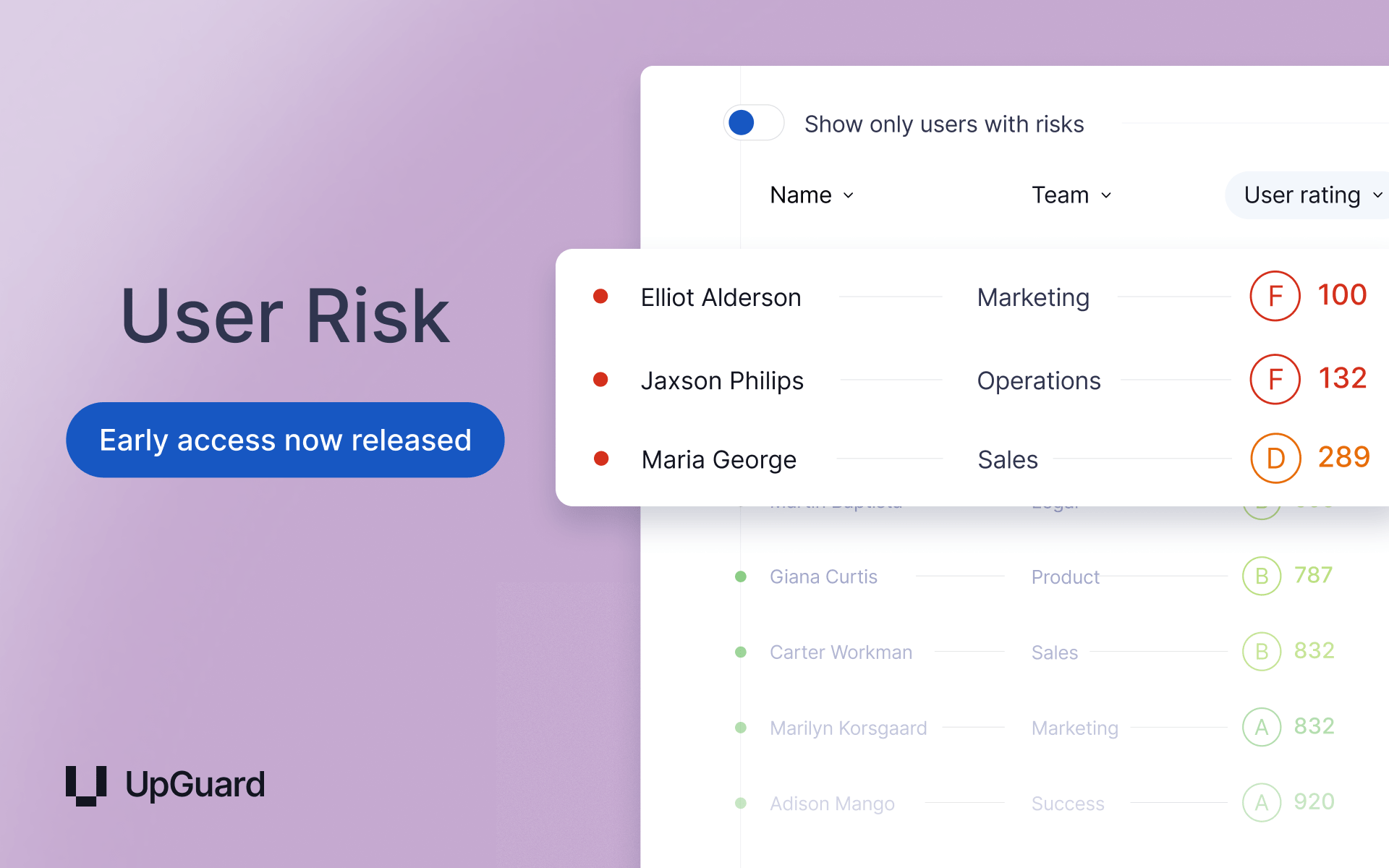
Now released in limited Early Access: User Risk
UpGuard’s new User Risk product gives you a single, unified platform to manage the complexity of human risk. Our AI Analyst unifies identity, behavior, and threat signals to give you a comprehensive picture of your workforce risk, while contextual coaching helps you build a stronger security culture and transform your employees into a proactive line of defense.
