TPCRM Framework: Building Digital Trust for Modern Enterprises
Third-party cyber risk management (TPCRM) has emerged as a critical discipline, moving beyond traditional approaches to address the unique and evolving cyber threats posed by vendor relationships.
This post explains the core tenets of TPCRM, outlines key requirements for ideal tools, and suggests implementation strategies for this new, important branch of cybersecurity.
Definition of TPCRM
Third-party cyber risk management (TPCRM) is the systematic process of identifying, evaluating, and mitigating cybersecurity-specific risks associated with using third parties, such as vendors, suppliers, contractors, and partners.
TPCRM represents a significant evolution from traditional third-party risk management (TPRM). While TPRM addresses a broader spectrum of risk domains, including financial, operational, legal, and reputational concerns, TPCRM is a specialized subset that specifically focuses on cybersecurity and IT-related risks posed by third-party vendors.
Robust TPCRM requires a multi-dimensional approach that goes beyond questionnaires and point-in-time assessments. As third-party ecosystems expand, the external attack surface — comprising internet-facing assets, misconfigurations, and exposed data — has become an increasingly critical part of the threat landscape.
Effective TPCRM must account for this growing exposure with continuous monitoring and proactive risk identification.
The broad scope and specialisation of TPCRM present unique challenges that traditional TPRM practices aren’t equipped to manage, underscoring the need for a dedicated cyber risk approach.
Beyond monitoring the external attack surface, effective TPCRM includes continuous due diligence, control verification, remediation tracking, and alignment with security frameworks. It demands cyber-specific visibility into vendor security postures.
TPCRM is not merely TPRM with "cyber" appended, it's a specialized discipline tailored for the specific complexities of the modern vendor threat landscape.
Differences between TPRM and TPCRM
Organizations must recognize that simply relabeling existing third-party risk management (TPRM) programs is insufficient. To transform a TPRM program into a TCPRM program, a fundamental shift in methodology and technology adoption is required. At a high level, TPCRM is differentiated by its expansion of continuous monitoring and nth-party vendor detection capabilities.
Broader scope of continuous monitoring
While good TPRM programs monitor typically also monitor other risk risk domains besides cyber risks, such as financial and compliance-related risks, TPCRM programs further extend this scope to include other cyber risk domains, such as:
- Remote access vulnerabilities
- Counterfeit products
- Reputational risks (stemming from poor security practices)
- Malware infections
- Third-party supply chain attacks.
Because TPCRM places a greater emphasis on a continuous assurance mindset, the program's continuous monitoring component requires a multidimensional approach beyond automated risk scoring.
Such a model typically involves:
- Vendor security questionnaires: Mapping to applicable cyber frameworks and regulations, with the option of customization to broaden the scope of cyber risk domains being queried.
- Security rating: Continuously evaluating external party security postures with fast refresh rates, to produce real-time awareness of evolving vendor risk.
- Notifications: Triggered when vendor security postures drop below a set threshold, support proactive risk management responses.
- Security profile control checks: Automated checks of a vendor's security controls to ensure ongoing alignment with your security standards
Together, these capabilities form an adaptive continuous monitoring framework, capable of covering a wide range of cyber risk domains while enabling proactive vendor risk identification and management
Nth-party cyber risk detection
Besides continuous monitoring, another defining characteristic of TPCRM is its focus on securing the entire interconnected network of vendors, extending beyond immediate third-party relationships to include fourth parties, fifth parties, and so on. This cascade of external parties is what’s collectively known as your nth-party vendors.
This expansion of monitoring scope is important because a vulnerability exploited in a downstream nth-party can create a ripple effect, ultimately impacting the primary organization.
TPCRM aims to provide visibility into these extended digital supply chains, highlighting areas of concentrated risk to support advanced risk mitigation efforts, underscoring the necessity for AI-powered solutions capable of mapping and assessing such complex, multi-layered relationships.
To further clarify the distinct focus of TPCRM, the following table summarizes some of the key differences from traditional TPRM.
TPRM vs. TPCRM: Key differentiators
Why is TPCRM essential for digital trust?
