Grounded: The ARINC vMUSE Attack Disrupting Multiple Airports
The line between the digital and physical worlds blurs completely when a cyber attack results in widespread, tangible disruption. For thousands of travelers, this became a harsh reality when major European airports were forced to delay flights due to a ransomware attack targeting a vendor in the supply chain.
To prevent a repeat catastrophic event, we must break down how the vendor's vulnerability was exploited and deepen our understanding of the often-overlooked risks lurking within complex technology supply chains.
What we know
On Saturday, September 20, 2025, a cyber attack caused significant disruptions at several major European airports. The European Union Agency for Cybersecurity (ENISA) later confirmed that a ransomware attack caused the outage, which targeted the ARINC vMUSE system, a passenger processing platform by Rockwell-Collins.
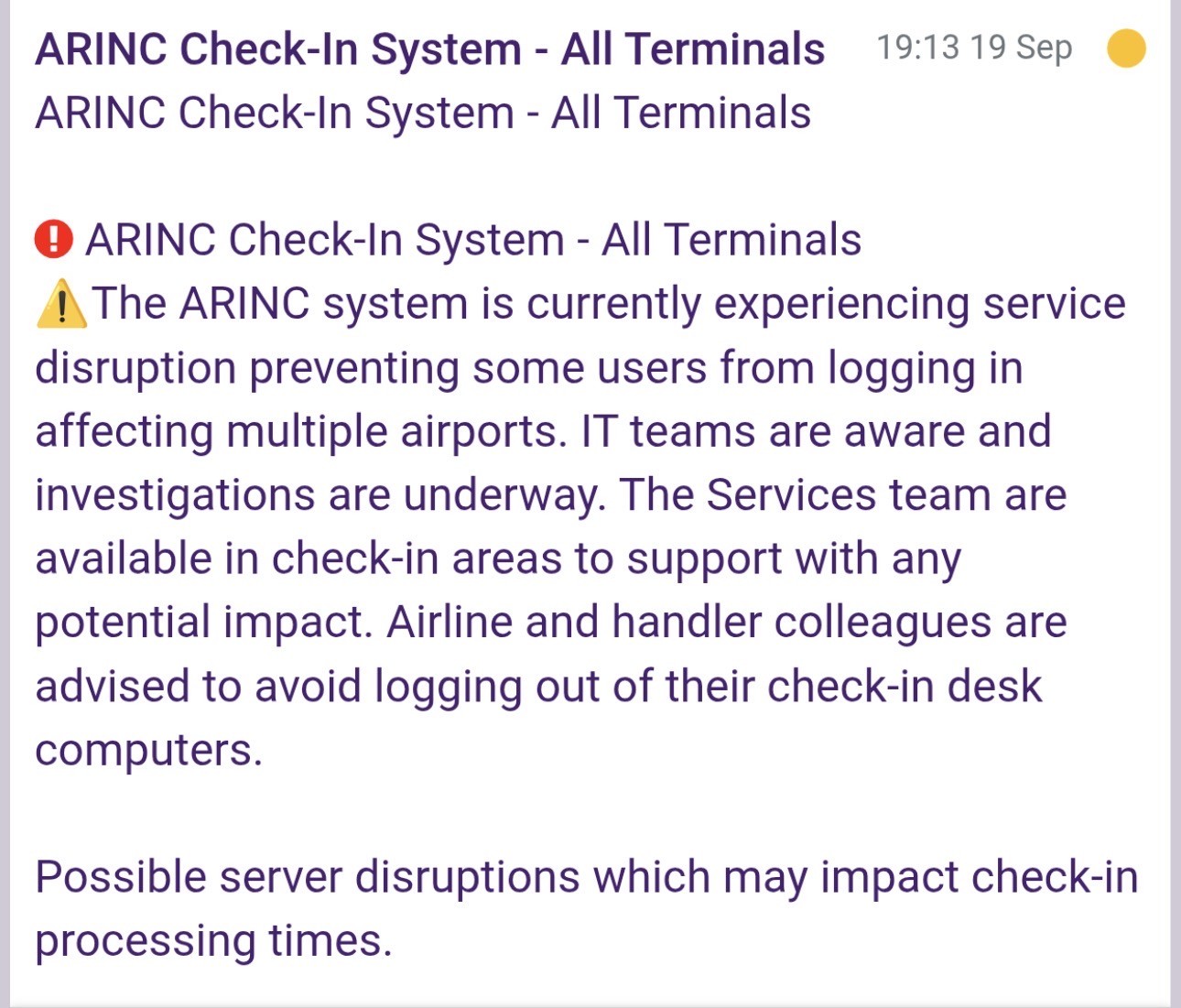
With this system unavailable, airports were forced to switch to manual procedures. This workaround caused major delays for passengers and led to 217 flight cancellations across the key affected hubs as staff worked to get operations moving again and restore the system's functionality.
A chain of vulnerabilities
While the full details of the intrusion are still under investigation, the technical cause of the breach points to a classic and preventable security failure: the exploitation of outdated, vulnerable, and internet-facing systems. The vMUSE platform connects airports via a proprietary Collins network called ARINC AviNet, which functions as a dedicated VPN. The simultaneous failure across multiple airports strongly suggests that this central network was the point of compromise.
