From September 14-16, over 180 NPM packages were compromised and used to deliver what is now called the Shai-Hulud worm. That malware would propagate itself by pushing malicious changes to other NPM packages accessible to the victim, and exfiltrate the victim’s secrets by publishing them to public GitHub repositories. The names of the compromised packages have been reported by the original researchers, and others have noted that early in the attack cycle, there were over 700 GitHub repos with the “Shai-Hulud Migration” or “Shai-Hulud Repository” descriptions indicative of compromise. This report uses publicly verifiable data to investigate which companies had users affected by Shai-Hulud to better understand the scope of this incident.
The GitHub events archive
Reports on the extent of Shai-Hulud exfiltration to GitHub, like that from Wiz, have focused on using GitHub Search to find repositories with indicators of compromise, most obviously the repo descriptions “Shai-Hulud Migration” or “Shai-Hulud Repository.” This method is limited in that it only searches live content; deleted repos are not indexed by search. By the end of September 16, only a handful of affected repositories were still up on GitHub.
However, there is an independent forensic trail of activity on GitHub that UpGuard and other researchers can use to search some data and metadata from repos, even after they have been deleted. Actions on GitHub, like creating a repo or changing a private repo to public, create events in the GitHub public timeline. Those events can be read in real time for data leaks and threat monitoring, and historical events can be downloaded from gharchive.org. Thank you, GH Archive!
Identifying users infected with Shai-Hulud
The technical details of this attack allowed us to reliably identify affected repos’ GitHub event data. The repos created or modified by the worm all have one of two possible descriptions, with no randomness or other complications, and this description does not frequently occur outside of this attack.
Filtering the GitHub events archive to just events mentioning our Shai-Hulud keywords, we wind up with 207 repos. Of those, 175 match the “Shai-Hulud Migration” description and 33 match “Shai-Hulud Repository.”
The two descriptions mapped to the two GitHub attack patterns. Repos with the description “Shai-Hulud Migration” were generally pre-existing repos that the malware renamed to “<previous repo name>-migration” and made public. Those with the description “Shai-Hulud Repository” were new repos created by the malware with the name “shai-hulud” containing only the data.json used to exfiltrate secrets. In reviewing the names of repos with each description, these mappings were overwhelmingly true, though there were some exceptions. Some of those repos, where a new repo is named “shai-hulud” but the description is “Shai-Hulu Migration” and no data.json file is present, might be lookalikes created by users or remnants of incomplete clean-up.
From the list of affected repos, we can identify the users who own them. Among that data set, a small number of users were responsible for the largest number of repos. Some of these users were also contributors to NPM packages and thus acted as the “super spreaders” that propagated Shai-Hulud to other packages, from which it could infect new users.
