NIST compliance in 2026: A complete implementation guide
Aligning with a NIST framework is a strategic initiative for any organization serious about cybersecurity. It provides a clear roadmap to defending against sophisticated supply chain attacks, meeting evolving regulatory demands, and managing growing cyber risk exposure from third-party vendors.
This guide explains the core NIST frameworks and provides a practical, 5-step implementation plan for building a resilient and defensible security program with a NIST standard.
What is NIST compliance?
The National Institute of Standards and Technology (NIST) is a non-regulatory U.S. government agency that develops technology standards and guidelines to drive innovation and industrial competitiveness. As part of its mission, NIST creates and promotes standards and best practices for cybersecurity that are recognized globally as the gold standard for cyber threat defence.
It is crucial to understand that a certification does not determine NIST compliance. When an organization claims that they are NIST compliant, they mean that they have implemented the recommended controls and standards from a relevant NIST framework (like NIST 800-171 or the NIST CSF) and can demonstrate this alignment through established processes and continuous monitoring, all verified by comprehensive documentation, which typically includes a:
- System security plan (SSP): Describes how each relevant control is implemented.
- Plan of action & milestones (POAM): Tracks remediation of deficiencies and all supporting security policies, procedures, and training records.
This documentation serves as dynamic, ongoing proof of implemented security controls, demonstrating continuous alignment with a specific NIST framework — a different approach to a static award, confirming alignment at a single point in time.
Compliance with a NIST standard is an ongoing process of demonstrating alignment, not a static award representing alignment at a single point in time.
Read our post explaining the difference between compliance and audits to deepen your understanding of the unique nature of NIST compliance.
Who needs NIST compliance?
NIST compliance is mandatory for business partners of the U.S federal government, particularly those handling sensitive or Controlled Unclassified Information (CUI). There are two primary groups in this category:
- Federal agencies: All U.S. federal agencies are required by law (the Federal Information Security Management Act) to follow NIST SP 800-53 guidelines.
- Government contractors: Any organization part of the government supply chain, especially the Defense Industrial Base (DIB), must comply with specific contractual clauses like DFARS 252.204-7012, which mandates adherence to NIST SP 800-171 to protect controlled unclassified information (CUI).
Many industries (especially highly regulated ones) outside the government sector also align with NIS frameworks, usually voluntarily, to bolster security postures against a proven cybersecurity standard.
Sometimes, alignment with a NIST framework supports compliance with industry-specific regulations. Here are some examples across the most highly-regulated industries:
Healthcare sector
- The U.S. Department of Health and Human Services (HHS) provides an official "crosswalk" that maps the requirements of the HIPAA Security Rule directly to the NIST Cybersecurity Framework, serving as a practical guide for compliance.
- The HIPAA Safe Harbor Law directs regulators to consider an organization's use of "recognized security practices," specifically NIST-based frameworks, when determining fines and audits after a data breach.
- The Health Industry Cybersecurity Practices (HICP), developed by HHS's 405(d) program, offers voluntary, NIST-aligned guidance tailored to help healthcare organizations mitigate common cyber threats.
- NIST publishes specific cybersecurity guidance for medical device manufacturers and providers to manage the risks associated with connected health technologies
Learn how UpGuard protects the healthcare sector from third-party risks >
Financial sector
- The FFIEC (Federal Financial Institutions Examination Council), which sets standards for U.S. financial institutions, uses the NIST Cybersecurity Framework (CSF) as the foundation for its Cybersecurity Assessment Tool (CAT).
- The influential New York Department of Financial Services (NYDFS) Part 500 cybersecurity regulation is structurally modeled after the NIST CSF's core functions (Identify, Protect, Detect, Respond, Recover).
Learn how UpGuard protects the finance sector from third-party risks >
Energy and utilities sector
- The U.S. Department of Energy actively promotes the NIST CSF as a foundational resource for energy companies to strengthen their cybersecurity posture.
- While the NERC CIP (Critical Infrastructure Protection) standards are mandatory, many utilities map their CIP compliance activities back to the NIST CSF to communicate risk more broadly and holistically manage security.
