A CISO's Guide to Defending Against Social Media Impersonation
The platforms your customers trust to connect with your brand are now being weaponized to destroy its reputation. AI is equipping cybercriminals with industrial-scale operations that can replicate your brand presence across all major social platforms in just minutes.
This guide provides a CISO's framework for moving from reactive brand monitoring to proactive threat disruption, detailing a four-pillar plan to neutralize these threats before they impact your business.
The dawn of industrial-scale brand impersonation
The threat landscape of impersonation attacks has changed forever. Brand impersonation now comprises 51% of all browser-based phishing attempts. This isn't a recent emergence. In 2024, brand impersonation attacks increased by 42%, and since then, Microsoft has prevented over 5,000 credential thefts via social media phishing.
Since ChatGPT's launch in late 2022, phishing attacks have grown by 4,151%, indicating that, unsurprisingly, AI is the mechanism driving this insurgency.
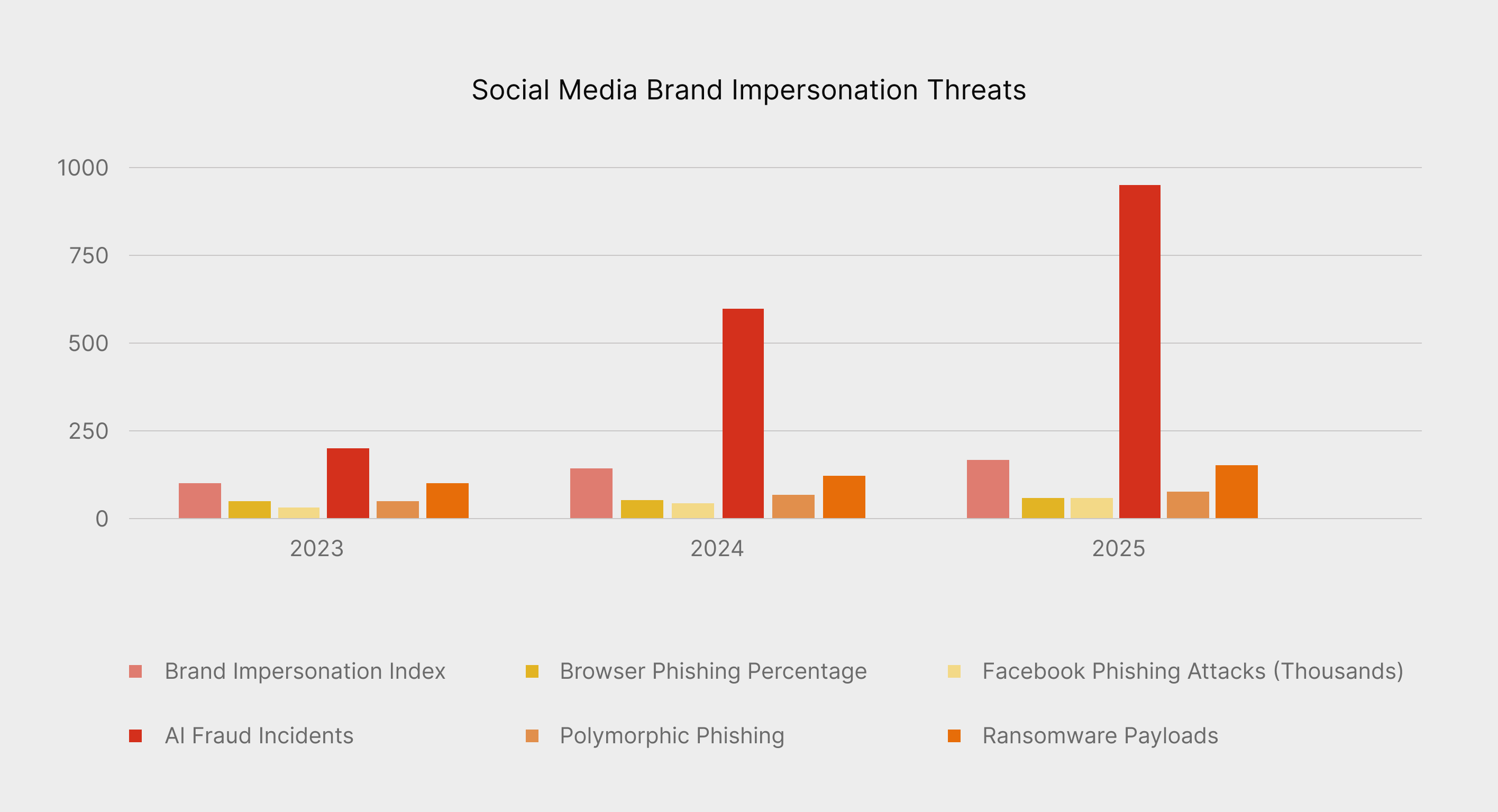
The mid-market vulnerability gap
This threat is particularly acute for mid-market organizations (500-10,000 employees), providing the perfect conditions for exploitation — maximum exposure with minimal defense capability.