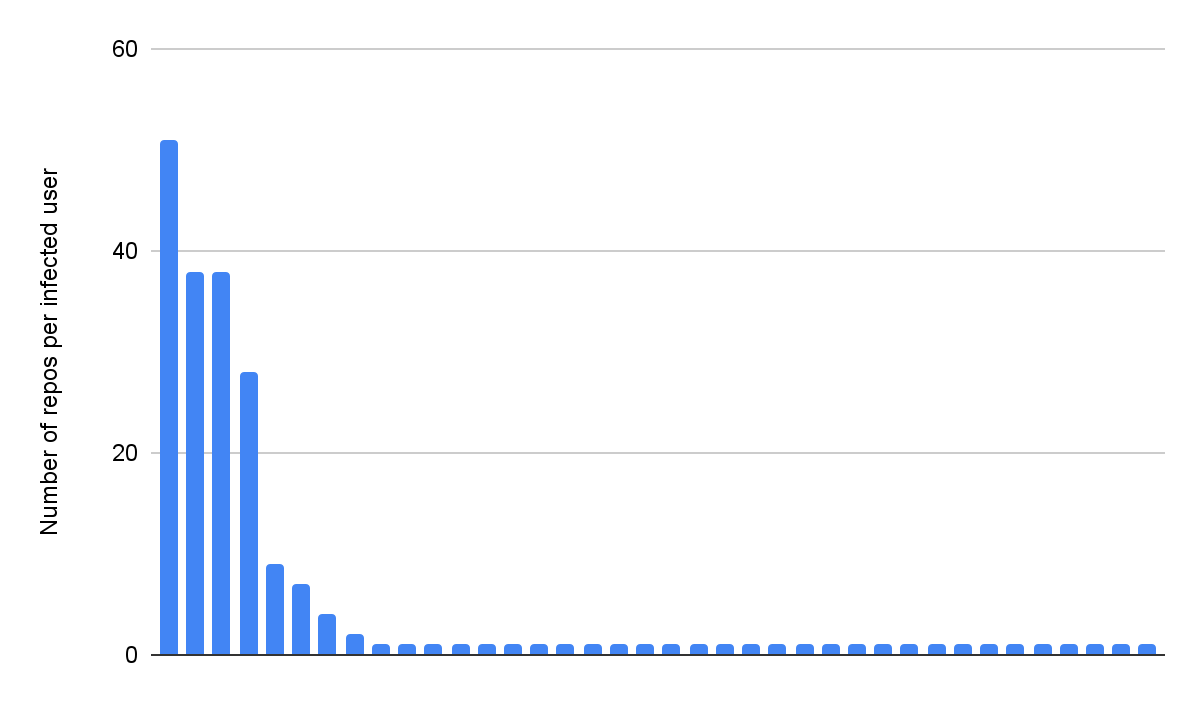
Identifying companies infected with Shai-Hulud
Those 207 repos only belonged to 37 unique users. GitHub offers many optional ways that a user might identify their employer, but with such a small number we could be safe and manually confirm those attributions ourselves.
That level of inspection identified a tiny number of false positives, but overwhelmingly provided confirmation of the user’s self-identified employers. (The false positives were non-trivial to identify and would be difficult for any automated system. For example, one user went so far as to create an exact replica of the IOC: a repo named shai-hulud, description reading “Shai-Hulud Repository,” contents of a single data.json file, double base64-encoded data, only to reveal a YouTube link to…a Rickroll.)
The repo names also gave some hint of the potential impact on those companies. As seen above, most users had a single point of impact. Others, those with many private repositories that were flipped to public, had access to data that suggests extensive corporate impacts. The user who unintentionally leaked 50 repos bearing their employer’s name has deleted their entire GitHub account.
Amongst users with IOCs in the public GitHub archive and GitHub profiles with identifiable employers, these are the companies where they work:
- aplos.com
- asnbank.nl
- bitfactory.nl
- brightback.com
- crowdstrike.com
- fino.group
- flockit.com.ar
- klarrio.com
- kodelabs.com
- logovo.ca
- loopmein.app
- mobioffice.io
- nstudio.io
- openloophealth.com
- verifaction.co.za
- wdtablesystems.com
- yoobic.com
Crowdstrike and nStudio are also among the maintainers of known compromised NPM packages, so their inclusion here is no surprise, but does help validate the methodology.
All of the associated GitHub users have since removed the files leaking their secrets or company code, but anyone can reconstruct the links to these companies using data from gharchive.org and inspection of the relevant users’ GitHub profiles.
Conclusion
The Shai-Hulud attack is certainly in the running for the largest supply chain compromise ever. The potential install surface for the affected packages is massive and requires action from all NPM developers to assess their exposure. Because of the particular method of data exfiltration in this case, we also have some visibility into the third-party impacts of the attack.
Similar to infostealer logs, malware infection can be inferred from the traces of attempted secret exfiltration. At a minimum, that fact warrants a response. In some cases, where private repos were leaked, more investigation is necessary to ensure that none of the data, secrets, or proprietary information in those repositories was accessed by unauthorized parties. As with stealer logs, the Shai-Hulud attack highlights the value of a diversity of tactics to detect compromises in the NPM ecosystem, audit internal systems for their usage, and monitor GitHub for indicators of compromise in the outside world.
Protect your organization
Related breaches

Student Applications: How an Education Software Company Exposed Millions of Files

By Design: How Default Permissions on Microsoft Power Apps Exposed Millions
Sign up for our newsletter
Free instant security score
How secure is your organization?




.jpg)
.jpg)