- CISA (Cybersecurity and Infrastructure Security Agency) consistently recommends the NIST CSF as a best-practice framework for all critical infrastructure sectors, including energy and utilities.
Technology sector
- Technology companies, especially SaaS and cloud providers, adopt the NIST CSF to meet the security due diligence requirements of their enterprise customers, particularly those in regulated industries like finance and healthcare.
- Any Cloud Service Provider wishing to sell to the U.S. federal government must meet the security standards of the FedRAMP program, which are based directly on NIST Special Publication 800-53.
- In response to heightened supply chain threats, software companies are increasingly adopting the NIST Secure Software Development Framework (SSDF, SP 800-218) to build security into their product lifecycle and meet new federal procurement standards.
- The industry is turning to new NIST guidance for cutting-edge fields. For example, companies developing or deploying artificial intelligence adopt the NIST AI Risk Management Framework to ensure responsible and trustworthy systems.
- Many tech companies use the NIST CSF as the underlying control framework to prepare for other security audits, such as SOC 2, as there are official mappings between the frameworks.
Learn how UpGuard protects the technology sector from third-party risks >
For most organizations, NIST provides a voluntary set of best practices, controls, and guidelines for managing cybersecurity risk.
The three key NIST frameworks explained
The three primary NIST frameworks that form the core of compliance conversations are:
- Cybersecurity framework (CSF): A high-level, flexible framework for managing cyber risk that is adaptable to any organization.
- Special publication (SP) 800-53: A comprehensive catalog of security and privacy controls primarily for federal information systems.
- Special publication (SP) 800-171: A set of controls for protecting sensitive information in non-federal systems, particularly for government contractors.
Learn how UpGuard supports compliance with NIST CSF >
These frameworks are related but serve distinct purposes. Choosing the right one depends on your organization's obligations, customers, and risk appetite.
1. NIST cybersecurity framework
The NIST CSF is the most accessible starting point for any organization looking to formalize its cybersecurity risk management program. The recent update to version 2.0 has expanded its scope and added the critical new function, Govern, making it more comprehensive than ever.
The six core functions of NIST CSF 2.0:
- Govern: The new centerpiece function. It focuses on establishing and monitoring the organization's cybersecurity risk management strategy, expectations, and policy.
- Identify: Understand your assets, data, risks, and vulnerabilities to manage them effectively.
- Protect: Implement safeguards to ensure the delivery of critical services.
- Detect: Implement activities to identify the occurrence of a cybersecurity event.
- Respond: Take action regarding a detected cybersecurity incident.
- Recover: Implement plans for resilience and restore impaired capabilities or services.
2. NIST SP 800-53
Think of NIST 800-53 as the comprehensive "encyclopedia" of security controls. It is highly detailed and prescriptive, providing a vast library of controls that federal agencies must implement. Its key concepts include:
- Control families: Controls are organized into 20 families, such as access control (AC), incident response (IR), and supply chain risk management (SR).
- Control baselines: Organizations select a baseline (Low, Moderate, or High) based on the security impact level of their systems, which dictates the minimum set of required controls.
Refer to this NIST 800-53 checklist for an overview of the requirements for achieving alignment.
3. NIST SP 800-171
NIST 800-171 is an essential framework for any non-federal organization (primarily government contractors) that handles controlled unclassified information (CUI). Its importance cannot be overstated for businesses within defense and federal civilian agency supply chains.
- The link to 800-53: Its 110 security requirements are a subset derived directly from the SP 800-53 moderate baseline, tailored for non-federal environments.
- The CMMC connection: Compliance with SP 800-171 is the foundational requirement for achieving the Department of Defense's Cybersecurity Maturity Model Certification (CMMC).
Refer to this NIST 800-171 checklist for an overview of the requirements for achieving alignment.
How to support NIST compliance in 7 practical steps
This roadmap is a continuous improvement cycle, not a one-time project. The following framework can be used alongside your choice of compliance software.
1. Assess your current security posture
Define your scope or "authorization boundary" — the full extent of the people, processes, and technologies subject to your chosen NIST framework (refer to the table above).