Their vulnerability is driven by:
- Lean security teams: Small teams of 5-20 people lack the bandwidth to continuously monitor multiple social media platforms.
- Limited visibility: A reliance on traditional, perimeter-based security tools creates a massive blind spot for social media threats.
- Executive exposure: Public-facing leadership roles make executives attractive and easy targets for impersonation.
- SOC overload: With over 252,000 new websites created daily and tens of thousands of malicious URLs detected by Proofpoint in just months, the sheer volume of potential threats overwhelms security operations centers (SOCs) and human-led response capabilities.
The result is a perfect storm: maximum exposure with minimal defense capability.
How popular social platforms are being exploited
Understanding how attackers abuse each major social media platform is critical for building adequate defenses.
1. Facebook/Meta
Facebook has become the epicenter of systematic brand impersonation. The attack methodology is ruthlessly efficient. Threat actors create fake business pages that mirror legitimate brands, then use Facebook's advertising system to promote phishing content directly to targeted employee lists harvested from LinkedIn.
Examples of impersonation attacks on Facebook
- "Facebook guest" scam: A widespread campaign known as the "Facebook Guest" scam targets business pages with distressing messages falsely claiming that the page's content has violated copyright or community standards. These messages, which contain links to credential-stealing websites, are quite convincing, even to cyber threat-aware users.
- Malicious brand advertising: Threat actors create malicious advertisements that mimic legitimate brands and then use Facebook's ad system to target specific users with phishing content.
- Fake job advertisements: Fraudsters post fake job advertisements on Facebook, impersonating a real company or a recruitment agency. The goal is to trick applicants into paying upfront for "training" or "background checks," or to harvest their personal information for identity theft.
2. LinkedIn
Attackers exploit LinkedIn's credibility by creating fake executive profiles. They then use these personas to request sensitive information or credentials from employees who believe they're communicating with legitimate leadership.
Examples of impersonation attacks on LinkedIn:
- Fake profiles: Attackers create fake profiles to send connection requests to users. These profiles often have red flags, such as using stock photos, having incomplete or vague details, and showing a general lack of engagement, like posts or comments. These fake connections are often the first step in a larger scam.
- Phishing scams: After connecting with a target, scammers send convincing messages containing links designed to steal credentials or deploy malware. Attackers may also impersonate official LinkedIn communications to trick users into clicking these malicious links.
- Fake job offer scams: Scammers may impersonate recruiters or use fake employee profiles to post fraudulent listings containing credential-stealing links.
- Crypto investment scams: This is a growing threat in which scammers impersonate financial experts or other legitimate professionals. They send unsolicited messages promising high, guaranteed returns on crypto investments and pressure victims to act fast before the "opportunity" is gone. A recent example of this is the indictment of the Chairman of Prince Group, resulting in the largest-ever foreclosure action.
3. X/Twitter
X/Twitter's architecture provides multiple exploitation opportunities. The platform's real-time nature and trending algorithms make it particularly effective for rapidly amplifying campaigns. Attackers exploit viral mechanics by creating fake crisis scenarios or urgent announcements that appear to come from legitimate corporate accounts.
The speed of information spread on X/Twitter means malicious content can reach thousands of potential victims before traditional monitoring systems can detect and respond to the threat.