Digital trust is the confidence stakeholders and customers have that an organization will protect the data it is entrusted to process. Without sufficient digital trust, your business will seem too high-risk to interact with.
When customers or partners share data with your company, they expect you to safeguard it not only from internal errors but also from breaches that might come through your vendors. Customers will still hold your company responsible for failing to protect their data if a breach occurs via a vendor.
For stakeholders, customers, and regulators, an organization's state of third-party security is increasingly becoming a primary driver of digital trust.
Stakeholders, customers, and regulators are increasingly becoming aware of the role vendors play in data breaches. Some studies indicate that as many as 73% of breach incidents were caused by a compromised third-party vendor. As such, an organization's state of third-party security is increasingly becoming a primary driver of digital trust.
85% of consumers want to know a company's data and AI policies before buying its products or services.
- Source: 2022 McKinsey survey of 1,300 business leaders and 3,000 consumers globally.
A well-implemented TPCRM framework is vital in reassuring stakeholders, customers, and regulators that an organization is well protected against cyber threats. It serves as a tangible demonstration of an organization's commitment to robust security practices and diligent oversight of its vendor ecosystem.
Demonstrable TPCRM practices, including continuous monitoring, thorough risk assessments, and well-documented remediation efforts, provide the necessary evidence of compliance and responsible data stewardship, fostering customer confidence that their data is handled securely throughout the entire vendor lifecycle.
As such, TPCRM transcends cybersecurity. It also plays a pivotal role in external relationship management, regulatory adherence, and the overall establishment of digital trust.
How TPCRM builds digital trust
A modern third-party cyber risk management (TPCRM) program actively builds digital trust by integrating specific controls directly addressing the security concerns of stakeholders.
This is achieved through a five-pillar framework.
1. Security due diligence
Before a vendor is deemed safe to onboard, they must undergo a thorough due diligence process to ensure they meet your organization's acceptable cybersecurity standards.
Common practices include:
- Security questionnaires or surveys: Vendors answer detailed questions about their security policies, infrastructure, incident history, compliance certifications, etc.
- Evidence collection: Reviewing documents like SOC 2 reports, ISO 27001 certificates, penetration test results, or trust pages.
- Risk assessments: For high-risk vendors, perform a more in-depth audit or assessment of their security program against your standards.
- Risk ratings and analysis: Evaluating the vendor's responses and evidence to identify gaps (e.g., missing encryption, weak access controls) and determine a risk level.
This proactive approach of thoroughly vetting third parties before they're given access to your data highlights the zero-trust lens through which all vendor relationships are governed in a TPCRM program.
Even after a vendor is deemed safe to onboard, trust is not assumed by default, ongoing authentication is still required throughout the relationship lifecycle.
Applying Zero Trust principles to third-party relationships could involve:
- Requiring vendors to authenticate via multi-factor authentication (MFA) before accessing any internal systems.
- Segmenting the network to ensure each vendor's level of access to systems and data is the minimum required to perform their contractual functions.
- Tracking vendor access activities in real time, flagging anomalies or unauthorized behavior.
- Regularly reviewing all vendor connections to ensure predetermined access limits are maintained.
- Ensuring all access points are immediately disabled for all offboarded vendors, ideally automatically.
Additionally, as more vendors integrate AI into their operations, due diligence must extend to Ethical AI Governance, assessing potential algorithmic bias, model security, and regulatory alignment.
2. Vendor inventory and classification
After onboarding, all vendors are meticulously accounted for in a centralized repository. Each vendor in the inventory should be classified into risk tiers based on the level of risk they pose to your organization, ranging from critical to low risk.
All vendors with access to customer data should be automatically classified as "critical." Vendors that will not cause regulatory infractions should they become compromised can be assigned to a low-risk tier (e.g., a landscaping service).
High-risk vendors will need to undergo periodic comprehensive risk assessments.
How an up-to-date vendor inventory and risk classification builds digital trust
Maintaining a single source of truth for vendor information ensures no blind spots in your third-party attack surface. When combined with risk classification, stakeholders have complete confidence that an organization is not only monitoring all external partnerships, but also carefully tracking the impact of high-risk vendors.
