Salesloft Drift Breach: What Happened and How Does It Affect Me?
- Updated September 9, 2025
UPDATE: Salesforce/Salesloft Integration Is Restored
As of a recent update, the integration between the Salesloft platform and Salesforce has been restored. Customers will be contacted directly by the Salesloft Customer Success team to assist with the data reconciliation process before the Salesforce sync is re-enabled
A forensic investigation by Mandiant has shed new light on the Salesloft Drift security incident. After being hired on August 28, 2025, Mandiant investigated the breach and, as of September 6, 2025, has confirmed that the incident is contained.
The investigation's most important finding is that the breach was centered on the Drift application environment. The separate Salesloft platform was not compromised for data exfiltration, and Mandiant verified the technical segmentation between the two systems.
Details of the Incident
Mandiant’s investigation found that the attacker was active primarily between March and June 2025.
The attack unfolded in a clear, multi-stage process.
Stage 1: Initial access via GitHub
The attacker first gained access to Salesloft's GitHub account. From there, they downloaded content from multiple code repositories, added a guest user, and established workflows to maintain their access.
Stage 2: Reconnaissance
The attacker then performed reconnaissance in both the Salesloft and Drift application environments. However, the investigation found no evidence of a deeper compromise within the core Salesloft application itself.
Stage 3: Pivot to Drift environment & credential theft
The attacker leveraged their position to access Drift’s AWS environment. Once inside, they stole OAuth tokens for Drift customers’ technology integrations.
Stage 4: Data exfiltration
Using the stolen OAuth tokens, the attacker accessed customer data through the active Drift integrations.
The attack was methodical, with Cloudflare's investigation showing attacker activity that included initial reconnaissance on August 9, expanded reconnaissance on August 13, and final data exfiltration on August 17.
Official response and containment activities
Salesloft, with validation from Mandiant, executed a swift and thorough response to contain the threat.
Drift application environment
- The Drift infrastructure, application, and code have been isolated and contained.
- The Drift Application has been taken offline.
- All impacted credentials in the Drift environment have been rotated.
Salesloft application environment
- Credentials in the Salesloft environment were proactively rotated.
- Extensive threat hunting was performed across Salesloft infrastructure, and no additional Indicators of Compromise (IOCs) were found.
- The Salesloft environment was rapidly hardened against the attacker's methods.
Resolution and service restoration
Following the initial containment, Salesloft has now restored the integration with Salesforce. The restoration process requires customers to engage with the Salesloft Customer Success team to perform data reconciliation. Once this is complete, the Salesforce sync can be safely re-enabled.
The integration between the Salesloft platform and Salesforce has been restored.
List of businesses impacted by the Salesloft Drift breach
Victims include major technology companies and several prominent cybersecurity vendors.
How to respond to the Salesloft Drift event
Given the nature of the breach, organizations using Salesloft Drift (especially those integrating it with third-party platforms like Salesforce) are urged to take immediate action to mitigate risk and investigate for potential compromise.
The primary recommendations from security researchers fall into three main categories: investigation, remediation, and hardening.
1. Investigate for Compromise and Scan for Exposure
- Review integrations: The first step is to review all third-party integrations connected to your organization's Drift instance. This can be done within the Drift Admin settings page.
- Search logs for malicious activity: Within each integrated third-party application, search for the Indicators of Compromise (IoCs), such as IP addresses and User-Agent strings, provided by Google's Threat Intelligence Group. In Salesforce, this involves reviewing authentication activity from the Drift Connected App and looking for unusual RestApi Query events.
- Scan for exposed secrets: Actively search your Salesforce objects and other integrated platforms for sensitive secrets that may have been exposed in the exfiltrated data. The threat actor specifically looked for credentials related to Amazon Web Services (AWS), Snowflake, and other services.
Salesloft Drift IOCs
2. Revoke and rotate credentials
- Rotate all connected tokens and keys: For every third-party application integrated with Drift, immediately revoke and rotate all API keys, credentials, and authentication tokens associated with the integration.
- Rotate exposed credentials: If the investigation uncovers any hardcoded secrets or exposed credentials, they must be rotated immediately. This is critical to prevent the threat actor from using them to compromise other systems.
