Breach Risk Threat Monitoring: A Path to Clarity in Cyber Noise
The digital landscape is expanding at an unprecedented rate, driven by the mass migration to the cloud, the proliferation of IoT devices, and the rapid growth of AI. While this growth presents limitless opportunities, it also creates a daunting new reality for cybersecurity teams.
As a company's digital footprint and attack surface expand, it becomes increasingly vulnerable to the growing number of threats, particularly those originating from the open, deep, and dark web. Threat actors in these spaces are becoming increasingly active, establishing larger operations and developing comprehensive criminal supply chains.
The problem is that even when security teams use dedicated tools to monitor the dark web, they're often overwhelmed by a flood of raw data and alerts. This requires significant manual effort to investigate and remediate, forcing teams into a reactive security strategy rather than taking proactive steps to protect their posture.
So, how can a cybersecurity team, already inundated with daily alerts, proactively address the ever-growing number of threats from illicit online spaces? The answer lies in one crucial aspect of threat detection: context.
Why Context Matters Now, More than Ever
As the average business's attack surface continues to grow, modern security operations center (SOC) teams are increasingly focused on detecting threats from the open, deep, and dark web. These areas are a well-known blind spot for conventional internal security tools, such as firewalls and endpoint detection and response (EDR) systems, which only monitor their immediate perimeter.
Think of it this way: securing your home with bodyguards who check the doors and windows is a solid defense. But who's checking the local pub down the street where someone might be discussing their plans to break in next week? In the modern security landscape, that "pub" is where breaches often begin—with attackers selling stolen credentials, planning attacks on illicit forums, or exposing sensitive data in public code repositories.
To supplement these blind spots, threat analysts utilize individual tools to scan the internet for underground forums, marketplaces, and criminal groups, thereby understanding their tactics, techniques, and procedures (TTPs). While these scans are useful, they lack a crucial component: context.
These external sources generate a large amount of noise in the form of alerts. Without a specialized solution that provides real-time clarity, the process becomes slow and inefficient. Each potential threat must be triaged and investigated individually, turning vital intelligence into an unmanageable sea of noise.
This lack of context is the driving factor behind two critical issues faced by SOC teams when monitoring the open, deep, and dark web: a reactive security strategy and alert fatigue.
A reactive security strategy
A reactive security strategy means a security team is constantly playing catch-up, responding to threats only after they've been identified. This is a direct result of a lack of context. Without a clear understanding of an alert's severity, analysts are forced to react to every signal, wasting time on low-priority issues while real threats go unnoticed.
Instead of proactively hunting for risks and strengthening defenses, the team gets stuck in a cycle of triage and investigation, never gaining an advantage.
A truly proactive security strategy uses context to prioritize threats, spot new trends, and predict potential attacks before they happen. For example, if a company's credentials are sold on the dark web, a proactive team would use context to understand the scope of the breach and take steps to prevent future attacks.
Without this contextualized approach, teams are left fighting one fire at a time, creating an insecure and unsustainable operational model.
Alert fatigue
Alert fatigue is a longstanding issue within the cybersecurity industry, and it is especially prevalent when teams are required to manually triage, investigate, and remediate every alert from their daily scans without context. This time-consuming burden is a serious threat that can severely weaken a company's security posture and potentially lead to major security gaps.
This fatigue triggers a cascade of risks, including missed critical alerts, widespread team burnout, and a high volume of false positives. Let's take a look at some examples of the consequences that arise when alert fatigue is prevalent within your cybersecurity team.
- Increased risk of data breaches: Security analysts face an overwhelming number of alerts, which makes it easy to miss real threats. For instance, the M-Trends 2025 report revealed that cybercriminals are using Infostealer malware to steal sensitive data and sell it on online forums. These genuine threats can be easily lost in the constant stream of notifications that analysts must deal with, and thus, the chances of a successful breach increase.
- Delayed response to critical threats: Investigating false positives, such as your company name simply being mentioned on a dark web forum, is a significant drain on a security team's time and resources. When analysts are overwhelmed with irrelevant alerts, their attention is diverted from real threats, thereby delaying the detection and prevention of an attack.
- High employee turnover and burnout: The stress of sifting through thousands of alerts daily can lead to emotional and physical exhaustion, and this stress factor is amplified when alerts are coming from varying sources. A study commissioned by Kaspersky found that 83% of cybersecurity practitioners experience alert fatigue, which can lead to high turnover rates.
- Wasted resources: The time security professionals spend investigating irrelevant alerts is time not spent on more strategic initiatives, such as proactive threat hunting or enhancing security architecture. This leads to an inefficient use of valuable human resources and can result in higher operational costs.