- Identify your authorization boundary: Clearly document which assets are in scope. This includes servers and endpoints, network segments, cloud environments (IaaS, PaaS, and SaaS), operational technology (OT) systems, and specific applications that process, store, or transmit sensitive data. For a contractor seeking CMMC certification, this boundary contains all assets that handle CUI.
- Map your third-party dependencies: List every third-party vendor and service provider whose products or personnel with access to systems or data. This includes your cloud service provider (e.g., AWS, Azure), managed service providers (MSPs), and SaaS applications. It is critical to identify these vendors since they're an extension of your attack surface. This effort is critical, since your third-party network directly impacts compliance with standards like NIST 800-53.
2. Classify information assets and systems
Once your scope is defined, the next step is to classify your information and systems to understand their value and required level of protection. This begins with a thorough data discovery and classification process to identify each sensitive data type — Controlled Unclassified Information (CUI), or Personally Identifiable Information (PII), and where it resides at rest and in transit.
The sensitivity of the data a system processes directly dictates its criticality. Using the Federal Information Processing Standards (FIPS 199) standard, formally categorize each system by assessing the potential impact (Low, Moderate, or High) on its Confidentiality, Integrity, and Availability (C-I-A) if it were compromised.
This categorization is not just an administrative exercise; it determines the specific baseline and rigor of security controls you will implement.
3. Conduct a gap analysis
A gap analysis is a systematic, control-by-control comparison of your current security posture against the requirements of your chosen NIST framework.
Collect evidence of current controls
You must gather proof of how you are currently meeting (or not meeting) each control. This is a multi-faceted effort that involves:
- Documentation review: Assembling and reviewing existing policies, procedures, network diagrams, system configurations, and incident response plans.
- Personnel interviews: Speaking with system owners, administrators, developers, and security personnel to understand how processes work, which often differs from how they are documented.
- Technical verification: Involves using tools to validate configurations. This could involve running vulnerability scans, reviewing firewall rule sets, and checking access control lists in key applications and cloud environments.
Map controls to the framework
Create a matrix using a spreadsheet or a risk management platform. List every control requirement from your target framework (e.g., the 110 controls in NIST SP 800-171) and map your collected evidence against each.
For each control, assign a status. A common scoring system is:
- Implemented: The control is fully in place, documented, and operating as intended.