3. Automated risk scoring and vendor ratings
Manually reviewing hundreds of vendors is a monumental task. Many modern TPCRM programs leverage tools that calculate a security rating or risk score for each vendor, using a combination of assessment data and external threat intelligence.
For example, a platform might analyze a vendor's questionnaire answers and scan for known vulnerabilities or breaches in the vendor's internet-facing systems, then produce a score (e.g., 0-100 or a letter grade) indicating the vendor's cyber risk posture.
Automated scoring brings consistency and speed to risk analysis. Instead of relying solely on subjective judgment, you get data-driven insights into which vendors pose the highest risk.
A low score might flag inadequate security hygiene or past incidents, prompting immediate follow-up. Conversely, a high score can reassure you that a vendor follows good practices.
AI-driven risk analytics further sharpen the accuracy of risk scores by identifying subtle risk indicators and detecting risk patterns at scale, ultimately resulting in reduced time-to-remediation.
How automated risk scoring builds digital trust
Risk scores provide a transparent, objective metric to share with leadership and vendors. By using quantified risk ratings, organizations can demonstrate a rigorous, quantifiable approach to managing vendor security, further reinforcing trust with auditors and executives that third-party risk is under control.
4. Continuous monitoring and threat detection
Cyber risk is not static. A vendor that was secure last quarter could suffer a breach tomorrow, or gradually weaken in security posture over time. Continuous monitoring is therefore foundational to TPCRM.
Continuous monitoring isn't limited to tracking individual vendor security postures, it should also include tracking the complete scope of security risk commonly linked to data breaches, including data dumps on the dark web and ransomware forums—a commonly overlooked attack vector category.
Continuous monitoring could involve the following data feeds:
- Automated alerts for security changes: Getting notified if a vendor's security rating drops, if their domain is found in a data breach dump, or if new vulnerabilities in their systems become public.
- Threat intelligence feeds: Monitoring the dark web or open sources for news of attacks or leaked data impacting your digital supply chain.
- Integration with IT systems: Using zero-trust network tools to track vendor access in real time..
How continuous monitoring builds digital trust
Continuous monitoring supports dynamic enforcement of Zero Trust. It demonstrates to stakeholders that you're not blindly trusting onboarded vendors to maintain alignment with your cybersecurity standards, you're continuously verifying and tracking their security performance.
5. Compliance and regulatory alignment
Modern enterprises must align their TPCRM efforts with an ever-growing list of cybersecurity regulations and industry standards. Compliance alignment is thus a key component of the TPCRM framework. This involves mapping your third-party risk controls and activities to requirements such as:
- Data protection laws: Regulations like GDPR, HIPAA, CCPA, PCI-DSS, and others mandate high security standards for vendor relationships involving sensitive data, and some of these laws could hold you accountable for third-party data breaches.
- Industry standards and frameworks: Frameworks like ISO 27001, NIST Cybersecurity Framework, SOC 2 Trust Services Criteria, and others all include sections on third-party risk management. To be compliant or certified, you must demonstrate that you assess and monitor vendor security.
- Internal policies: Aligning with your organization's risk appetite and security policies. For instance, if your policy says all critical vendors must have an up-to-date SOC 2 report or multi-factor authentication, your TPCRM program should ensure those checks are in place.
A strong TPCRM program will incorporate compliance checks into its processes. This might mean having standard vendor security requirements that mirror regulatory standards and tracking each vendor's compliance status.
Many TPCRM tools assist with this by tracking vendor certifications, compliance data, and mapping questionnaire responses to specific regulatory requirements.
When a regulator or auditor comes knocking, you should be able to produce evidence that you're managing third-party cyber risk in line with required practices.
How compliance and regulatory alignment build digital trust
Demonstrating compliance isn't just about avoiding fines. It proves to customers and potential partners that your organization takes data stewardship seriously, no matter who's handling it. Verifiable compliance is one of the strongest signals of digital trust.
Steps to implement TPCRM
Implementing an effective third-party cyber risk management (TPCRM) program is a structured, cyclical process. The following steps provide a practical roadmap, helping you establish or mature your TPCRM capabilities.