It's clear then that the issue of context matters more now than ever before. It's the root cause behind critical security gaps when monitoring the deep, open, and dark web, significantly increasing alert fatigue and inaccurate responses. The bleak reality is that when your team is stuck in this cycle, regardless of how lean your SOC team is, your business's overall security posture is at risk.
Thankfully, however, this daunting challenge can be mitigated. This is our answer to the increasing number of contextless alerts from the open, deep, and dark web, as well as the critical concerns of reactive security strategies and alert fatigue: Breach Risk Threat Monitoring.
Introducing Threat Monitoring: Cutting Through the Noise To Enable Proactive Risk Management
UpGuard has officially expanded our Breach Risk solution to include a new feature called Threat Monitoring. Our vision for this product was straightforward: to provide cybersecurity teams with a way to cut through the noise when monitoring the wider internet and turn signals into actionable intelligence.
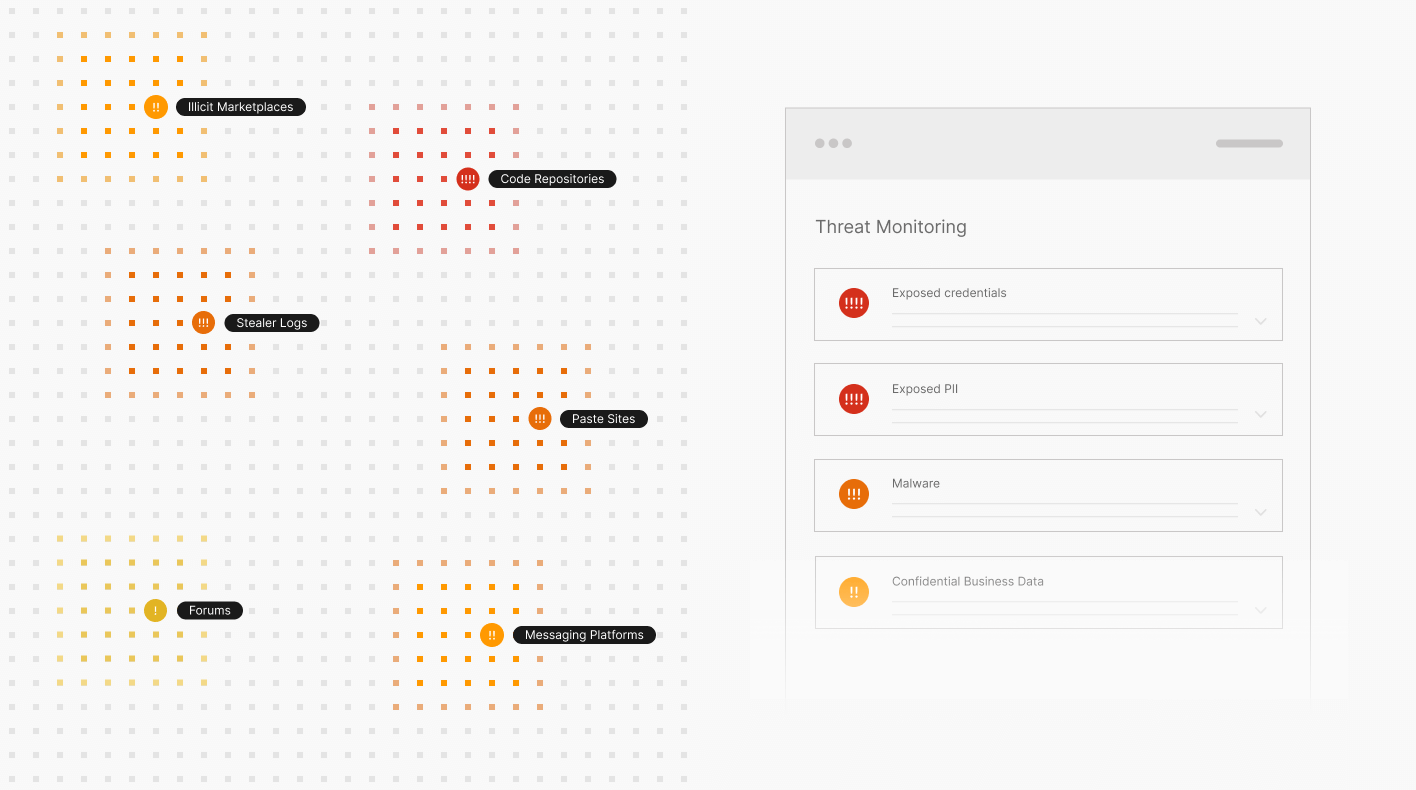
Think of Threat Monitoring as your virtual threat analyst inside of Breach Risk. It interprets and provides context for threats across your external attack surface, then prioritizes them by severity and provides remediation workflows and guidance. This enables your team to transition from a reactive workflow to a lean, proactive strategy—addressing critical threats before they become breaches and avoiding wasted resources on low-impact alerts.