Examples of impersonation attacks on X/Twitter
- Link shortener abuse: Threat actors use X/Twitter's native link shortener, t.co, to hide malicious links and deliver credential phishing payloads. In a specific attack, a t.co link was embedded in a phishing email that impersonated DocuSign. When clicked, the link took the target to a landing page featuring both Adobe and Microsoft brand impersonations, with the ultimate goal of harvesting credentials through an Adversary-in-the-Middle (AITM) attack.
- Ad URL spoofing for crypto scams: A sophisticated scam exploits a vulnerability in the advertising display URL feature on X/Twitter. Attackers create ads displaying a legitimate-looking link, such as one from CNN.com, but redirect users to a malicious cryptocurrency scam website.
The business impact
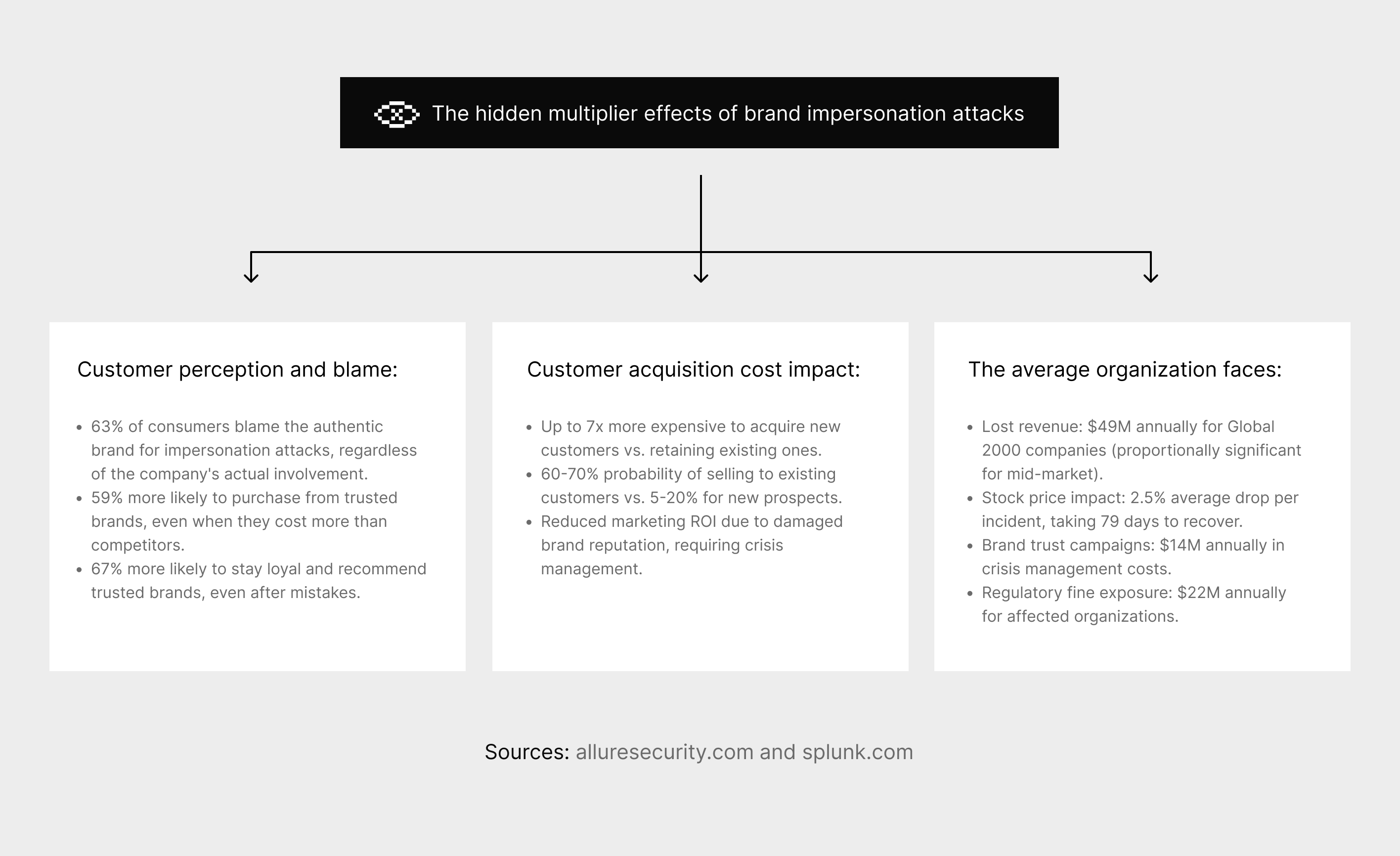
The financial impact of social media brand impersonation extends far beyond traditional breach costs. It creates a crisis of customer trust with staggering multiplier effects.