Here’s how User Risk transforms your approach to managing human risk:
- AI Analyst: Automatically synthesizes thousands of signals into a prioritized action plan, helping your team focus on the threats that matter most and move beyond manual, time-consuming analysis.
- Unified Risk Signals: Consolidates disparate human risk signals – like unauthorized SaaS and AI usage, compromised credentials, and over-privileged permissions – into a single, unified view that’s updated daily.
- Real-Time Behavioral Coaching: Moves beyond ineffective training by delivering educational "nudges" directly within an employee's workflow, building secure habits at the exact moment of a risky action.
- Comprehensive Risk Discovery: Utilizes a browser extension and directory integrations to discover your true SaaS and AI footprint, including non-SSO apps that other tools miss.
- Unified User Risk Profile: Centralizes all discovered risks for each user into a single profile, allowing for targeted intervention and a clear view of your riskiest individuals and teams.
To learn more, visit the product overview page or contact your Customer Success Manager.
Pre-set assessment scope by vendor tier in Security Profile
You can now right-size vendor assessments by pre-setting scope with Security Profile control templates. Once set, these templates automatically apply across your vendor ecosystem based on vendor tier. Use our recommended tiered templates or tailor your own from the control library to match the exact scope you need. With an expanded security framework offering more comprehensive controls and checks, you get greater flexibility and precision when building assessments. Plus, the gap questionnaire is now dynamically generated from the applied template and pre-filled with existing evidence, so vendors only need to address what’s truly missing.
Ability to tune AI-commentary for Instant Risk Assessments
We’ve enhanced our AI Instant Risk Assessment commentary to give you more control. You can now fine tune the AI to suit your needs by setting the target audience (e.g. technical, non-technical), choosing the level of detail, and even entering custom prompts for specific use cases. Create the perfect report first time, faster than ever.
Vendor Risk AI analyst insights
We've added helpful, AI-generated insights to every vendor's summary page. Get an instant read on a vendor’s security posture and potential gaps, along with smart, actionable recommendations for next steps. The AI analyzes all active evidence including scan data, documents, questionnaires, and incidents to give you a comprehensive and immediate understanding.
More vendor evidence added to the Security Profile
We've added over 1,500 new public documents for more than 200 of our most-monitored vendors. These documents are now available as evidence in Vendor Risk and have been pre-scanned against the Security Profile. This update saves you time and effort by reducing the need to chase down evidence, so you can get to assessing your vendors faster.
Other improvements
- We’ve changed the description of B grade to Organization has reasonable security controls in place but could have gaps in their security posture to better reflect risk level.
- We’ve added some additional detail to the (excel) Vendor Risk assessment summary report including Portfolio, Grade and Assessment year.
- This release includes a number of bug fixes.

Improvements to remediation workflow
We’ve made it easier to track and manage remediation requests. You can now revert a remediation request from "Awaiting Review" back to "In Progress" if the vendor's response is incomplete or insufficient. Previously, this status change wasn’t possible. Doing so will generate a notification to the recipient to take further action on unresolved risks. This ensures a more flexible and effective remediation workflow, empowering you to ensure all identified risks are thoroughly addressed. This improvement is available for both Vendor Risk and Breach Risk remediation requests.
