6 Ways to Make Your Risk Assessments Land With Stakeholders
As businesses expand, so do their lists of third-party vendors—and with them, the number of risk factors and complexity. This increase means that security analysts are often overwhelmed by a growing number of vendor risk assessments. However, completing an assessment alone isn’t enough; its value depends on how effectively the results are communicated. Risk assessments are vital tools that stakeholders rely on to make informed decisions, and all that hard work risks being undermined if the findings aren’t presented in a way that resonates.
Analysts may struggle to get stakeholders to fully grasp the findings in their detailed and meticulous reports. These documents are often filled with technical jargon and complex topics that, even after attempts to simplify, remain a major pain point. Unless the results are translated into clear, actionable insights, stakeholders may miss the significance of the risks uncovered – and the value of the assessment is essentially lost.
In fact, nearly 50% of C-suite security professionals agree that jargon is the biggest barrier to management understanding and addressing cybersecurity risks within their vendor supply chain. The unfortunate reality is that a report (no matter how detailed) is useless if its critical findings are misunderstood.
This communication gap can lead to internal friction, delays, and misprioritization, but there are more severe consequences down the line. When strategic decisions (or lack thereof) are made without a true grasp of cyber threats, the outcome can range from a false sense of security to unexpected operational disruptions, significant financial losses, or irreversible reputational damage.
Fortunately, you have options to combat this disconnect. By adopting a few effective methods, you can improve your risk assessment reports and ensure they resonate with stakeholders at every level. This guide offers six practical techniques to help you create reports that everyone, from the server room to the boardroom, can easily understand.
1. Scope your report to the vendor engagement
A one-size-fits-all approach to vendor assessments can overwhelm stakeholders with irrelevant information. Focus on scoping the assessment's depth and breadth to align precisely with the unique characteristics of your relationship with a given vendor.
For example, if your core e-commerce platform relies on a third-party payment gateway, an assessment of that gateway's uptime, incident response, and data integrity is paramount. For a software vendor providing an internal, non-critical tool, the focus might be more on access controls and basic data privacy. Instead of assessing for every single control, focus only on what truly impacts your organization, given the vendor's role, system access, and data exposure.
This practice ensures that procurement and business stakeholders receive a report focused exclusively on the risks that matter, allowing them to make informed decisions without sifting through pages of unnecessary information.
2. Map findings to business and compliance obligations
When a non-technical stakeholder sees a report filled with complex risks, it's often difficult for them to grasp the "so what?" That’s why mapping is crucial.
Directly linking a finding to a business obligation bridges the gap between a technical flaw and its real-world consequence. For example, rather than simply stating "SQL injection vulnerability detected," a report should highlight that "This vulnerability directly violates our internal data handling policy and Article 32 of GDPR, potentially leading to significant fines and reputational damage."
This direct mapping transforms complex technical issues into clear compliance and business consequences, ensuring that stakeholders skip the technicalities, immediately understand the full scope of the risk, and act accordingly.
3. Lead with a stakeholder-ready executive summary
The executive summary is what most executives and procurement leaders will read first, and more often than not, it's the only section they'll read in its entirety. A well-crafted executive summary is non-negotiable if you want your technical findings to land with key stakeholders.
This section should be concise and free of jargon, leading with 3-5 high-level takeaways that answer these core questions:
- What: Here are the relevant residual risk(s).
- So What: Here is why it is important to the business and its goals.
- Now What: Here is the specific action that should be taken/recommended.
By providing this clear, plain-language overview at the top, you empower busy stakeholders to quickly grasp the most critical information and make immediate, informed decisions without the need for endless back-and-forth.
4. Use visuals and consistent formatting
Dense blocks of text and jumbled data are the enemies of effective communication. To make your reports more digestible, replace long paragraphs with clear, well-defined sections and incorporate visuals, like a prioritization matrix, heat maps, and simple graphs.
Consistency is key. Using standardized templates and outputs for all your vendor assessments not only improves readability but also builds credibility. When directors oversee multiple vendor reviews, a consistent format allows them to quickly compare and contrast risks, cutting down on review cycles and reducing the "style drift" that can plague reporting across different teams.
5. Define timeframes in business-aligned terms
The phrase "remediate immediately" can cause friction between security teams and business units. Instead of demanding action in technical terms, frame your remediation timeframes clearly, with business-aligned deadlines.
For example, a report might recommend a fix within 30 days to align with a specific regulatory requirement, or suggest a quarterly review to meet the terms of a contract renewal.
By framing urgency in terms of business timelines, regulatory obligations, or contractual commitments, you avoid unnecessary friction and ensure that your security recommendations are viewed as a collaborative effort to protect the business (not an arbitrary demand).
6. Adapt your language for each stakeholder group
To be effective, you must speak the language of your audience. Don't just present technical data; instead, translate it into key findings that directly align with the specific assessment criteria and interests of each stakeholder.
- Procurement leaders: Focus on contractual obligations, service level agreements (SLAs), and the financial or legal risks tied to a finding. Reframe a technical issue as a security gap that could violate a contract's data protection clause, exposing the organization to legal and financial liability.
- Executives and the board: Emphasize high-level business impact, brand reputation, and competitive risk. Aim to translate every technical finding into a clear risk to the business's bottom line and reputation.