- Partially implemented: Some aspects of the control are met, but significant deficiencies exist.
- Not implemented: The control is missing entirely.
- Not applicable (N/A): The control does not apply to your specific environment (this must be justified).
When evaluating a vendor's alignment with a NIST standard, the vendor can initiate this step in a questionnaire. Here's an example from our free NIST 800-53 risk assessment template.
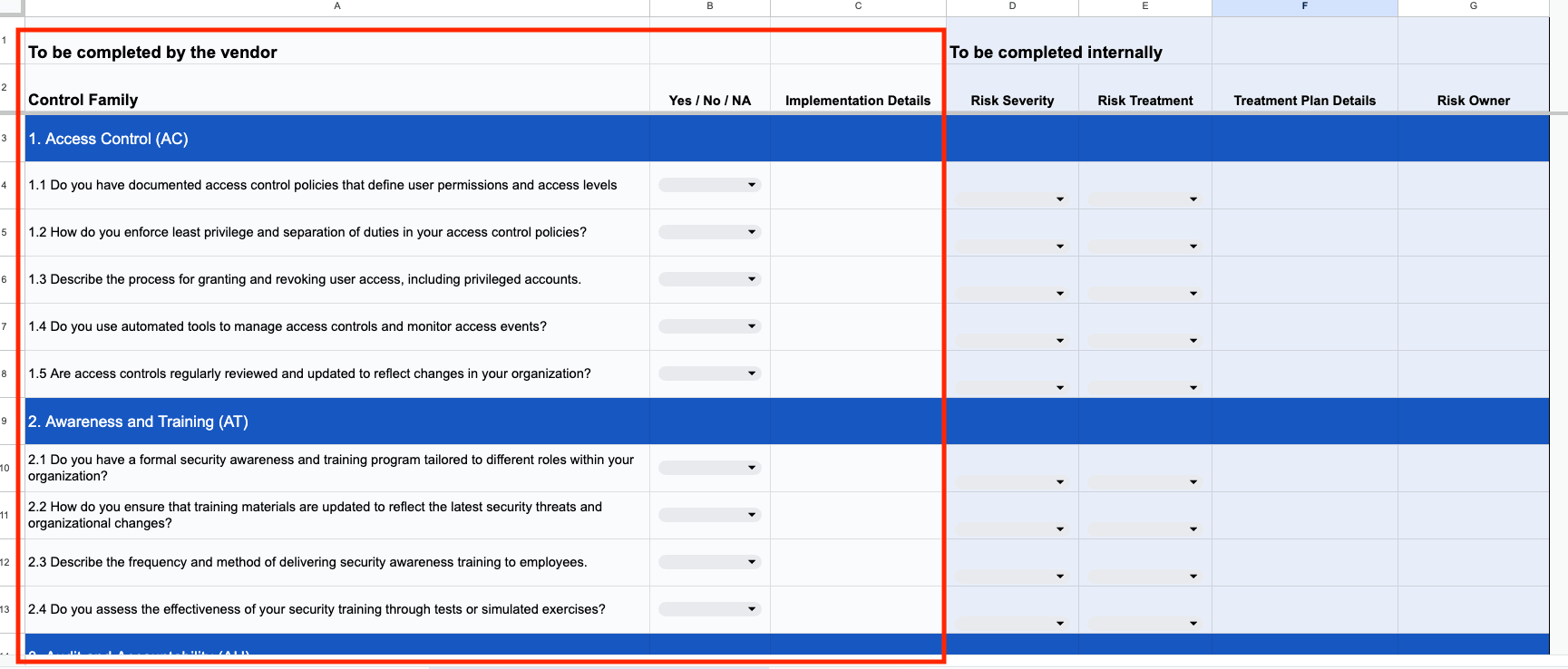
For tracking vendor alignment, we created some free templates. Download the template for your preferred NIST standard from the list below:
The final output of this process is a detailed report that precisely identifies every control gap. This report becomes the primary input for your remediation plan, outlined in a risk assessment, often called a plan of action & milestones (POAM).
4. Perform a risk assessment
A gap analysis tells you what controls are missing; a risk assessment tells you how much it matters. By prioritizing control gaps based on the threat they pose to your organization, this step transforms your compliance exercise into a true compliance management strategy.
Instead of fixing all 100+ gaps at once, a risk assessment helps you focus your limited time and resources on the deficiencies that present the greatest danger.
For detailed guidance, refer to NIST's risk assessment guidelines, which can be applied to any NIST framework.
According to NIST's guidelines, the key steps in a risk assessment are:
- Threat identification: Identify relevant threat sources and events. Threat sources could be adversarial (e.g., nation-state actors, cybercriminals) or non-adversarial (e.g., system failures, or human errors facilitating security incidents). Tie each identified source to a threat event, likely adversarial actions to take place (e.g., phishing campaign, ransomware deployment, DDoS attack, or insider breach).
- Vulnerability identification: Your gap analysis report is the primary input here. A missing or weak control is a vulnerability. Technical vulnerability scan results (e.g., CVSS scores for unpatched software) supplement this.
- Likelihood determination: For each identified risk (a threat exploiting a vulnerability), determine the likelihood of it occurring. This is often ranked on a scale (e.g., High, Medium, Low) based on threat actor capability, intent, and the effectiveness of your existing controls.
- Impact analysis: If the event occurs, what is the level of harm to the organization's operations, assets, or individuals? Use the FIPS 199 criteria (Confidentiality, Integrity, Availability) to assess the impact as High, Medium, or Low.
- Risk determination: Combine the likelihood and impact assessments (e.g., using a risk matrix) to assign an overall risk level to each identified gap. A high-likelihood, high-impact event becomes your top priority for remediation.
UpGuard streamlines the threat and vulnerability detection process according to NIST's assessment guidelines, preparing a rich dataset of cyber risk insights for analysis in an in-built risk assessment workflow.