Other improvements
- We’ve made improvements to the evidence selection modal in the Vendor Risk Security Profile, improving clarity on document names, types, statuses and dates
- This release includes a number of bug fixes
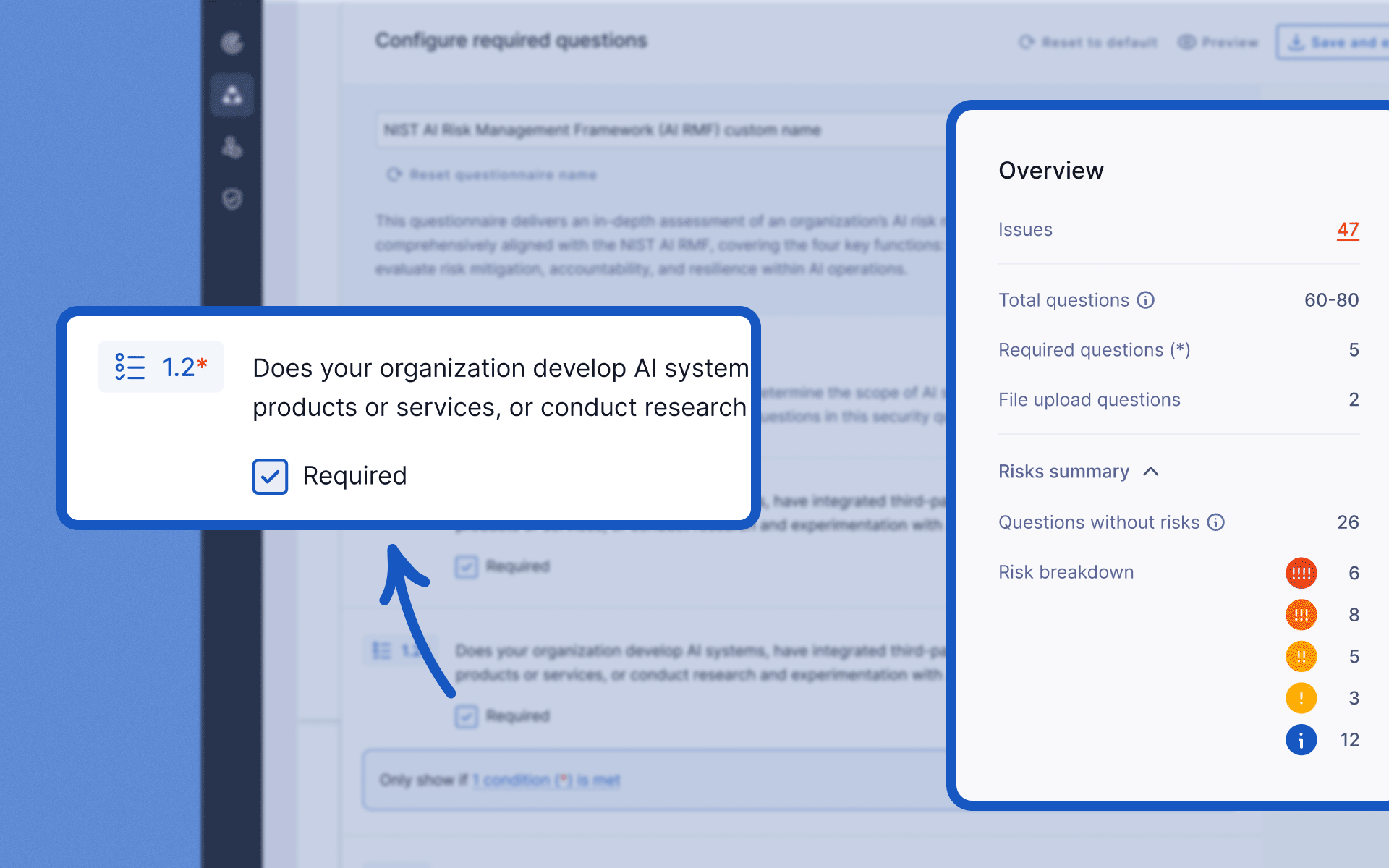
Configure questions as required
To help get the information you need from vendors, you can now mark questions as required in both default and custom questionnaires. This can be done in the Questionnaire Library when creating a new custom questionnaire or when editing an existing questionnaire.
Required questions are also highlighted to vendors in the questionnaire viewer, making it clear what needs to be answered before they can submit their response.
We’ve also introduced an Overview section in the questionnaire builder to give you better visibility into the breakdown of questions and potential risks that could be flagged.
To learn more see Edit and build questionnaires.
Customizable vendor attribute update notifications
Users can now create custom notifications triggered by updates to their vendor's attributes. This allows for proactive monitoring of critical vendor information changes, enabling timely responses and improved risk management.