To ensure this new feature truly delivers on its promise, we released it to customers for early access. Using their feedback, we've fine-tuned Threat Monitoring to deliver on our vision of proactive threat detection and management on the open, deep, and dark web. Let's break down how it all works in detail.
Transform raw signals into actionable threats
Threat Monitoring is designed to empower your cybersecurity teams to move from noise to clarity. It achieves this through an adaptable and intelligent search object called Transforms, which can be thought of as a superpowered "keyword search."
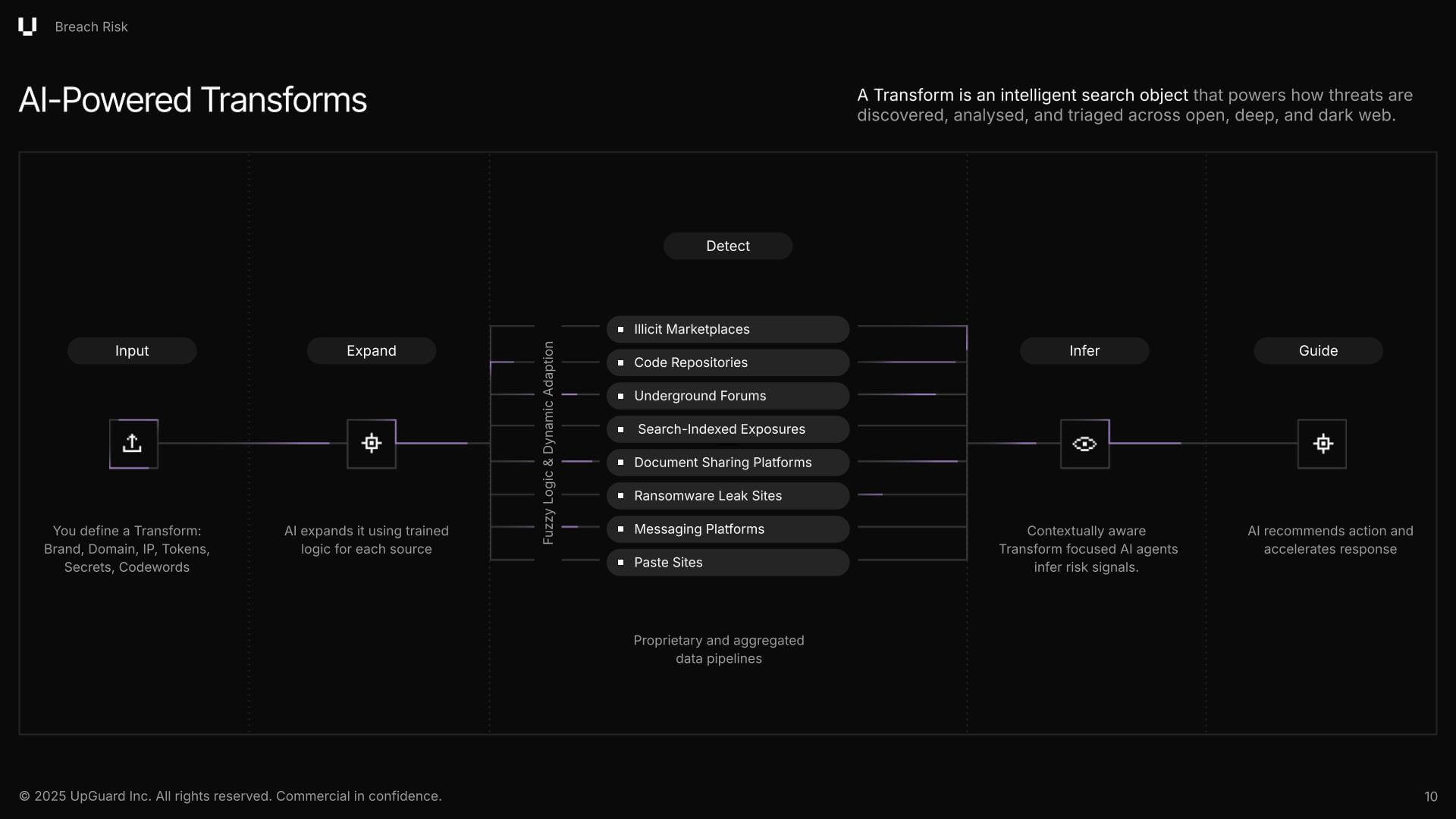
Threat Monitoring’s source-aware Transforms automatically fan out to detect exposures across the open, deep, and dark web platforms. It extends its reach to platforms such as GitHub, Telegram, ransomware blogs, forums, and illicit marketplaces, posing a significant challenge for many security teams to monitor.