3. Harden access controls for the future
- Enforce the Principle of Least Privilege: Ensure that connected applications like Drift have the minimum necessary permissions required to function. Avoid granting overly permissive scopes, such as "full" or "api," to third-party integrations.
- Restrict access by IP address: Where possible, define trusted IP ranges for connected applications to restrict access to your corporate network. Okta successfully blocked this attack because the threat actor's connection attempt came from an unauthorized IP address.
- Limit API access: In Salesforce, remove the "API Enabled" permission from general user profiles and grant it only to authorized users via a Permission Set.
4. Re-enable and Reconcile Integrations
For the Salesforce integration, do not re-enable the sync immediately. Wait for the Salesloft Customer Success team to contact you to guide you through the necessary data reconciliation steps.
How to check if you've been impacted by the Salesloft Drift event
To check if you have been impacted, your security team should:
- Treat drift-related tokens as compromised: Given the scope of the incident, the safest approach is to treat any authentication tokens stored in or connected to the Drift platform as potentially compromised.
- Audit third-party application logs: The most direct way to check for impact is to search the audit logs of any application integrated with Drift for malicious activity. You should search for suspicious queries or access patterns originating from the IP addresses and User-Agent strings in the IOC table above.
- Review Salesforce authentication and API logs: Specifically, within Salesforce, administrators should review authentication activity associated with the Drift Connected App and look for unusual RestApi Query events that query 500 or more records.
Why is this an important issue for vendor risk management?
This incident is a key lesson in third-party risk. The attacker's entry point was a code repository, which they then used to pivot to a related but separate application (Drift). This highlights the need to scrutinize the security of all platforms a vendor operates, not just their main product.
The Salesloft Drift incident highlights several crucial issues for Vendor Risk Management:
- Risk Concentration: The attack exposed the systemic risk created when many organizations rely on a central platform like Salesforce. When a single, widely used application integrated with that platform (in this case, Drift) is compromised, it creates a single point of failure with a massive blast radius, affecting numerous companies simultaneously — like we saw in the CrowdStrike incident.
- Inherent trust is a bad habit: The attack's effectiveness relied on the inherent trust that organizations place in their third-party integrations. By hijacking legitimate OAuth tokens, the attackers could impersonate the Drift application, allowing their malicious data exfiltration queries to blend in with regular API traffic and bypass traditional security tools.
- Identity risk is the new perimeter: The breach underscores that identity compromise is among the most pressing risks in SaaS environments. The attackers did not need to exploit a technical vulnerability in Salesforce; they simply needed to acquire valid credentials — OAuth tokens issued through a normal authorization flow. This demonstrates that an organization's security is no longer defined by its network perimeter but by the security of all identities and applications with access to its data.
- Everyone is at risk: The list of confirmed victims includes major technology providers and even prominent cybersecurity vendors like Cloudflare, Palo Alto Networks, and Zscaler. This proves that even organizations with mature security programs are susceptible to supply chain attacks, making rigorous third-party cyber risk management a critical pillar for all cybersecurity programs.
How to ensure you are protected against similar future attacks
Protecting your organization from similar supply chain attacks requires a proactive, defense-in-depth approach focused on managing third-party application risk.
- Enforce the Principle of Least Privilege: A critical first step is to ensure that all third-party integrations, including Drift, are granted only the minimum necessary permissions to perform their intended function. Avoid assigning overly permissive scopes like "api" or "full access" to connected applications. If an attacker had compromised a token with fewer privileges, the potential for significant data loss would have been greatly reduced.
- Implement strict access controls: Configure connected applications to only allow access from trusted IP ranges. This single control prevented the attackers from accessing Okta's Salesforce instance. You should also limit API access to only authorized users through the use of dedicated Permission Sets rather than enabling it by default on broad user profiles.
- Assume breach and rotate credentials: As a matter of policy, immediately revoke and rotate all credentials, API keys, and authentication tokens for any application connected to a compromised third-party service. Any sensitive data or credentials that a customer may have shared with a vendor (e.g., in a support ticket) should be considered compromised and rotated immediately.
- Integrate AI into your third-party risk program: Traditional vendor monitoring struggles to keep pace with the rapidly expanding digital supply chain. Integrating AI into your TPRM workflow bridges this critical visibility gap, making it possible to track changes to each critical vendor's security profile in real time.