Granular Trust Page document access control
Trust Page administrators can now decide exactly which individual documents and questionnaires a requester can access, instead of turning access protection on or off for the entire Trust Page. This allows for more granular, per-resource access controls on Trust Pages, making it easier for admins to share evidence only with the parties that truly need it.
Other improvements
- Users can now sort and compare vendors more easily with the addition of Industry and Headquarters columns on the Vendors page and in the Excel export.
- This release includes a number of bug fixes.
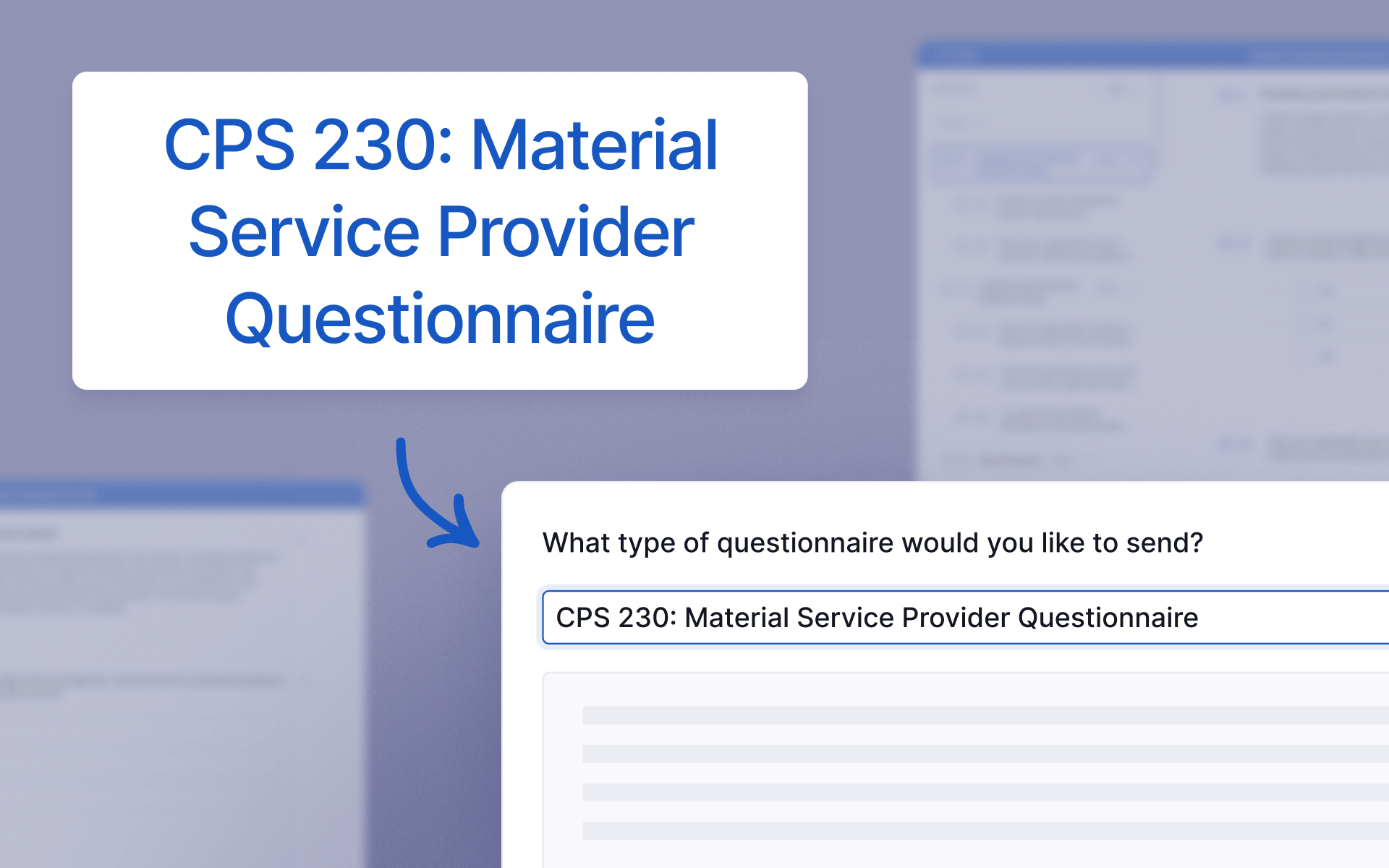
New questionnaire: CPS 230 Material Service Provider
We’ve added a CPS 230: Material Service Provider Questionnaire. This questionnaire is designed to help APRA-regulated Australian financial services customers identify and assess material service providers and their capacity to support your critical operations and obligations to comply with CPS 230. Learn more
Other improvements
- To make it easier to see the full list of documents available for a vendor, UpGuard-sourced public documents are now stored in the vendor’s Additional Evidence page.