These are not network logs or system alerts; they are chaotic, decentralized platforms where threat actors communicate, trade stolen data, and plan attacks. Without specialized tools, a security team is essentially blind to the external threats being planned against them, but Breach Risk’s Threat Monitoring scanning finds and surfaces each match.
This last step is where Transforms truly shine, as they can then interpret the context of each finding and link it to potential business risks. So, if a flag is raised for your company's name being mentioned in a dark web forum somewhere, the Transform will interpret that context and feed it into the next core system of Threat Monitoring, which utilizes AI-powered prioritization.
Prioritize what matters with AI-powered intelligence
Now that you've gotten the context surrounding your alerts thanks to Transforms, what's next?.
Well, to truly gain control, you need a way to prioritize threats effectively without having to manually review them all. And that's where Threat Monitoring's AI-powered prioritization feature takes the reins.

Trained by cybersecurity analysts, it analyzes each finding and its context, provided by the Transform, to infer and easily communicate its severity, urgency, and context. This analysis provides a threat severity indicator as well as a high-level threat summary, making it far easier to understand at a glance. This is extremely powerful for cybersecurity teams managing larger attack surfaces, as they would typically need to vet each case individually, especially if they originate from sources such as the dark web.
The AI threat summary is great. It’s refreshing to read two sentences and immediately know why I should care about a finding. I can look at a critical alert, see that it’s exposed GitHub credentials from a classroom lab exercise, and move on within seconds because the context is right there.
— Tom Grundig, Director of Information and Security, Boston University
Instead of manually triaging threats, a cybersecurity specialist can simply read a high-level threat summary to instantly determine if a threat is urgent and requires immediate remediation. This allows for rapid threat detection that leverages AI to not only make a cybersecurity team's job a lot easier but also enables them to proactively tackle threats and vulnerabilities well in advance.
Finally, Threat Monitoring provides clear, actionable remediation guidance for each finding. Once an alert has been contextualized and prioritized, it offers a clear path forward—such as initiating credential resets or notifying relevant stakeholders—allowing teams to easily plan their workflow, coordinate with other departments, and move from insight to remediation in a few simple steps.
Make the shift to proactive security
By transforming noise into clear signals, prioritizing what truly matters, and providing integrated remediation guidance, Threat Monitoring empowers your team to move beyond simply responding to incidents. It allows them to focus on meaningful work, strengthen their overall cyber risk posture, and build a resilient and proactive security strategy to prevent threats before they become breaches.
“Security teams today are overwhelmed by fragmented alerts and lack the visibility needed to see how attackers view their organization,” said Dan Bradbury, Chief Product Officer, UpGuard. “With Threat Monitoring in Breach Risk, our customers gain a clear, prioritized view of emerging threats, supported by AI that cuts through noise to surface real risks so teams can act faster.”
This shift from a reactive to a proactive security posture is precisely what's needed in today's rapidly evolving threat landscape within the open, deep, and dark web. The expanding attack surface, the overwhelming volume of alerts, and the constant battle of missing context no longer need to be insurmountable challenges.
For example, instead of simply being alerted to a breach after it has occurred, Threat Monitoring can proactively surface a conversation on a dark web forum where a threat actor is attempting to sell credentials for your network. This allows your team to disrupt the attack, invalidate the credentials, and strengthen your defenses before the threat even has a chance to execute.
By finding and addressing these external threats at their source, you move from a posture of passive defense to one of active disruption.
A Crucial Part of a Complete Cyber Risk Solution
Threat Monitoring is a powerful new capability now available within Breach Risk, but it's just one piece of the puzzle. It stands as a key feature within UpGuard’s comprehensive Cyber Risk Posture Management (CRPM) platform, designed to provide a complete and unified overview of your security landscape.
Expanding Threat Monitoring within Breach Risk aligns with our vision for Cyber Risk Posture Management. We’re helping customers move from reactive alert fatigue to proactive threat detection and response while simplifying how they manage and report on cyber risk.
– Mike Baukes, CEO, UpGuard.
When coupled with our other powerful tools, such as Vendor Risk and User Risk, security teams gain the ability to proactively secure their digital assets. Breach Risk and Threat Monitoring handle threats to your immediate external attack surface, while Vendor and User Risk address external vulnerabilities across your supply chain and threats within your workforce, respectively. This powerful combination allows you to manage security both internally and externally from a single platform, embodying our approach to holistic cyber risk posture management.
Ready to see the whole picture? Request a demo or product tour today to discover how Threat Monitoring integrates with our complete platform and empowers your team to move beyond simply responding to incidents to actively preventing them.