How UpGuard is helping customers respond to the Salesloft Drift breach
UpGuard has shipped a number of updates to help its customers rapidily respond to the Salesloft Drift supply chain attack:
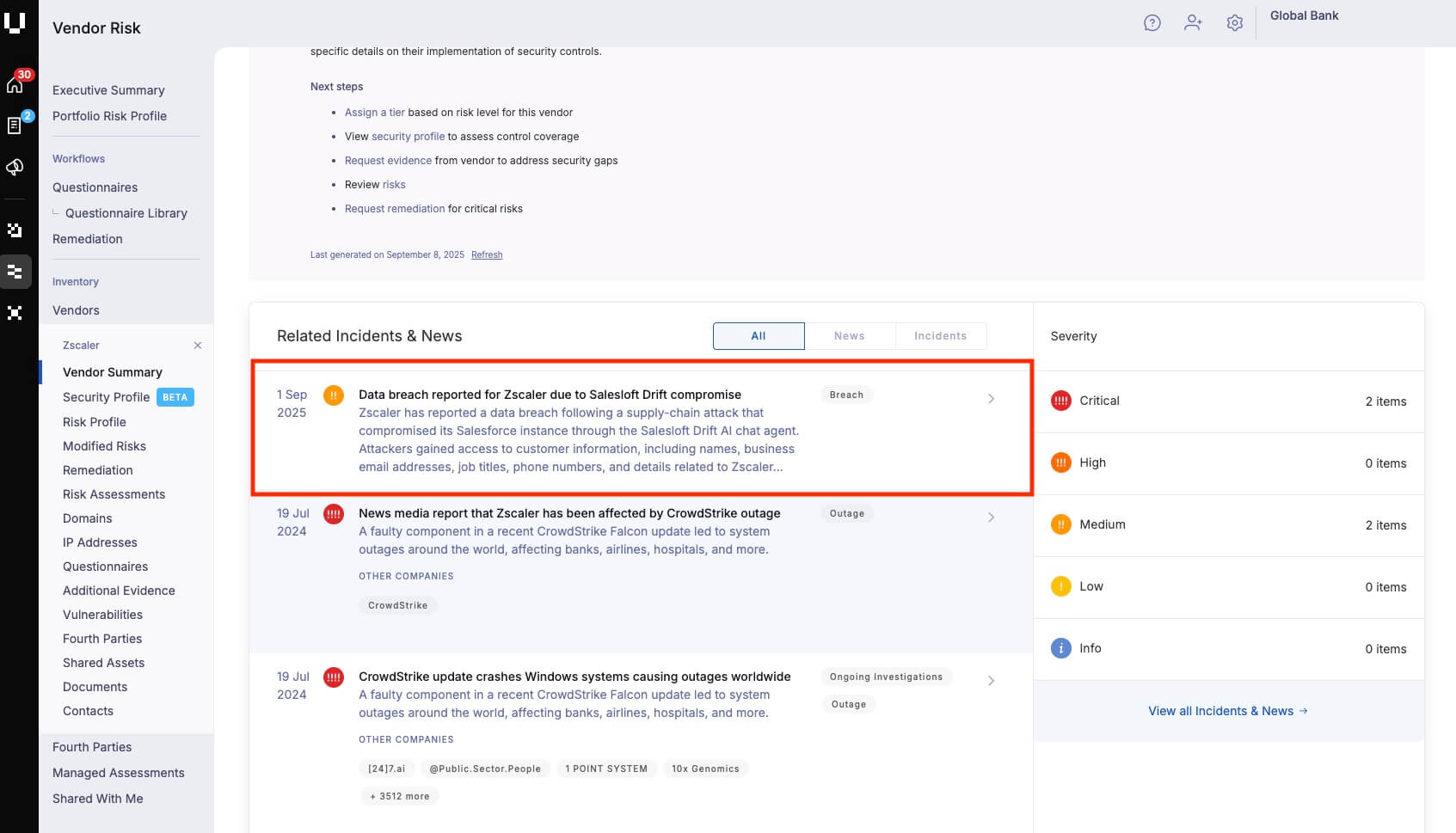
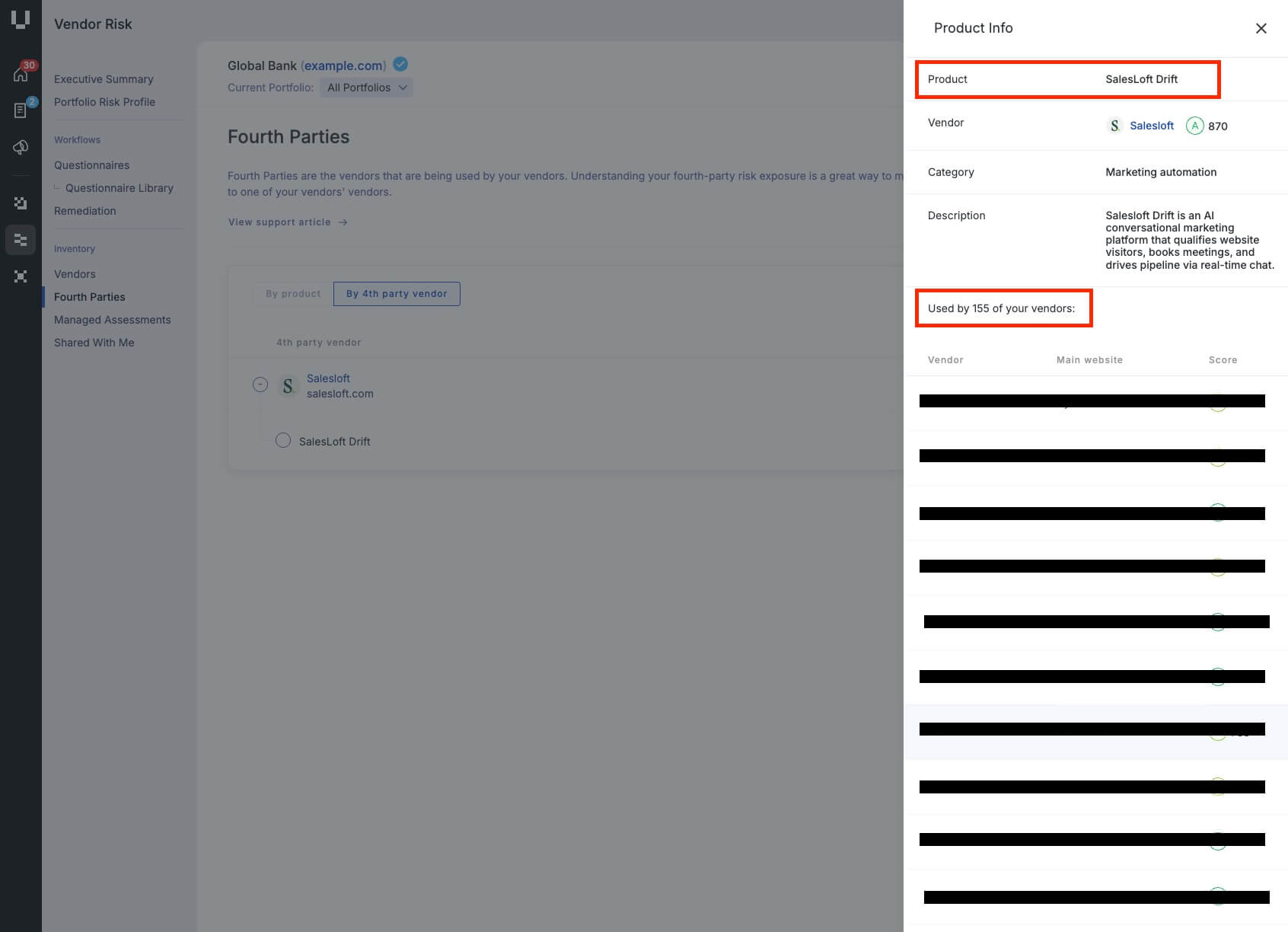
Immediate Salesloft Drift visibility
Customers can now instantly see their exposure to Salesloft Drift wherever it appears in their IT ecosystem, as a detected product in their domain network via Breach Risk, and as a fouth-party vendor via Vendor Risk.