- The list of all risks in Instant Risk Assessments is now filterable, making it easier to search, sort, and review relevant risks before finalizing your report.
- You can now export the “You and your vendors” tab from Incidents and News.
- Added “click to copy” functionality to risk details across Breach Risk and Vendor Risk.
- This release also includes a number of bug fixes.

Protect the documents in your Trust Page with watermarks
Add an extra level of protection for the PDFs in your Trust Page with our new watermarking capability. Downloaded PDFs can now include a watermark displaying the downloader's company domain, name, email address, and download timestamp, providing greater control over your shared information. This feature can be enabled in your Trust Page settings. Learn more
Improvements to AI document scanning and risk assessment commentary
To improve the quality of results we've made improvements to AI document scanning in the Security Profile and AI Autofill. Improvements include:
- Improved citation handling, focusing on citation quality
- Improved prompts to handle specific nuances of some individual controls and control families
- Upgraded from GPT-4o to GPT-4.1
We've also made improvements to AI risk assessment commentary to reduce the likelihood for self-contradictory statements in the risk assessment narratives.
Improved domain list filtering in Breach Risk and Vendor Risk
You can now view active and inactive domains even after applying filters in the Domains UI. Previously, these lists were only available when no filters were applied—this update restores that flexibility and makes it easier to analyze filtered domain sets.
Other improvements
- This release includes a number of bug fixes

Now Released in Early Access: Threat Monitoring for Breach Risk
UpGuard’s new Threat Monitoring features give you real-time visibility into threats across the open, deep, and dark web. Our AI Threat Analyst continuously scans for signs of data exposure and malicious activity linked to your organization, helping you detect and respond before attackers can act.
Here’s how Threat Monitoring takes your external risk detection to the next level:
- AI Threat Analyst: Automatically triages findings and provides clear remediation guidance to help your team act faster.
- Broad threat coverage: Continuously monitors multiple attack vectors across open, deep, and dark web sources for early warning signs.
- Prioritized and contextualized: AI Threat Analyst filters out noise and enriches results with relevant context so your team can focus on high-confidence threats.
- Transform-based monitoring: Lets you define what to track, such as brands, domains, IPs, emails, or product names, for targeted threat detection.
- Collaborative investigation workspace: Centralizes alerts, context, and actions to support faster triage and investigation across teams.
To learn more, see What is UpGuard Breach Risk Threat Monitoring?
These features are available to customers in our early access program. If you’d like to learn more or be notified when they become generally available, please contact your UpGuard Customer Success Manager.
We’ve made it easier to monitor vendors
Adding and managing vendors is now significantly easier. The improved vendor monitoring flow provides a clear, guided experience, allowing you to add multiple vendors at once, search our database, or add vendors without a web presence with minimal information.
Subscribe to Trust Page updates
Trust page viewers can now subscribe to receive email notifications of important updates. Trust page administrators can also manage subscribers directly within the Trust Page settings, making it easier to communicate important security and compliance updates to your customers and prospects. To learn more, see How to Create Your Trust Page.
Other improvements
- This release includes a number of bug fixes

Add news and other updates to your Trust Page
Trust Page administrators can now add updates to their Trust Pages, keeping customers informed about important events and news, such as communicating a new certification or other compliance milestone; promoting a change to a policy; or to inform customers in the rare event of an outage or breach. These updates are immediately visible on the published Trust Page and Vendor Risk users can also subscribe to their vendors’ Trust Page updates.
