack surface monitoring with vendor risk questionnaires to provide visibility into a vendor's security posture. The platform excels in automated questionnaire workflows, which help simplify vendor assessments and the onboarding process. It integrates external scans, questionnaires, and certifications into a unified security rating to quantify vendor risk.
However, the platform has significant limitations. A key weakness is that it lacks fully real-time monitoring capabilities, which contradicts claims of real-time alerting. Additionally, Panorays underperforms in its reporting, offering limited options for customizing reports and dashboards. The platform also does not natively support TPRM workflows, which forces customers to purchase additional tools to manage the third-party risk lifecycle effectively.
Who uses Panorays' attack surface management services?
Panorays partners with resellers, MSSPs, and technology to provide an automated third-party security platform that manages the inherent and residual risk, remediation, and ongoing monitoring.
4. SecurityScorecard

Key attack surface management product features
- Third-party security ratings
- Cyber risk intelligence
- Hacker chatter monitoring
Learn how SecurityScorecard compares with UpGuard >
Why SecurityScoreCard?
SecurityScorecard offers insights into a company's vendor risk exposure through its cybersecurity ratings platform. It draws from open, proprietary, and dark web sources. It presents its findings in an A–F letter grade system, making vendor risk exposure easy for non-technical stakeholders to understand.
However, potential users should be aware of several limitations. The platform’s staggered scan cycles can disrupt real-time visibility into a vendor's security posture. Customers have also reported occasional issues with inaccurate IP attribution that require support requests to fix. Additionally, vendor monitoring and risk assessment workflows are licensed as separate modules, which may increase purchasing complexity.
Who uses SecurityScorecard's attack surface management services?
Organizations use SecurityScorecard’s rating technology for self-monitoring, third-party risk management, board reporting, and cyber insurance underwriting.
5. ProcessUnity (formely CyberGRX)

Key attack surface management product features
- Continuous monitoring of inherent risk
- Risk scoring
- Real-time threat intelligence
Learn how CyberGRX compares with UpGuard >
Why ProcessUnity?
ProcessUnity is a third-party risk management platform designed to streamline the entire vendor lifecycle, from onboarding to offboarding. The platform's core strength is its Global Risk Exchange, a library of pre-completed, validated vendor assessments that can significantly reduce the effort and time needed for security reviews.
However, a primary drawback is the platform's lack of native external scanning capabilities. ProcessUnity relies on third-party integrations with security rating providers to deliver external risk insights. This dependency means the accuracy of its external risk data is entirely contingent on the quality of the chosen partner solution. This model also heavily relies on vendor participation to keep assessments in the exchange up-to-date.
Who Uses ProcessUnity?
ProcessUnity provides security professionals, risk managers, and procurement managers with ongoing vendor portfolio analysis.
6. OneTrust Vendorpedia

Key attack surface management product features
- Third-party risk exchange
- Privacy, security and data governance platform
- Insights on vendors’ security controls, policies, and practices
Learn how OneTrust Vendorpedia compares with UpGuard >
Why OneTrust Vendorpedia?
OneTrust does not natively incorporate many of the critical breach vectors associated with an organization’s external-facing attack surfaces.
It Offers an AI engine via their Athena product enabling risk insights across privacy, security, and governance risks. Athena provides insights about a vendor’s internally managed security controls, policies, and practices.
Who uses OneTrust Vendorpedia's attack surface management services?
OneTrust Vendorpedia is used by small and medium businesses and large enterprises. Its services are particularly valuable for privacy, compliance, and risk management teams who use the platform to automate vendor due diligence, manage vendor contracts, and ensure compliance with various data protection regulations.
7. RiskRecon

Key attack surface management product features
- Continuous monitoring of an organization and its vendors
- IT profiling
- Security analytics
Learn how RiskRecon compares with UpGuard >
Why RiskRecon?
RiskRecon specializes in external security monitoring and is well-regarded for its accurate asset attribution and strong cloud scanning capabilities. The platform provides reliable, actionable insights and helps IT teams prioritize vulnerabilities based on asset value.
While external scanning is a primary strength, RiskRecon takes a partnership and integration-first approach to vendor assessment workflows. This means that to achieve a complete and optimal third-party risk management experience, organizations will need to adopt an additional solution from one of RiskRecon's partners to handle the assessment process.
Who uses RiskRecon's attack surface management services?
Organizations worldwide, including those in finance, insurance, healthcare, energy, and defense, use RiskRecon to minimize their risk.
8. Recorded Future