Research shows that 63% of consumers blame the authentic brand for impersonation attacks, regardless of the company's involvement. This misplaced blame is devastating because:
- It is up to 7x more expensive to acquire a new customer than to retain an existing one.
- The probability of selling to an existing customer is 60-70%, compared to just 5-20% for a new prospect.
According to Splunk analysis, the average organization faces significant financial fallout, including $49M in lost revenue annually for Global 2000 companies, a 2.5% average drop in stock price per incident, and $14M in annual crisis management costs.
Anatomy of a modern impersonation attack campaign
Modern attackers don't operate on a single platform; they execute coordinated, multi-platform campaigns that make detection more difficult. A typical playbook involves:
- Reconnaissance (LinkedIn): Attackers scrape LinkedIn for high-value targets, organizational structures, and employee lists. The platform's professional context makes it a goldmine for believable social engineering.
- Impersonation (Facebook/Meta): Using the harvested data, threat actors create fake business pages that perfectly mirror a legitimate brand, establishing a fraudulent—but credible—presence.
- Amplification (X/Twitter): The platform’s real-time nature is exploited to rapidly spread malicious links, often by manufacturing fake crisis scenarios or urgent announcements that appear to come from official corporate accounts.
- Diversification (Instagram, TikTok, Reddit): Attackers create content tailored to younger demographics on Instagram and TikTok or infiltrate Reddit communities to build credibility before launching an attack.
This coordinated approach makes detection exponentially more difficult for security teams monitoring platforms in isolation.
This multi-platform tactic demonstrates that these incidents are not isolated but usually part of a broader compromise strategy, sometimes scaling to a vast cybercrime enterprise. Within the Microsoft ecosystem alone, attempted fraud and scams have been valued at approximately $4 billion over a 12-month period.
Case Study: The LinkedIn Executive Impersonation Campaign
A recent campaign targeting mid-market technology companies illustrates the sophisticated nature of modern social media attacks.
- The Attack: Attackers scraped LinkedIn to identify C-level executives and their direct reports. They created fake executive profiles using AI-generated headshots and sent connection requests to employees. Once connected, the fake executives sent "urgent document review" requests, leading to credential harvesting pages.
- The Impact: The campaign compromised over 1,200 employee accounts across 47 organizations before it was detected. The average dwell time was 23 days. Affected organizations faced:
- $340,000 average incident response costs per organization
- 14% customer churn rate following disclosure of the breach
- 6-month recovery period for full trust restoration
A closer look at the attack chain:
- Step 1: Reconnaissance - Attackers scraped LinkedIn to identify C-level executives and their direct reports across 200+ companies in the technology sector.
- Step 2: Profile creation - Fake LinkedIn profiles were created using AI-generated headshots and scraped biographical information from legitimate executive profiles.
- Step 3: Network infiltration - The fake profiles sent connection requests to employees, achieving a 34% acceptance rate by targeting lower-level staff flattered by the apparent attention of C-level executives.
- Step 4: Credential harvesting - Once connections were established, the fake executives sent urgent requests for "urgent document review" that led to credential harvesting pages hosted on trusted domains.
- Step 5: Lateral movement - Stolen credentials were used to access corporate systems and initiate internal phishing campaigns targeting additional employees.
A CISO's action plan: Four pillars for social media defense
Defending against industrial-scale social media impersonation requires a systematic approach that anticipates attacks rather than reacting to them.
Pillar 1: Implement comprehensive social media threat intelligence
CISOs must establish continuous monitoring across all major social platforms with automated threat detection capabilities.
1. Deploy automated brand monitoring across six core platforms
Your monitoring strategy must go beyond simple keyword matching. Your automated solution should scan for not only the unauthorized use of brand names, logos, and executive imagery, but also for permutations of these assets. This includes monitoring for deceptively similar domain names used in vanity URLs and slight logo alterations designed to fool the human eye.