Questionnaire attachments automatically added to additional evidence
Questionnaire attachments submitted by vendors are now automatically added to the Additional Evidence section. This streamlines the assessment process and eliminates the manual step of converting attachments, making it faster and easier for you to include these documents in your security profile and risk assessments.
Minimum questionnaire completion rates
Users can now set a minimum completion percentage for questionnaires in Settings. This ensures vendors provide sufficiently complete responses, reducing the need for follow-up and improving assessment accuracy. If a vendor attempts to submit a questionnaire below the set threshold, a message will prompt them to answer additional questions before submission.
Improved navigation for settings pages
The Settings pages now use a consistent sidebar navigation, matching other areas of the application. This improves navigation and provides a more unified user experience. The Settings menu has also been reorganized for better clarity and includes new sections for Subsidiary Management and Vendor Onboarding.
Other improvements
- Support for ISO42001 badges on Trust Pages
- Added automated scan and evidence rating breakdown to the Vendors page and Excel export enabling for more comprehensive vendor comparison and analysis
- This release includes a number of bug fixes

Risk Assessment Summary Report now available in Excel format
You can now download the Risk Assessment Summary Report in Excel. The report provides a snapshot of assessment statuses across your vendor portfolio and is organized into three sheets—In Progress, Completed, and Not Assessed—to simplify analysis. We've also improved the sorting for easier navigation.
Other improvements
- Resolved an edge case affecting document states in draft questionnaires
- General bug fixes and performance enhancements

Expanded News & Incidents coverage
We've enhanced News and Incidents coverage to include the Securities and Exchange Commission (SEC) as a source. The SEC tracks regulatory outcomes of data breaches and broadens our coverage of US cybersecurity impacts.
Trust Page tips and tricks
We've made several updates to help you edit and publish your Trust Page. There’s a new “Get started guide” with information to guide you through the process of setting up your Trust Page, as well as the introduction of tips after your page is published. The Settings page has also been redesigned, making it easier to add a custom domain, NDA, and configure your access settings. Visit your Trust Page to see these changes.
Other improvements
- Resolved problems with case sensitivity in security links and re-issuing access invites.
- Improved Vendor Risk Fourth party export to make it clearer which vendors are using which products.
- Added page numbers and question numbers to citations in the Vendor Risk Security profile to help provide more context.
- Improved warnings when questionnaires and documents used in Vendor Risk security profile and risk assessments are deleted or archived.
- Detected Products export functionality now includes the vendor's score and an indication of whether the vendor is currently monitored within Vendor Risk.
- This release includes a number of bug fixes.

Vendor Risk AI-Powered Security Profile (Beta) – Ongoing Enhancements
We’re continuing to roll out incremental improvements to the Vendor Risk AI-powered Security Profile (Beta) to give you greater flexibility, control, and clarity.
- Custom Domain & IP selection: You can now customize the domains and IPs used in a vendor’s security profile. Your selection is saved between sessions and automatically applied to the Instant Risk Assessment, helping you tailor assessments to specific vendor engagements and use cases.
- Excel document support: You can now upload and scan Excel documents as part of the evidence used in the security profile.
- Manual check management: We’ve made it easier to manage checks and citations—users can now manually mark checks as "met" to better reflect their evaluation.
- Add comments to all checks: Comments can now be added to both passed and unmet checks (previously, comments were only supported for identified risks).
- Updated rating logic: The Security Profile rating will now default to the automated scanning score when no evidence has been provided. Once evidence is added, the rating will automatically update to reflect the combined impact of the automated scanning and evidence, against the Security Profile control set.
More enhancements to come in upcoming releases.
New in Breach Risk: Risk Waivers for Subsidiaries
We’ve introduced Risk Waivers for Subsidiaries, a powerful new feature in Breach Risk that gives organizations greater control and flexibility in managing risk across their subsidiaries. With this enhancement, you can now create private risk waivers for risks associated with any of your subsidiaries. These waivers are visible only within your organization and ensure your internal risk posture reflects the controls and context you manage centrally.