1. Identify key vendors (including Nth parties)
The foundational step in any TPCRM program is creating and maintaining a comprehensive inventory of all third-party vendors, suppliers, and partners interacting with your organization's systems, data, or critical services.
This inventory must extend beyond direct (first-tier) relationships to identify critical Nth parties (fourth-parties, fifth-parties, etc) within the digital supply chain, as these indirect connections can also introduce significant risk.
For each identified entity, it's crucial to document the specific services they provide, the level and type of data they access or process, such as PII, PHI, or financial data, which is particularly important for businesses in a highly-regulated sector, like finance.
Once the inventory is established, vendors should be categorized or tiered based on their inherent risk level. A common approach involves classifying vendors into tiers (e.g., Tier 1 for high criticality and high risk, Tier 2 for medium, Tier 3 for low).
This prioritization is typically based on factors such as the sensitivity of data being accessed, the potential impact on critical business functions if the vendor's services are disrupted, and the vendor's relevance to specific regulatory requirements (e.g., GDPR, HIPAA, PCI DSS).

Automation can save you significant time with this effort and improve consistency across tiering processes, particularly when onboarding many vendors.
2. Conduct comprehensive risk assessments
Following identification and prioritization, each vendor, particularly those in higher risk tiers, must undergo a thorough risk assessment to evaluate their cybersecurity posture and identify potential vulnerabilities.
A multi-faceted assessment approach is recommended for a holistic and reliable view of vendor risk, as no single method provides a complete picture. Questionnaires are self-attested and can be subjective or outdated; security ratings offer an external perspective but may not capture internal control deficiencies; and technical assessments are often point-in-time evaluations.
Combining these methods allows for data triangulation, leading to a more robust and validated risk profile.
A multi-faceted risk assessment approach may include:
- Security Questionnaires: Distribute detailed, often customized, security questionnaires (e.g., based on frameworks like SIG, CAIQ, or bespoke templates) to gather in-depth information about the vendor's security policies, implemented controls, incident response capabilities, data protection practices, and compliance certifications.
- Security Ratings: Utilize objective, data-driven security ratings to represent each vendor's security posture with a quantifiable score.
- Technical Assessments: This can involve reviewing penetration test results, vulnerability scan reports, and independent audit reports (e.g., SOC 2 Type II, ISO 27001 certificates) provided by the vendor. Organizations might conduct their own limited technical tests or on-site assessments where appropriate and for very high-risk vendors.
Based on the aggregated results from these assessment activities, assign each vendor a quantifiable cyber risk rating or score. Scoring ensures a consistent approach to risk prioritizing during remediation efforts.
Organizations should look for TPCRM platforms that can ingest and correlate data from multiple cyber risk evaluation sources, such as questionnaires and risk assessments, to provide a unified view of each vendor's evolving risk posture.
3. Establish risk mitigation measures
Once risks are identified and vendors are rated, the next step is to implement appropriate risk mitigation strategies and controls tailored to each vendor's level of risk.
Risk mitigation works best when it's collaborative. If you're constantly enforcing controls, revise your onboarding workflow. Vendors should understand and align with your Third-Party Cyber Risk Management expectations from day one.
A TPCRM platform with built-in vendor collaboration tools will simplify the remediation process. Watch this video to see how UpGuard integrates vendor collaboration features into its workflow.
Effective risk mitigation measures include:
- Contractual Agreements: Embed robust security clauses within all vendor contracts. These clauses should clearly define data protection responsibilities, mandate adherence to specific security standards and controls, outline compliance requirements (e.g., with GDPR, HIPAA), establish clear breach notification timelines and procedures, and include the organization's right to audit the vendor's security practices. Service Level Agreements (SLAs) for security performance, such as incident response times and system uptime, should also be specified.
- Security Controls Implementation: Based on the risks identified, require vendors to implement or enhance specific security controls. This could include mandating multi-factor authentication (MFA) for access to your systems, data encryption at rest and in transit, specific network segmentation, or adherence to secure coding practices.
- Risk Treatment Decisions: For each significant identified risk, a formal risk treatment decision should be made. Options typically include:
- Mitigate: Apply controls to reduce the likelihood or impact of the risk.