Advanced systems leverage AI-powered image recognition and Natural Language Processing (NLP) to identify these sophisticated impersonation attempts across social platforms.
At the very least, across Facebook, LinkedIn, X/Twitter, Instagram, TikTok, and Reddit, your monitoring must scan for:
- Unauthorized use of brand names, logos, and executive imagery
- Fake accounts impersonating company personnel
- Suspicious pages or groups using company branding
- Coordination between multiple fake accounts
2. Integrate social media intelligence with existing threat feeds
Social media threats don't exist in isolation; they're often precursors to email phishing campaigns or indicators of compromised credentials appearing on dark web markets.
Integrating social media intelligence into your broader security ecosystem provides critical context. For example, correlating a suspicious social media profile with a recently registered phishing domain or a mention on a dark web forum provides a high-fidelity signal of a coordinated attack.
By connecting disparate events in this manner security teams shift from from reacting to individual alerts to proactively dismantling entire attack campaigns — a holistic strategy directly mapping to the Direct, Respond and Recover functions of the NIST CSF.

3. Establish real-time alerting with intelligent prioritization
The sheer volume of social media mentions makes manual triage impossible. An effective strategy relies on automated, risk-based alerting. Instead of a chronological feed of every mention, alerts should be prioritized based on a calculated risk score.
Pillar 2: Create executive protection programs
C-level executives and other high-visibility personnel require specialized social media protection due to their elevated risk profile.
1. Conduct comprehensive digital footprint assessments for all executives
This process involves a thorough Open-Source Intelligence (OSINT) investigation to map out an executive's complete public-facing attack surface. This goes beyond cataloging their professional social media accounts to identify publicly available personal information — such as family members' names, location data from photo metadata, and personal interests shared on forums — that could be weaponized in a social engineering attack.
After defining the digital footprints of all persons of interest, evaluate their risk levels based on the degree of their attack surfaces.
The goal is to identify and remediate excessive public data exposure by tightening privacy settings and coaching executives on safer online practices.
2. Second, implement executive account monitoring
Continuous monitoring should be in place to detect the creation of "clone accounts" that meticulously replicate an executive's real profile. This includes tracking unauthorized accounts using their name or AI-generated deepfakes of their photos.
The monitoring should also extend to mentions of the executive in unusual contexts or on platforms they do not use, as this can be a precursor to an upcoming attack. The system should be capable of flagging suspicious login attempts and API connections to their legitimate accounts, indicating a potential account takeover in progress.
A monitoring strategy should track:
- Unauthorized accounts using executive names or photos
- Attempts to friend/connect with executive accounts from suspicious profiles
- Mentions of executives in potentially malicious contexts
3. Establish rapid response protocols
For executive impersonation incidents, including direct communication channels with platform abuse teams and legal procedures for emergency takedowns.
When an executive impersonation is detected, a pre-defined and well-rehearsed incident response plan is critical. This protocol should include established points of contact to expedite emergency account takedowns, and pre-drafted cease-and-desist templates ready for legal counsel to dispatch.
An incident response protocol must also include a clear communications plan for alerting employees, key stakeholders, and potentially the public to the impersonation attempt to prevent further damage.
Pillar 3: Automate threat response and remediation
The speed of social media threats demands automated response capabilities that can act faster than human operators.
1. Establish automated takedown workflows
Upon detecting a malicious page, the system should automatically initiate a workflow that captures digital evidence (e.g., screenshots, network logs), formats it according to each platform's unique abuse reporting requirements, and submits the takedown request via API.
Automated workflows should simultaneously:
- Submit abuse reports to platform providers
- Block malicious domains at corporate web gateways
- Alert affected employees about ongoing impersonation attempts
- Document incidents for compliance and legal purposes
Automated takedown workflows will reduce a process that once took hours of manual effort to mere minutes, significantly shrinking the window of opportunity for attackers.
2. Implement user-level automated responses
If an employee reports a social media phishing link, a Security Orchestration, Automation, and Response (SOAR) playbook can be triggered, where a suspicious URL is detonated in a sandbox for analysis, and if confirmed to be malicious, triggers a set of additional follow-up responses to thwart the attack, such as:
- lock the domain associated with the malicious link on corporate web filters;
- revoke the reporting user's active sessions;
- force a password reset;
- sweep email gateways for any other instances of the same malicious link, and
- scan for related indicators of compromise across corporate systems.