New in Trust Exchange: Trust Page enhancements
We’ve rolled out a number of improvements to Trust Pages in this release:
- Trust Page users can now add specific badges for their CSA STAR level, plus new badges for CSA TCP, CREST and URAC, so businesses who adopt these frameworks and standards can reflect that on their Trust Page.
- Downloads data is now available in the Trust Page access log, giving you deeper insight into the documents that your prospects and customers find most valuable.
- A preview mode for Trust Pages is now available, so you can see what your page will look like from an outside perspective prior to publishing.
- You can now customize your security link titles on your Trust Page via Settings > Content Library.
- We’ve made UI improvements to the Trust Page share modal, published status badges and settings page.
Other improvements
- For Vendor Risk customers who want to be notified when their vendors make changes to their Trust Page, we’ve made improvements to the notification, which you can enable via Home > Manage Notifications > Configure custom notifications.
- We’ve added a new Vendor Risk custom attribute type URL so you can now add clickable links as custom attributes.
- Users can now sort by percent complete when reviewing remediation requests in both Vendor Risk and Breach Risk.
- We’ve added SOC3 report as default document type to Vendor Risk Additional Evidence.
- This release includes a number of bug fixes.

Add a custom domain for your Trust Page
We’re introducing custom domain support for all Trust Pages, so that you can deliver a fully branded experience that builds trust and reinforces credibility with your prospects and customers. Paired with previous custom branding enhancements, your Trust Page can now feel like a natural extension of your existing web presence. This comes at no additional cost, and is available on all Trust Pages. Get started for free, or learn more about this feature.
Export vendor reports into Word documents
We’ve added support for generating editable versions of vendor reports, giving you greater flexibility to tailor content before sharing. You can now export the Vendor Summary, Vendor Detail, Vendor Risk Assessment, and Security Profile Risk Assessment reports in Microsoft Word format, making it easier to customize findings, add context, or apply your own branding. This option is in addition to the PDF option when generating reports.
Detection for exposed Llama.cpp instances
We have expanded our external attack surface monitoring to detect exposed llama.cpp instances, a popular open-source framework for running LLMs (eg Deepseek, LLaMa 2, Qwen…) locally. This enhancement helps organizations identify unintentionally exposed AI infrastructure, reducing the risk of unauthorized access to self-hosted language models and maintaining a secure AI deployment footprint.
PCI DSS Questionnaires
We’ve added a complete set of questionnaire templates to the Vendor Risk questionnaire library, aligned with the Payment Card Industry Data Security Standard (PCI DSS) v4. Each of the 10 official SAQ types is now available as a pre-built questionnaire ready to assess organizations against the requirements of PCI DSS. Note that these questionnaires are not a substitute for an Attestation of Compliance (AOC) or Report on Compliance (ROC).
Other improvements
- We’ve made it easier to waive risks in the Vendor Risk Security Profile (beta). You can now easily waive risks identified through document scans as soon as they are identified.
- This release includes a number of bug fixes

Open Ollama server detection
UpGuard’s latest update to Breach Risk and Vendor Risk improves external attack surface monitoring by detecting exposed Ollama instances—self-hosted large language models that become vulnerable when publicly accessible via port 11434. This new capability helps organizations prevent unauthorized access, safeguard AI assets, and mitigate the risk of data theft or model tampering.
Improvements to Trust Page questionnaires
It’s now easier to add security questionnaires to your Trust Page, with a redesigned module that streamlines the process and makes it easier to share your responses with prospects and customers. You can now import questionnaires directly on the Trust Page, as well as more easily access details about your Trust Page questionnaires via Answer Questionnaires > Public questionnaires.
Other improvements
- We’ve added company logos to Vendors in Vendor Risk.
- We’ve changed the handling of informational risks in the Vendor Risk Security profile. Details of informational risks are included but do not impact the control status or security rating.
- This release includes a number of bug fixes.
Sign up for our newsletter
Free instant security score
How secure is your organization?
- Instant insights you can act on immediately
- Hundreds of risk factors including email security, SSL, DNS health, open ports and common vulnerabilities