Here is a list of the top ten airports using vMUSE:
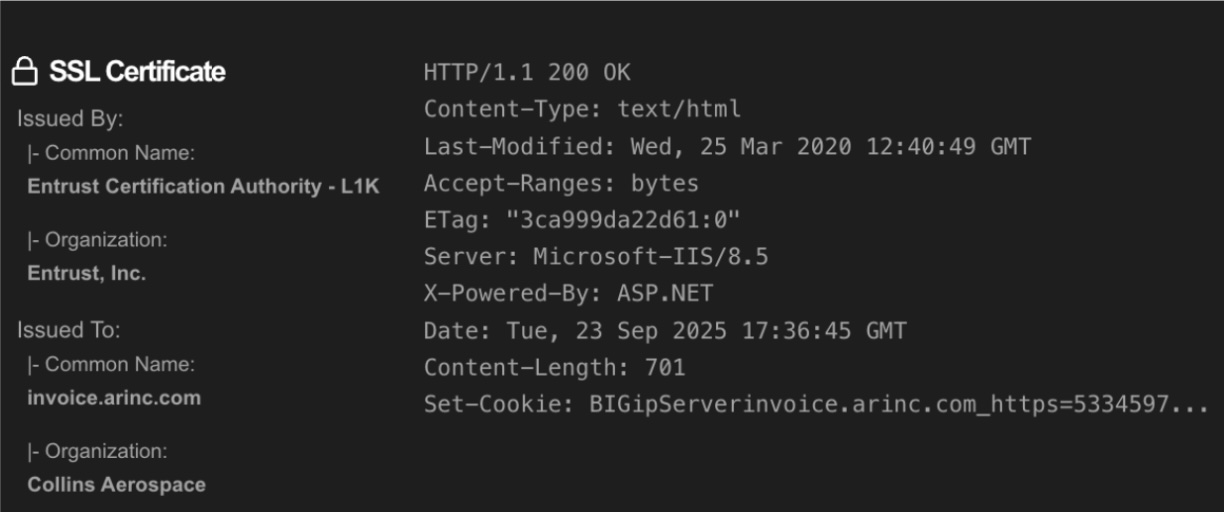
Security researchers examining the public-facing infrastructure of the ARINC network quickly identified multiple red flags, painting a picture of a digital environment ripe for compromise. Public scans revealed that the company's network was running a host of obsolete software, including:
- Microsoft's IIS 8.5 web server, which reached its official end-of-life in 2023.
- A version of the Glassfish application server dating back to 2014.
- An Oracle Communications Messaging Server that had not been updated since 2015.
These legacy systems contain well-documented vulnerabilities that have long since been addressed in newer versions.
A significant cybersecurity oversight appears to be the use of outdated network hardware. Half of the company's Cisco ASA VPN appliances — devices that act as the gatekeepers for the network — were operating past their manufacturer's end-of-life date, meaning they no longer received security updates.
A wide range of known vulnerabilities exists for these devices and their software. Coupled with the fact that they must be internet-facing to function, the use of Cisco ASAs creates a high-risk environment ripe for exploitation.
Cyberattacks with such large-scale impacts usually require extensive preparation, and this event may have been set in motion as early as 2023. Though not confirmed by Collins Aerospace, the ransomware group BianLian claimed to have breached Collins Aerospace in 2023, stealing around 20 gigabytes of data.
If true, this event could have armed the attackers with the data leaks they needed to successfully execute this larger-scale attack.
The core lesson: A failure of supply-chain security
Ultimately, the chaos that unfolded across Europe's airports was not just the result of a single company's security lapse but a catastrophic failure of supply-chain security. The incident is a textbook example of the ripple effects of an interconnected digital ecosystem, where a vulnerability in one vendor can trigger a cascade of disruptions for countless dependent organizations.
The reliance of multiple international airports and airlines on a single, compromised system creates a single point of failure that attackers could exploit with devastating effect.
Adding a critical layer to this failure, the European Union Agency for Cybersecurity (ENISA) revealed that the attackers' initial entry point was not Collins Aerospace, but one of its own third-party providers.
This oversight highlights a fundamental weakness in modern enterprise security: most organizations are blind to the security risks of their vendor network.
This detail transforms the event from a direct vendor compromise into a multi-layered supply-chain attack, highlighting how deep and opaque these digital dependencies can be. It underscores a fundamental weakness in modern enterprise security: organizations are often blind to the risks inherited from their vendors' vendors.
To prevent future incidents of this scale, organizations must adopt a more rigorous and proactive approach to cyber risk posture management.
Key recommendations include:
- Demand complete transparency from vendors: The most critical lesson from this event is that organizations must have deep visibility into their vendors' technology stacks and internal security policies. It is no longer sufficient to accept a vendor's assurances of security. Businesses must demand answers to specific, granular questions, like:
- What software and hardware are you using?
- What are your patching schedules and update policies?
- How do you manage end-of-life equipment? T
Proper supply chain security assumes a vendor's systems are likely attack vectors, and that begins with complete awareness of their digital footprint.
- Implement robust legacy system management: Critical systems that rely on older components or cannot be easily updated present a significant risk. These systems must be properly inventoried, continuously monitored, and protected with strong compensating controls to reduce their attack surface and isolate them from potential threats.
- Elevate cybersecurity to a core business Function: The level of investment and executive oversight in cybersecurity must directly correspond to the criticality of the systems being protected. Security cannot be treated as a simple back-office IT function; it is a fundamental business risk. Rectifying this organizational mindset is the first and most important step in building true resilience.
The aviation industry, and indeed all sectors relying on complex technology partners, must now move swiftly to implement these principles to build a more defensible Third-Party Risk Management foundation.