- Business unit leaders: Explain how a security issue could disrupt operational continuity or affect client-facing responsibilities. This explanation makes the risk tangible by tying it directly to a stakeholder’s day-to-day work, such as a delayed product launch or a breakdown in customer service.
- Audit and Compliance Teams: Focus on regulatory requirements, internal policies, and control deficiencies. Frame technical findings as non-compliance issues or control gaps that could lead to formal audits, fines, or loss of certifications. For example, instead of "Weak access controls detected," state, "Access controls fail to meet ISO 27001 standards and our internal data governance policy, which could lead to audit findings and loss of certification."
Invest in impact: Can you afford to leave your reports unheard?
Crafting effective risk assessment reports is no longer just a technical exercise; it's a critical communication skill, and an area cyber analysts should invest in. By scoping your reports to the business, mapping findings to real-world consequences, and leading with clear, jargon-free summaries, you transform a technical document into a strategic asset. This approach ensures your message lands the way it was meant to—the first time.
Analysts can lead with these simple steps to improve their reporting, and teams looking to scale their efforts should consider solutions that streamline this process. UpGuard’s AI-Powered Vendor Risk solution is a powerful tool that can automate and enhance the steps outlined above.
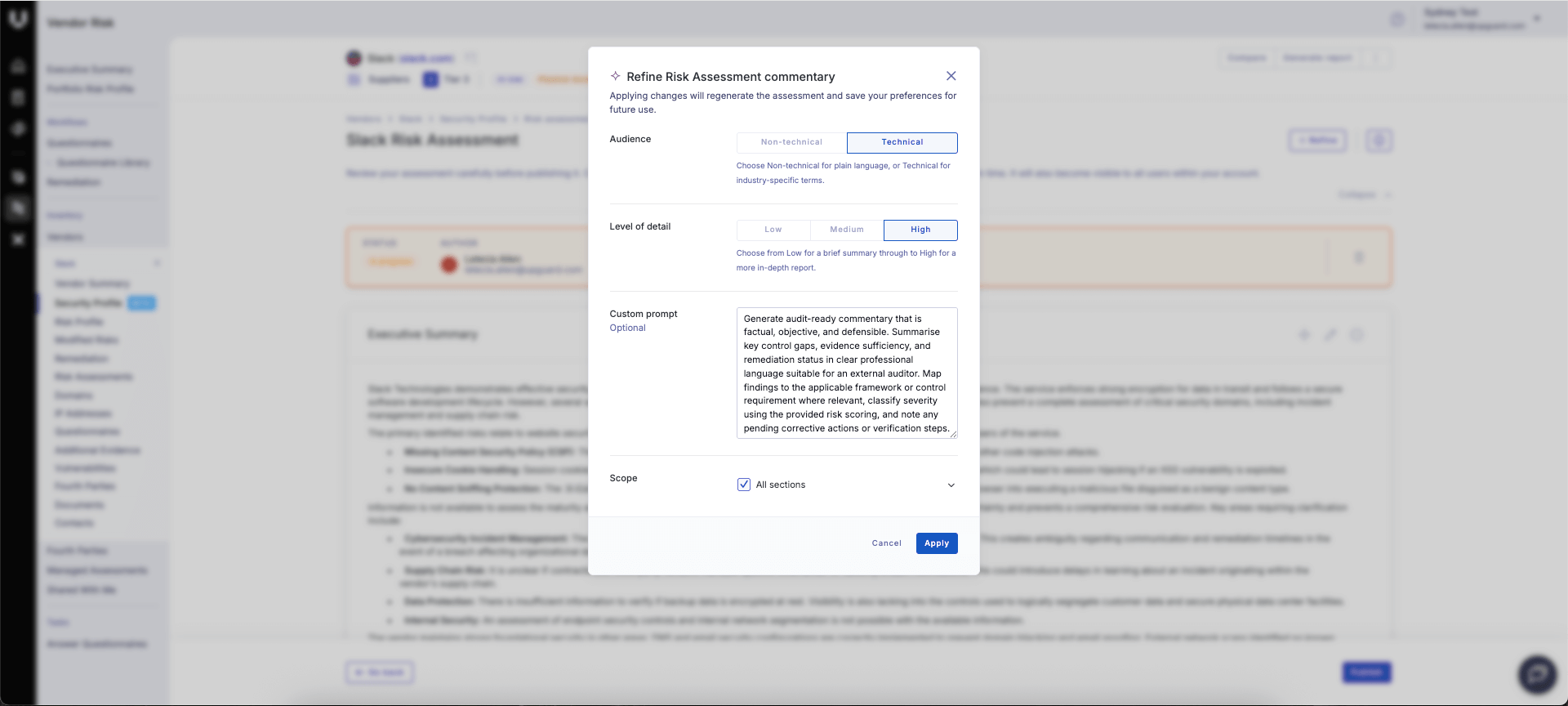
The Instant Risk Assessment feature AI-generates clear, structured reports based on your compliance and risk management activities in less than a minute—no starting from scratch and no heavy edits. Additionally, custom prompts allow you to tailor your report to a specific length and technicality. The result? Stakeholder-ready and perfectly framed reports for your audience, every time.
Ultimately, your approach to assessment reporting determines your team’s impact and efficiency in maintaining your supply chain's security posture. With so much at stake, we challenge you to ask yourself: "Are my reports scoped, structured, and translated so stakeholders can truly understand the risk? Or am I leaving them to interpret technical details on their own?"