- Transfer: Shift some of the financial impact of the risk to a third party, often through cyber insurance (though this does not absolve your organization of its responsibility for due diligence or reputational damage).
- Avoid: If the risk is too high and cannot be adequately mitigated to an acceptable level, the organization may decide to terminate the relationship with the vendor or not engage with them in the first place.
- Accept: For low-level risks that fall within the organization's defined risk appetite, a formal decision to accept the risk may be made, typically requiring sign-off from appropriate management.
- Remediation Plans: When vulnerabilities or control gaps are identified, work collaboratively with vendors to develop clear remediation plans. These plans should include specific actions, timelines, and responsibilities. Track the progress of these remediation efforts and verify that vulnerabilities are effectively closed.
Risk mitigation measures should be integrated into your third-party risk assessment workflow. Watch this video to learn how UpGuard incorporates this phase in a single vendor risk assessment lifecycle.
4. Integrate continuous monitoring
TPCRM cannot be effective if it relies solely on point-in-time assessments. The dynamic nature of cyber threats and the evolving security postures of vendors necessitate the integration of continuous monitoring tools and processes. This involves tracking vendor security performance, compliance status, and emerging threats in real-time.
Key aspects of continuous monitoring include:
- Scope of Monitoring: Continuously track changes in vendor security ratings, new publicly disclosed vulnerabilities affecting the vendor or their technology stack, reports of data breaches involving the vendor, drifts in their compliance status, and other relevant risk indicators. This provides accurate, up-to-date risk data, which is crucial for monitoring vendor data security and network security to prevent breaches.
- Automated Alerts: Configure monitoring systems to generate automated alerts for significant negative changes in a vendor's risk profile or upon detection of a security incident related to the vendor. .
- Proactive Defense: Continuous monitoring transforms TPCRM from a reactive, rear-view mirror perspective to a forward-looking, proactive defense, allowing timely intervention before a potential risk materializes into an actual incident. Organizations failing to implement robust continuous monitoring are essentially accepting periods of blindness to potential threats, significantly increasing their risk exposure.
5. Review and evolve regularly
A TPCRM program is not static. It must be an evolving component of the organization's overall risk management strategy. This requires regular review and adaptation to remain effective against the constantly changing threat landscape, evolving business objectives, and new regulatory requirements.
An evolving TPCRM program is a learning program, continuously refining its defenses based on past experiences, current intelligence, and future projections.
Key activities for program review and evolution include:
- Data-Driven Analysis: Utilize the data and metrics generated by TPCRM activities to objectively assess program effectiveness, identify areas for improvement, and demonstrate value to stakeholders. Important metrics include the number of identified versus mitigated risks, the cost of managing third-party risks, mean time to detect (MTTD) and mean time to remediate (MTTR) vendor vulnerabilities, trends in vendor security ratings, compliance adherence rates, and mean time to onboard (MTTO) new vendors.
- Consider Value at Risk (VaR): When prioritizing assessment efforts and allocating mitigation resources, consider the "value at risk." This involves evaluating the potential financial impact of business disruptions, data loss, or other material consequences stemming from a vendor-related incident. Focus on vendors that pose the greatest potential monetary and operational loss to the organization; they should all be grouped in your most critical tier.
- Strategic Prioritization of Assessments: Employ complete portfolio visibility and comprehensive risk intelligence to strategically prioritize vendors requiring comprehensive risk assessments. This is more effective than assessing all vendors equally or relying on simplistic criteria like contract size or annual spend, since it ensures efficient resource allocation.
- Maturity Models: Leverage established TPRM maturity models to benchmark current program capabilities, identify gaps, and develop a roadmap for progressive enhancements toward a more proactive and resilient state.
- Formal Review Process: Establish a formal, periodic process for reviewing the TPCRM program. This review should incorporate lessons learned from past incidents or near misses, new threat intelligence, changes in the regulatory landscape, and shifts in the organization's business strategy or third-party risk appetite.
