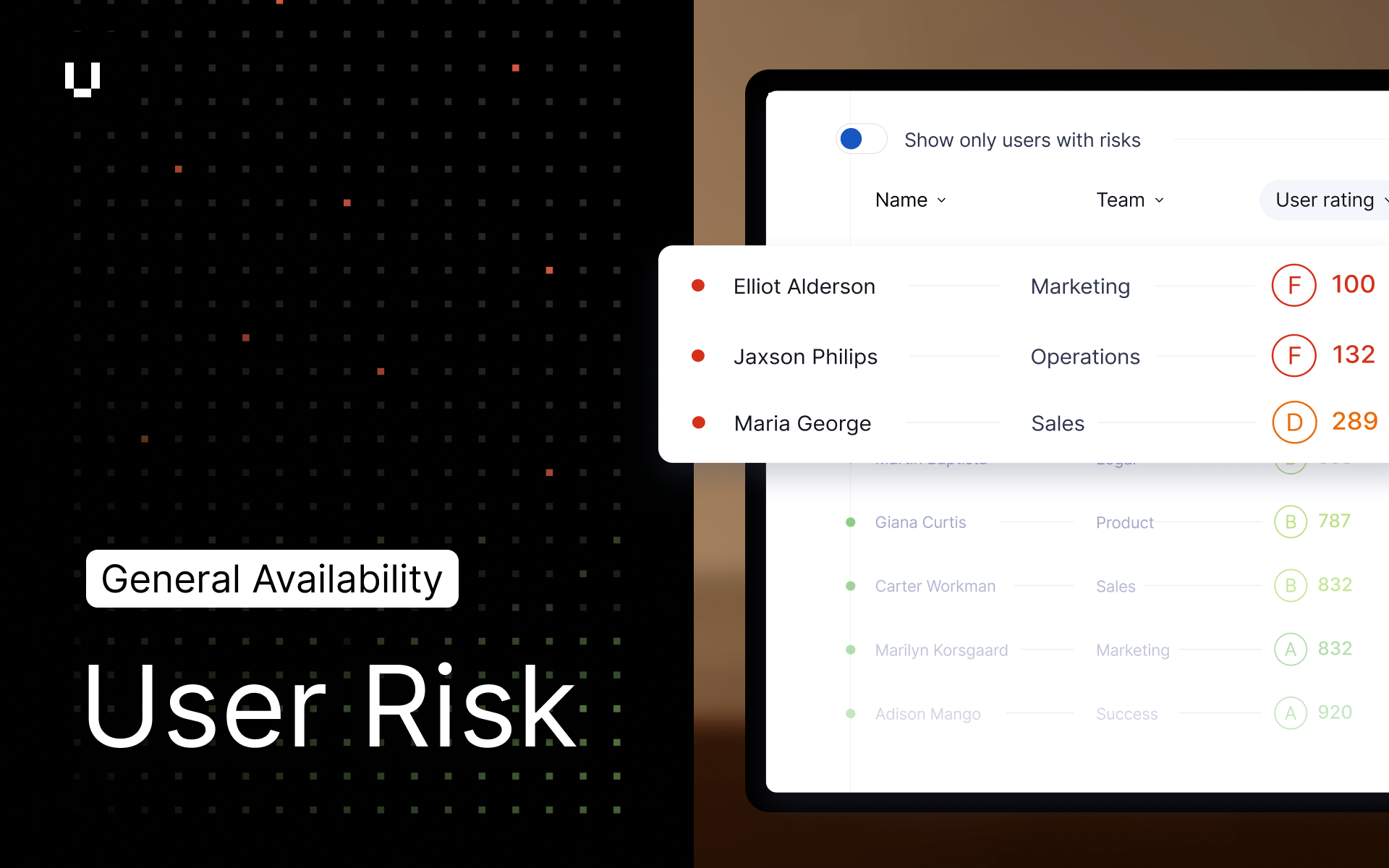
We are thrilled to announce that UpGuard User Risk has moved from Early Access to General Availability (GA). While you already trust UpGuard for "outside-in" security, User Risk completes the picture with an "inside-out" view of your internal workforce.
During User Risk development, we confirmed the challenges many organizations face around Shadow IT:
- Volume: Companies often have more SaaS applications than employees, they just don’t realize it.
- The "Long Tail": 60% of apps are used by just one person, making manual tracking impossible.
- SSO Blind Spots: 50% of app usage happens outside corporate SSO.
User Risk solves this with a complete workflow:
- Unified Visibility: Discover your true SaaS and AI footprint, permissions, and compromised credentials in a single view rather than siloed data.
- Prioritize & Govern: An AI Analyst automatically prioritizes risks to create clear action plans, allowing you to proactively govern policies.
- Change Behavior: Direct your users to use approved applications with real-time "nudges." If a user accesses an unapproved tool, User Risk immediately recommends an approved alternative.
How to Get User Risk: To complete your 360-degree view of risk, contact your Customer Success Manager today.
Introducing new premium Trust Exchange features
We are excited to announce the launch of a new tier of premium features in Trust Exchange, designed to supercharge your sales and security workflows. This includes the ability to import up to 15 security questionnaires per month and automate responses using unlimited AI calls which is crucial for managing a high volume of vendor requests. Trust Exchange customers can ensure brand consistency and document control with Custom Domain Configurations for your Trust Page and PDF Download Watermarking, providing an essential layer of security for sensitive documents.
Explore the new tier and sign up free here.
Ready to upgrade? Contact your Customer Success Manager.
No Customer Success Manager? You could upgrade it yourself in-product.
Get ready to scale your trust operations and look out for our next major update on a new feature, Multi Trust Pages coming in early December!