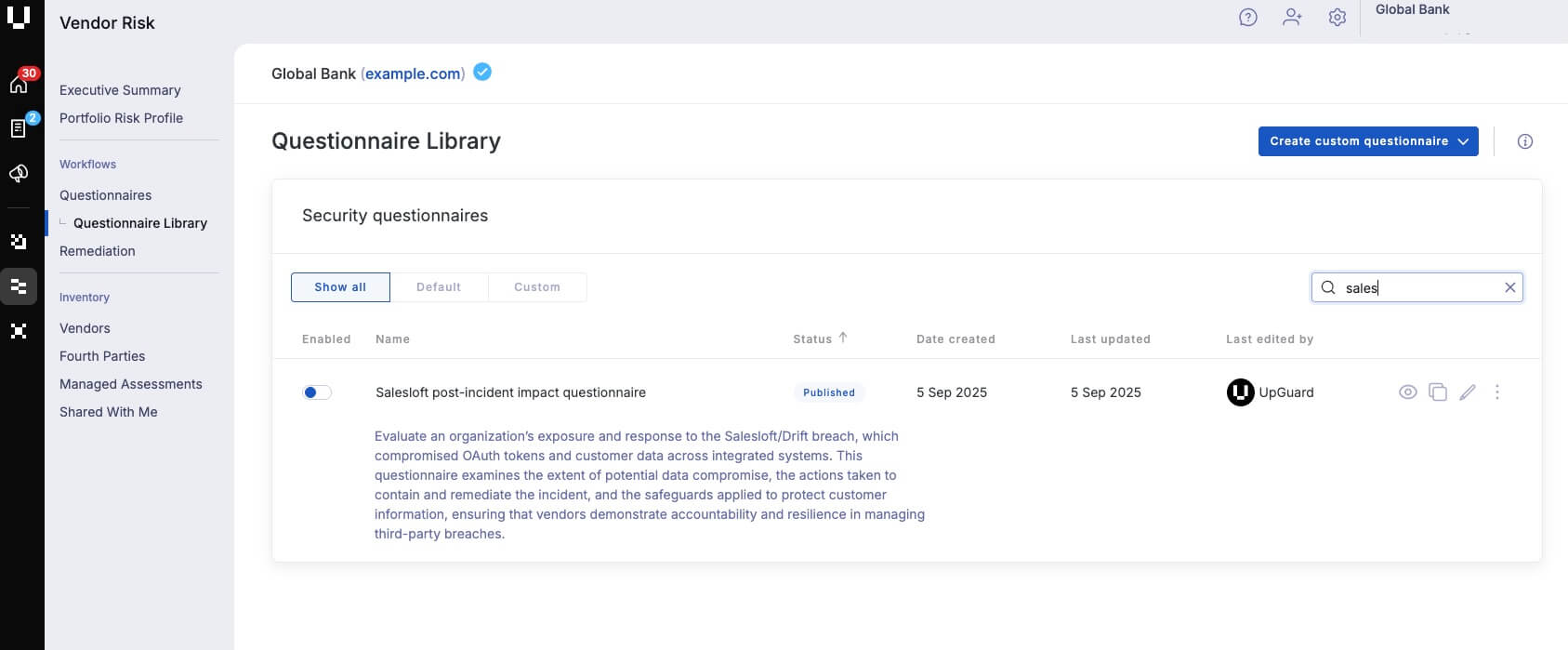
Salesloft post-incident impact questionnaire
This questionnaire helps teams quickly assess potential exposure to this incident, ensuring right information is collected for a more in-depth impact analysis.
How does UpGuard help security teams prepare for future incidents like this?
UpGuard provides specific capabilities to help security teams reduce the impact of future similar supply chain attacks:
- Fourth-party identification: UpGuard detects relationships with your vendors' vendors (fourth parties), providing critical visibility into the entire digital supply chain to prevent security gaps from downstream providers.
- Customizable questionnaires: The platform uses pre-built and customizable security questionnaires to conduct due diligence, ensuring that vendors meet your organization's specific security and reliability standards.
- Vendor risk classification: UpGuard includes tools to classify vendors based on their level of access and potential risk, allowing security teams to focus their resources on the most critical third-party relationships.
- Key document centralization for incident response: The platform offers a contract repository to store essential documentation, ensuring that response plans, service level agreements (SLAs), and liability information are easily accessible during an incident.