Best practices for TPCRM
Achieving consistent vendor risk reduction and fostering digital trust requires adherence to proven Third-Party Cyber Risk Management (TPCRM) best practices. The following practices will help you establish a scalable, repeatable, and effective TPCRM program.
1. Centralize your vendor management and standardize processes
A cornerstone of effective TPCRM is centralized vendor management. This involves maintaining a unified, up-to-date inventory and risk profile for every third-party relationship.
Accompanying this should be standardized processes for the entire vendor lifecycle, from initial evaluation and onboarding through ongoing monitoring to eventual offboarding. Such standardization ensures consistency and that critical steps are not overlooked, especially as the number of vendors grows, making ad-hoc approaches unmanageable.
2. Adopt a risk-based tiering model
Risk-based tiering is a critical best practice that ensures efficient security resource allocation to high-risk vendors. By categorizing vendors based on factors such as data access, service criticality, and potential financial impact, organizations can prioritize due diligence and monitoring efforts where they will have the most impact.
3. Clearly define roles and responsibilities
Clearly defined roles and responsibilities for TPCRM activities across various departments, such as procurement, IT, legal, and business units, are essential to prevent tasks from falling through the cracks and ensure accountability.
4. Leverage automation
Automation should be leveraged wherever feasible to handle repetitive tasks like data collection, questionnaire distribution, basic security checks, and alert generation. This not only improves efficiency and consistency but also frees up security personnel for more strategic risk analysis and mitigation planning.
Modern TPCRM tools achieve an optimum balance between automation and user oversight, helping you achieve scalable impact while maintaining complete control in the driver's seat.
5. Foster a security-aware culture through ongoing security education
Effective TPCRM also heavily relies on fostering a security-aware culture that extends to vendor relationships. While organizations typically do not provide formal security training to their external vendors, promoting ongoing communication and security education is paramount.
This involves clearly communicating your organization's security standards, policies, and expectations to all third parties from the outset of the relationship. Sharing relevant, anonymized threat intelligence that could impact the vendor (and by extension, your organization) can foster a collaborative security environment.
Most importantly, vendors should be encouraged to disrupt the trend of poor vendor security hygiene by investing in a robust Human Risk Management program.
6. Adopt and utilize cybersecurity frameworks
Established cybersecurity frameworks provide the essential blueprints for building a defensible and effective TPCRM program. Frameworks like the NIST Cybersecurity Framework (CSF), ISO 27001, and, particularly for healthcare, the HITRUST CSF offer structured, comprehensive, and widely accepted sets of controls and best practices.
- The NIST CSF offers a high-level structure for identifying, protecting, detecting, responding to, and recovering from cyber threats, which can be effectively adapted for evaluating vendor capabilities. Specific NIST publications like SP 800-53 (security and privacy controls) and SP 800-161 (cybersecurity supply chain risk management) provide more granular guidance.
- ISO 27001 is the international standard for Information Security Management Systems (ISMS). Assessing vendors against ISO 27001 controls or verifying their certification provides a strong indicator of their security maturity. ISO 27036 specifically addresses information security for supplier relationships.
- The HITRUST CSF is particularly valuable in the healthcare sector as it harmonizes multiple standards (including NIST and ISO) into a single, certifiable framework, emphasizing continuous monitoring and validation of controls. Aligning TPCRM practices with these frameworks demonstrates a commitment to industry best practices, facilitates regulatory compliance, and provides a common language and consistent criteria for assessing vendor security postures, making comparisons more meaningful and risk management more robust.
Here's a helpful table summarizing how TPCRM supports alignment with key compliance and cyber framework standards.
Key compliance frameworks & TPCRM alignment
Tools and technologies for TPCRM
The complexity and scale of modern vendor ecosystems necessitate using specialized tools and technologies to manage third-party cyber risk effectively. These solutions offer capabilities that automate processes, provide deeper insights, and enable proactive risk management, ultimately contributing to the establishment of digital trust.
Key capabilities found in advanced TPCRM platforms include:
1. AI-driven scoring
Artificial intelligence and machine learning algorithms are increasingly used to analyze large quantities of data from diverse sources. This includes security ratings, vendor questionnaire responses, threat intelligence feeds, and even publicly available information.