Initiating incident response procedures without manual intervention prevents a single click from escalating into an enterprise-wide breach.
3. Create feedback loops for threat intelligence improvement.
Each mitigated attack should strengthen your overall security posture. Indicators of Compromise (IoCs) — such as malicious URLs, domains, and usernames — from a confirmed social media threat should be automatically fed back into your entire security stack.
For example, a malicious domain is added to the blocklist for your DNS firewall and Secure Web Gateway, associated file hashes are added to your Endpoint Detection and Response (EDR) platform, and new detection rules are created in your SIEM.
This feedback loop ensures your defenses learn from every incident, creating a continuously improving, self-hardening ecosystem.
Pillar 4: Strengthen the last line of defense
CISOs must assume that some social media-based phishing attempts will succeed and focus on making stolen credentials worthless.
1. Mandate phishing-resistant MFA across all corporate systems.
Not all Multi-Factor Authentication is created equal. As CISA strongly advocates, organizations must move beyond bypassable methods like SMS and push notifications. Phishing-resistant MFA, based on standards like FIDO2/WebAuthn, is the gold standard.
This method, which uses hardware security keys or device-bound passkeys, creates a cryptographic bond between the user and the legitimate service. If an employee is tricked into visiting a phishing site, the authenticator will not work because the domain does not match, rendering the stolen credentials useless.
2. Implement zero-trust architecture
A zero-trust model assumes that no user or device is inherently trustworthy. Every access request must be continuously verified. This means implementing network micro-segmentation to prevent lateral movement, so a compromised account in one department cannot access sensitive data in another.
It also involves deploying User and Entity Behavior Analytics (UEBA) to detect anomalous activity, such as a user logging in from a new geographic location or accessing unusual files, which could indicate a compromised account.
3. Establish comprehensive incident response procedures
Your incident response plan must include specific playbooks for breaches originating from social media. These should detail the steps for handling a large-scale customer PII leak from a fake support page, managing public relations during a brand-damaging disinformation campaign, and ensuring compliance with regulatory notification requirements like GDPR.
These playbooks should be tested rigorously and regularly through tabletop exercises involving cross-functional teams, including security, legal, marketing, and executive leadership.
The advantage of early adoption
Mid-market CISOs have two choices: invest in social media threat monitoring now or accept the inevitability of playing defense against industrial-scale brand impersonation campaigns in the future.
For organizations that act proactively, the benefits extend beyond simple defense, creating tangible business value:
- Organizations implementing proactive threat intelligence achieve superior ROI through reduced incident response costs and faster threat mitigation
- Preemptive security measures reduce the total cost of ownership compared to reactive incident response.
- Competitive advantage through superior brand trust maintenance and customer retention
- Cyber insurance premium optimization through demonstrated external threat monitoring capabilities, meeting evolving underwriter requirements
How UpGuard enables proactive social media threat monitoring
Implementing defense against industrial-scale social media impersonation requires continuous, automated visibility across multiple platforms simultaneously. The speed of modern attacks means a malicious account can be created, used for credential harvesting, and deleted before traditional brand monitoring services even detect it.
UpGuard's new Social Media Monitoring capability is designed for this reality. Instead of periodic brand searches that miss time-sensitive threats, the platform provides:
- Automated Brand Discovery across Facebook, LinkedIn, X/Twitter, Instagram, TikTok, and Reddit, with pre-populated monitoring based on your organization's domain and existing brand assets.
- Intelligent Threat Classification that automatically categorizes detected accounts as Official, Safe, Suspicious, or Fraudulent, reducing alert fatigue while ensuring genuine threats receive immediate attention.
- Unified Threat Feed Integration that correlates social media impersonation attempts with dark web credential leaks and attack surface vulnerabilities, providing complete context for threat prioritization.
- Guided Remediation Workflows that provide step-by-step takedown procedures for each platform, streamlining response for lean security teams without specialized social media expertise.

This proactive approach provides the critical early warning needed to disrupt attacks before they reach employees or customers, neutralizing threats at the source rather than responding to successful compromises.
To learn more, get a tour of the UpGuard platform.