Key attack surface management product features
- Threat intelligence platform
- Delivers intelligence insights across six risk categories: brand, threat, third-party, SecOps, vulnerability, and geopolitical
- Evidence-based risk scoring
Learn how Recorded Future compares with UpGuard >
Why Recorded Future?
Recorded Future provides context surrounding vulnerabilities, enabling organizations to prioritize remediation.
Recorded Future’s Vulnerability Intelligence module collects vital vulnerability data from various open, closed, and technical sources, assigning each vulnerability a risk score in real time.
Who uses Recorded Future's attack surface management services?
Recorded Future provides threat intelligence to a global customer base. The platform is primarily used by security operations center (SOC) analysts, threat intelligence teams, incident responders, and vulnerability management professionals to proactively identify and prioritize threats, investigate incidents, and understand their external attack surface.
9. Digital Shadows (acquired by ReliaQuest)

Key attack surface management product features
- Attack surface monitoring
- Vulnerability investigation
- Threat intelligence
Learn how Digital Shadows compares with UpGuard >
Why Digital Shadows?
Digital Shadows Searchlight™ identifies vulnerabilities, allowing organizations to prioritize and patch their most critical identified risks. Its SearchLight™ product continuously identifies exploitable vulnerabilities across an organization’s public-facing infrastructure.
Who uses Digital Shadows' attack surface management services?
Digital Shadows, now part of ReliaQuest, provides security teams with threat intelligence and focused digital risk insights. Its platform is used by security operations (SecOps) professionals, threat analysts, and brand protection teams to identify and manage risks across the open, deep, and dark web, helping them protect their organization's external-facing digital assets.
10. CybelAngel

Key attack surface management product features
- Asset discovery and monitoring
- Incident severity indicator
- CVE vulnerability detection
Why CybelAngel?
CybelAngel gains visibility into organizations’ attack surfaces. The platform's Asset Discovery & Monitoring solution identifies and helps secure vulnerable shadow assets.
Who uses CybelAngel's attack surface management services?
CybelAngel provides digital risk protection solutions to global enterprise clients. Security teams, brand protection specialists, and risk managers use its platform to discover and remediate external threats such as data leaks, exposed credentials, and shadow IT across the open, deep, and dark web.
Real-world examples of how UpGuard helps organizations with attack surface management
The following is an overview of how real customers leveraged the UpGuard platform to help with specific aspects of their Attack Surface Management programs.
ASM Focus: Increasing visibility and asset discovery
Open-Xchange
- Challenge: The company's existing vulnerability scanner could only monitor known assets and lacked asset discovery capabilities, preventing them from having a complete register of their IT environment.
- Solution: Open-Xchange leveraged UpGuard to automate the discovery process for its public-facing assets, using the platform as a primary source for identifying newly discovered assets to add to their internal scanner.
Read the Open-Xchange case study.
Rimi Baltic
- Challenge: As a multinational organization with over 30 domains hosted across a combination of legacy and modern systems, the IT team found their manual asset discovery process challenging and "very tricky."
- Solution: The team found that asset discovery came "straight out of the box" with UpGuard, which brought all of their external resources into "one concrete picture" and provided greater visibility of their external attack surface.
Read the Rimi Baltic case study.
Ideals
- Challenge: The company required complete visibility across its IT infrastructure to effectively mitigate cybersecurity risks while enabling the product team to roll out new features rapidly.
- Solution: UpGuard provided increased visibility across the company's public attack surface, allowing them to resolve hundreds of maintenance tickets they previously wouldn't have detected.
Nexus Technologies, Inc.
- Challenge: The company's agile business model, which combined cloud solutions with on-premises software, created a complex attack surface where it was easy to overlook exposures.
- Solution: Nexus Technologies used UpGuard to understand all the risks linked to its entire digital footprint. This gave them peace of mind that they had not overlooked any vulnerabilities across their mixed environment.
Read the Nexus Technologies, Inc. case study.
ASM Focus: Attack surface reduction
Colorado State University
- Challenge: As a large institution, the university managed a highly distributed IT footprint with numerous public-facing domains and IPs that were not run centrally, creating a massive and difficult-to-track attack surface.
- Solution: UpGuard provided an automated way to view the attack surface, helping the university develop an asset inventory. This flagged unmaintained pages and end-of-life software, allowing them to pursue attack surface reduction with departmental IT managers.
Read the Colorado State University case study.
ASM Focus: Continuous monitoring
Games24x7
- Challenge: The team wanted a tool that would provide them with continuous visibility across their digital surfaces, enabling them to take immediate remediation measures to enhance their overall security posture.
- Solution: The company uses UpGuard to effectively discover and categorize exposure in its attack surface by severity. The platform's automated reports help it swiftly identify and respond to threats, enabling them to proactively safeguard its systems.
Read the Games24x7 case study.
Superloop
- Challenge: As a telecommunications provider with a complicated environment and many cloud-first vendors, Superloop required granular, layered insight into its supply chain to understand the critical operational impacts of security risks.
- Solution: Superloop implemented UpGuard Breach Risk as part of its supply chain security monitoring program. The platform provides an "interesting layered insight on our supply chain that could have a critical impact on our operation," which the company's CIO described as "vital" for their mission-critical services.