ISO 27001 and NIST CSF control templates for Security Profile
Assess vendors against international security standards with new control templates for ISO 27001:2022 and NIST CSF 2.0 in the Security Profile. Users can assess vendor adherence, automatically uncover mapped risks, send targeted gap questionnaires and generate comprehensive risk assessment reports aligned to these frameworks. These new templates can be set as the default for a specific vendor tier in settings to ensure consistency. For more information, read our Help Center article.
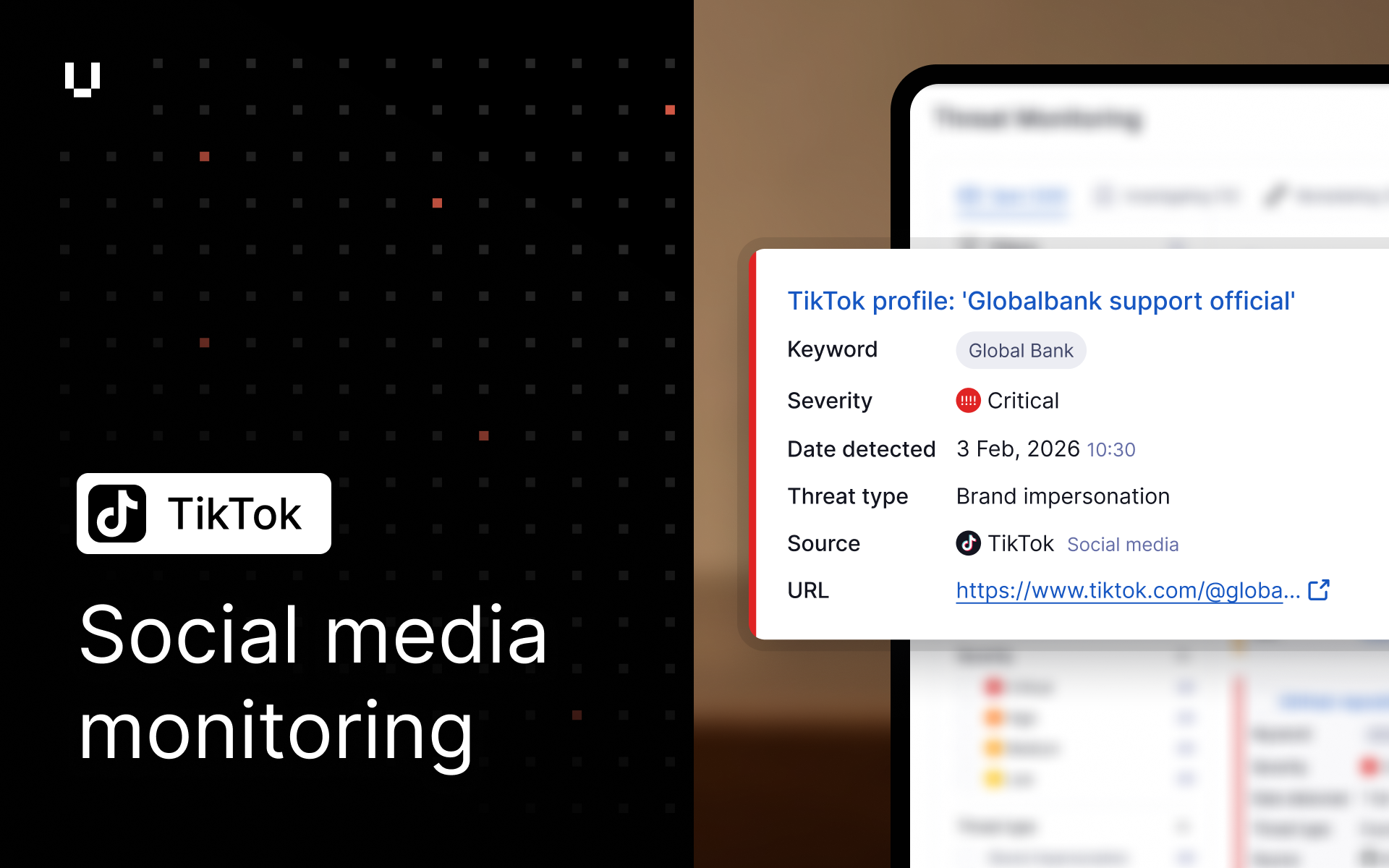
Social media monitoring added to Threat Monitoring
We’ve launched Social Media Monitoring, expanding Threat Monitoring to include Facebook and Instagram profiles and posts. This release detects key social media threat types, including brand impersonation, phishing and scam content, planned protests or activism, and indicators of violent threats.
Social Media Monitoring is available at no additional cost for all existing Threat Monitoring customers. It forms part of our ongoing commitment to continuously broaden and refine detected threat signals, delivering the broadest possible coverage while reducing noise and false positives through improved AI analysis and source tuning.
Read our CISO's Guide to Defending Against Social Media Impersonation
Other improvements
- Threat Details within Threat Monitoring now includes pagination across “Investigating”, “Remediating”, and “Closed” views, bringing consistency with the “Open” view and making it easier to navigate and review threats at scale.
- When infostealer malware has been detected, the resulting risks now provide clearer triage and remediation details, including redacted email and web-addressed credentials, along with updated guidance on creating a waiver within the platform.
- We have added 26 more detected products including MongoDB, Zabbix, Caddy and many more. These changes help you understand your own attack surface in more depth.
- We’ve added a Foreign Ownership, Control and Influence (FOCI) Internal Vendor Review questionnaire based on Australian Government FOCI Risk Assessment Guidance to the questionnaire library. This internal questionnaire serves as a preliminary assessment to determine if a full FOCI risk assessment is required.
- This release includes several bug fixes.
UpGuard Release Notes
See UpGuard In Action
Free instant security score
How secure is your organization?