The AI then generates dynamic, objective risk scores for each vendor, helping organizations quickly identify and prioritize their highest-risk relationships. This data-driven approach moves beyond subjective assessments to provide a more consistent and scalable method for evaluating vendor cyber risks.
The mechanisms behind AI-driven scoring can also be applied to scale the detection of security control gaps to streamline vendor risk assessments, addressing the compliance aligment objectives of TPCRM.
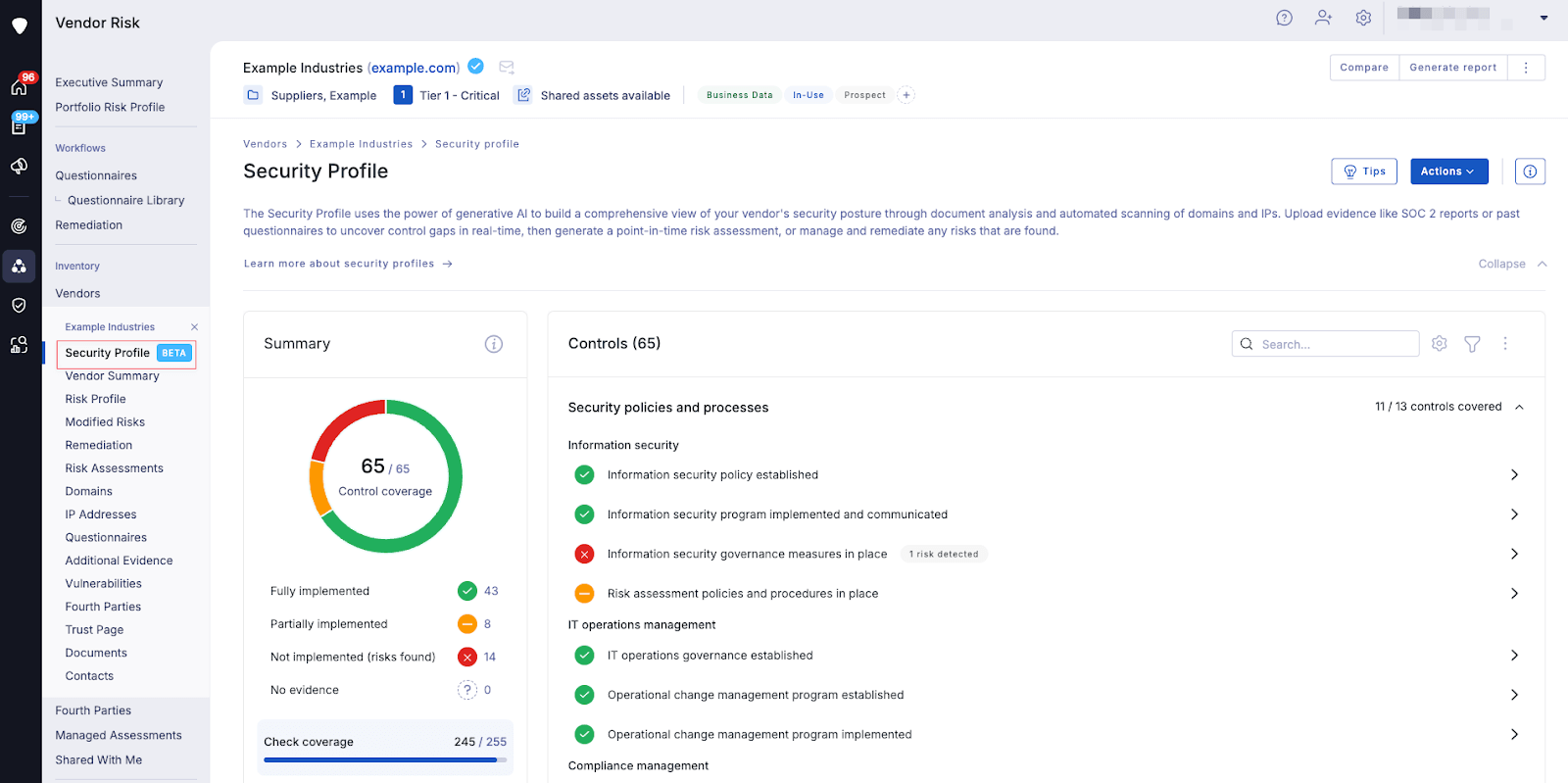
2. Automated workflows
Automation is crucial for streamlining the numerous processes involved in TPCRM. This includes automating vendor onboarding, the distribution and collection of security questionnaires, the initial analysis of assessment responses, the generation of risk alerts, and the tracking of remediation efforts.