Here's how the UpGuard platform can be leveraged in different risk scenarios:
5. Implement and remediate controls
With your gaps identified and risks prioritized in a risk assessment report, this phase transitions your program from analysis to active remediation. The cornerstone of this effort is a formal plan of action & milestones (POAM), which serves as your risk-based roadmap for closing security gaps.
This is not just a task list; it is a strategic document that details each weakness, the planned remediation, required resources, a realistic completion timeline, and the assigned owner. It ensures that the highest-risk items from your assessment are tackled first.
With this roadmap in place, the focus shifts to deploying a defense-in-depth strategy by implementing three types of controls:
- Technical controls, like multi-factor authentication and data encryption;
- Operational controls, such as security awareness training and incident response drills, and
- Management controls that encompass overarching risk governance policies.
This systematic implementation, tracked via the POAM, measurably closes your security gaps and strengthens your overall defensive posture.
6. Document policies and evidence
To prove compliance, you must be disciplined with your documentation, a process centered on a system security plan (SSP) — a comprehensive document that serves as the official narrative of your NIST-aligned security program.
The SSP must detail exactly how your organization implements every applicable control in your chosen NIST framework, providing auditors with a clear and complete picture of your NIST compliance efforts.
If it isn't documented, it didn't happen.
While the SSP describes your program, you must also maintain a body of evidence to prove its claims. This involves systematically collecting and storing artifacts like server logs, vulnerability scan reports, policy version histories, and staff training records. This evidence repository must be continuously updated (not just thrown together before an audit) as it serves as the definitive, ongoing proof of a security posture defined by NIST alignment.
By hosting some of these documents on a Trust Page, they can also be used as public-facing evidence of your organization's NIST compliance efforts — an effort that could draw the attention of prospective business partners who prioritize high security standards in their vendor relationships.

7. Monitor, measure, and improve continuously
This final phase focuses on maintaining vigilance through continuous security monitoring, where you implement automated tools and processes to watch for configuration drift, new vulnerabilities, and deviations from your established security baseline in real-time.
This vigilance must extend beyond your perimeter because your level of NIST compliance is inextricably linked to your supply chain cyber risks.
You must assess and monitor the security posture of critical third parties on an ongoing basis, proactively addressing vendor security risks before they impact your compliance efforts, or worse, develop into a costly breach.
These internal and external monitoring activities create a dynamic feedback loop, feeding new data into your risk assessment process and transforming compliance into a living cycle of continuous improvement.
Compliance is a program, not a project. It erodes the moment you stop paying attention.
NIST compliance without the complexity
Implementing a NIST framework is a significant undertaking, but the rewards of enhanced security, trust, and business enablement make the effort worthwhile.
Implementing and maintaining NIST alignment can seem daunting, but it doesn't have to be a manual, spreadsheet-driven nightmare. UpGuard simplifies this journey by automating security assessments, providing continuous visibility, and streamlining Vendor Risk Management.
Watch this video to learn how UpGuard leverages AI to streamline risk assessments aligned to NIST frameworks and other popular cyber standards.
FAQs about NIST compliance
How can you become NIST compliant?
NIST compliance is a continuous cycle of demonstrating alignment with all applicable controls of your chosen NIST framework. Compliance evidence is tracked in a System Security Plan (SSP), a document explaining how each relevant control is implemented.
Why is third-party risk so important for NIST compliance?
Third-party risk is critical for NIST compliance because the frameworks view security holistically, treating your supply chain as an extension of your security perimeter, where a vendor's weakness becomes your liability.
NIST provides a structured methodology and a standard set of controls to consistently assess and manage these external risks. Neglecting this part of your attack surface makes it impossible to achieve the comprehensive cyber threat defence strategy promoted by all NIST frameworks.
What are the top benefits of NIST compliance?
The primary benefits include: enhanced security and resilience against cyberattacks; winning contracts (especially federal and enterprise); building demonstrable trust with customers and partners; and implementing a structured, world-class methodology for managing cyber risk.
What are the most common challenges with NIST compliance?
The most common challenges are the complexity of understanding which controls apply, resource constraints (budget, personnel, and expertise), tracking framework alignment in real-time, and maintaining audit-ready documentation.