Automated workflows enhance efficiency, reduce manual effort, ensure consistency, and allow security teams to focus on more strategic risk mitigation activities.
For an example of how a TPCRM solution like UpGuard leverages automation in its workflows, watch this video:
Learn how UpGuard transforms TPRM with AI.
3. Integrated breach notifications and threat Intelligence
Modern TPCRM tools often integrate external threat intelligence feeds to offer timely alerts of security incidents impacting your vendor ecosystem. Such integrations enable proactive risk mitigation, helping you secure your public-facing assets as a new threat spreads throughout the global vendor ecosystem, and not in the aftermath.
The CrowdStrike incident is a recent example a major security event impacting the vendor ecosystem that users with access to a threat intellignece feed were able to efficiently respond to.

4. Unified dashboards and reporting
Centralized dashboards offer a real-time, consolidated view of the organization's overall vendor risk posture. These dashboards could display individual vendor risk scores, the status of ongoing assessments, outstanding remediation tasks, compliance levels, and the distribution of critical vendors in the third-party network, represented in a vendor risk matrix.
This unified visibility facilitates informed decision-making for security leaders and provides valuable reporting for executive management and boards.

FAQs about TPCRM
As third-party cyber risk management (TPCRM) becomes increasingly critical, several common questions arise. Addressing these helps clarify the scope, applicability, and core components of a modern TPCRM program.
What is the difference between TPRM and TPCRM?
TPRM (third-party risk management) is a broad practice that manages all types of risks posed by third-party relationships, including financial, operational, strategic, and compliance risks.
TPCRM (third-party cyber risk management) is a focused subset of TPRM that deals specifically with cybersecurity risks spanning third and nth-party vendors.
Can small businesses benefit from TPCRM?
Yes, absolutely. Small businesses also rely on third-party software, cloud services, contractors, and suppliers, and any of these could introduce a cyber risk.
A small business is likely a vendor for a larger organization, and by leveraging TPCRM principles to improve its overall security posture, a small business reduces the risk of becoming an attack vector to a large-scale data breach.
Is continuous monitoring mandatory in TPCRM?
From a best-practice perspective, continuous monitoring is considered a cornerstone of effective TPCRM.
Cyber risks can evolve quickly; a vendor that was secure at onboarding might be compromised a month later. Without continuous monitoring, problems would only be discovered at the next scheduled risk assessment (or after a breach happens).
Reinforcing digital trust with a modern TPCRM program
A modern third-party cyber risk management (TPCRM) program is key to advancing corporate security maturity towards a proactive approach to managing supply chain risks by embedding risk awareness into every stage of the vendor lifecycle.
The foundation of this evolution lies in automation and real-time risk intelligence, which deliver the visibility and contextualization required for faster, more informed decision-making. With these capabilities, security teams are better equipped to support digital transformation initiatives while maintaining operational resilience.
To future-proof this strategy, organizations must be capable of addressing stakeholder concerns about evolving third-party attack threats, namely the increasing adoption of AI technology and the sophisticated third-party cyberattacks that will likely result from this transformation.
This could involve applying Zero-Trust Architecture to all third-party access points and clear ethical AI guidelines governing how vendors develop and deploy AI systems, focusing on fairness and transparency. Seamless cross-board compliance integrations will also likely become essential to support data protection compliance across jurisdictions without sacrificing the agile characteristics of TPCRM.
When these elements are integrated into a unified TPCRM approach, organizations not only reduce their exposure to evolving vendor-related cyber risks but also transform their third-party security into a strategic enabler of innovation, growth, and long-term competitive advantage.