The modern cybersecurity landscape is being redefined by the human element. With every individual user accessing your network, tools, and sensitive data, managing your human attack surface is growing more critical than ever. Yet, as user autonomy increases and AI erupts, this task has become increasingly difficult, if not impossible, with yesterday's tools.
The compliance-focused approach we use cannot adequately manage the risks associated with the modern user, where the proliferation of SaaS applications, the explosion of Shadow AI, sophisticated phishing, and supply chain complexity fuel increased risk. What we’ve found is that in this expanding landscape, security teams are flying blind, lacking visibility into the true scale of human risk. User data is scattered across siloed tools, making the process of gaining an "identity-level view of risk" too complex for most teams to perform consistently, at least until now.
In this first installment of our User Risk series, we'll address the aspect that keeps most leaders flying blind: visibility. We'll discuss the modern visibility gap—which encompasses unmanaged Shadow SaaS (including Shadow AI), risky application permissions, and fragmented identity-based risk data—and how UpGuard built User Risk to address this exact concern, gaining full visibility over your workforce.
The visibility gap: You can't protect what you can't see
Your attack surface is not just the firewall—it’s the human identity and every endpoint they control. These endpoints, including application permissions, personal cloud storage, and device configurations, result in a human-shaped visibility gap in your defenses. While this gap was once manageable during slower technological expansion and adoption, the rapid spike in both over the last few years has made it increasingly difficult for traditional security tools to keep up.
Let's first discuss legacy issues. Traditional tools often address common human risk vectors—such as risky permissions, phishing attempts, and compromised credentials—as siloed, point-in-time events across various applications, dashboards, and manual processes (more on these later). Because these critical signals are scattered so broadly, organizations struggle to aggregate them into a single, comprehensive view of their human attack surface.
When it comes to modern threats, the traditional stack is also failing to manage the sharp rise in shadow AI (the use of unapproved AI applications), the latest emerging subset of shadow IT. As our recently released Shadow AI report details, its huge appeal—driven by efficiency—has made it popular among both employees and security leaders alike, and it can be deployed easily outside the purview of standard human risk security procedures and tools.
The most common reason for using unapproved tools was much simpler: they used them because it was easier. Second, when applications that employees wanted to use were blocked, they were just as likely to find a workaround for accessing those tools as they were to stop using them. - UpGuard, The State of Shadow AI Report 2025, page 21.
This inability to unify both new and old risks converges into a single, glaring visibility gap that security leaders are aware of but struggle to effectively manage and remedy. With the current playbook failing to provide full visibility into common user risk behaviors and the rise of newer, emerging threats like shadow AI, leaders are left unable to fully understand the true scale of modern human risk and how to secure it. As the saying goes, you cannot protect what you cannot see.
The old playbook can’t keep up
We’ve discussed the issue of visibility in modern-day human cybersecurity risk and revealed that the traditional playbook is proving ineffective in closing this visibility gap. But why exactly does the old playbook fail at providing in-depth and actionable visibility? To put it simply, the existing it was not designed to look inside the corporate perimeter, follow the user, or consolidate reporting—key features needed in today's expanding human risk attack surface.
This lack of comprehensive visibility is not going unnoticed by security leaders. Participants in our User Risk Early Access Program (EAP) consistently express frustration that current solutions provide only fragmented data and limited scope, forcing reliance on time-consuming manual processes. They emphasize the struggle to accurately determine what they can and cannot see, noting that the constant challenge is to fill those gaps to gain proper coverage.
Leaders openly admit to being "blind" to many of the actions users take, especially concerning unauthorized SaaS and Shadow AI. This critical gap between what leaders know they should see and what their tools allow them to see is the central point of friction in modern human risk management, often leading to a failure to truly identify risk.
Visibility failures in current human risk management
- Lack of comprehensive visibility: Existing directory systems (like Microsoft Entra) only track application usage via corporate credentials, missing significant shadow saas or shadow AI usage via personal credentials. Network tools track traffic but lack the proactive insight into user intent.
- Data silos and manual processes: Security data resides in separate silos (DLP, phishing logs, application logs). Achieving a holistic, identity-level view of risk requires time-consuming manual export and normalization, often resulting in the critical task not being completed.
- Limited identity context: Traditional systems often list all compromised emails, including those belonging to former employees who are no longer relevant, requiring manual sifting to isolate active user risks. This renders it impossible to generate a true identity-based risk score.
- Limited guidance during friction: When tools block risk, the user is left without the approved alternative. This creates unnecessary friction, driving users directly toward unauthorized workarounds, thus actively worsening the blind spot.
The true cost of lacking visibility
We’ve discussed why visibility is failing, but what about the real-world consequences? As many are aware, visibility is not just an option in modern cybersecurity—it’s the cornerstone of a robust security posture and a fundamental requirement. When you lack a clear view into your human attack surface, the reality is that you’re left open and exposed to a myriad of threats.
Security leaders have long been challenged by common workforce risks, including compliance, data leakage, and vendor risk, which are already difficult to manage due to the use of siloed tools and fragmented data. However, the stakes are now significantly higher: these traditional threats are compounded by the rapid emergence of Shadow AI.
This new breed of threat involves sensitive corporate data, including intellectual property (IP), proprietary financial information, system credentials, personally identifiable information (PII), and client secrets, being fed into unmonitored third-party models with zero visibility into how that data is stored or processed.
Without this complete visibility into both common and emerging threats, every single user is becoming a more targetable and active risk across the organization. This leaves you with the daunting reality that all it takes is one user making the wrong decision to escalate a risk to a full-blown breach.
As one User Risk EAP participant succinctly put it, the greatest danger lies in the inherent fragility of human decision-making: no matter how robust your technical controls, policies, or standards are, it only takes one employee making one bad decision in a single moment for everything to fall apart.
Without a complete picture of their full human attack surface, your security teams are left with massive, unmanaged exposure that not only poses risk but also affects vendor due diligence, compliance reporting, and your overall cybersecurity posture. This crisis of visibility is why security leaders are turning to new discovery solutions, as it has been proven that traditional tools are ineffective in monitoring and managing this core concern in the evolving landscape of human risk.
Closing the visibility gap with User Risk
As we've stated previously, you can't protect what you can’t see. The sheer scale of today's user-driven risk, alongside new threats like shadow AI and the unmanageable long tail of unsanctioned SaaS, demands a solution built specifically to provide visibility into the modern human attack surface.
You need a singular platform that can gather comprehensive user risk data from various signals—such as identity and sanctioned app data from Microsoft Entra and Google Workspace—and aggregate it with critical insight into unapproved AI application usage.
True visibility at this breadth is a substantial request, but we've met it. Our solution to this demand is User Risk, UpGuards' human risk management platform within our cyber risk posture management (CRPM) ecosystem.
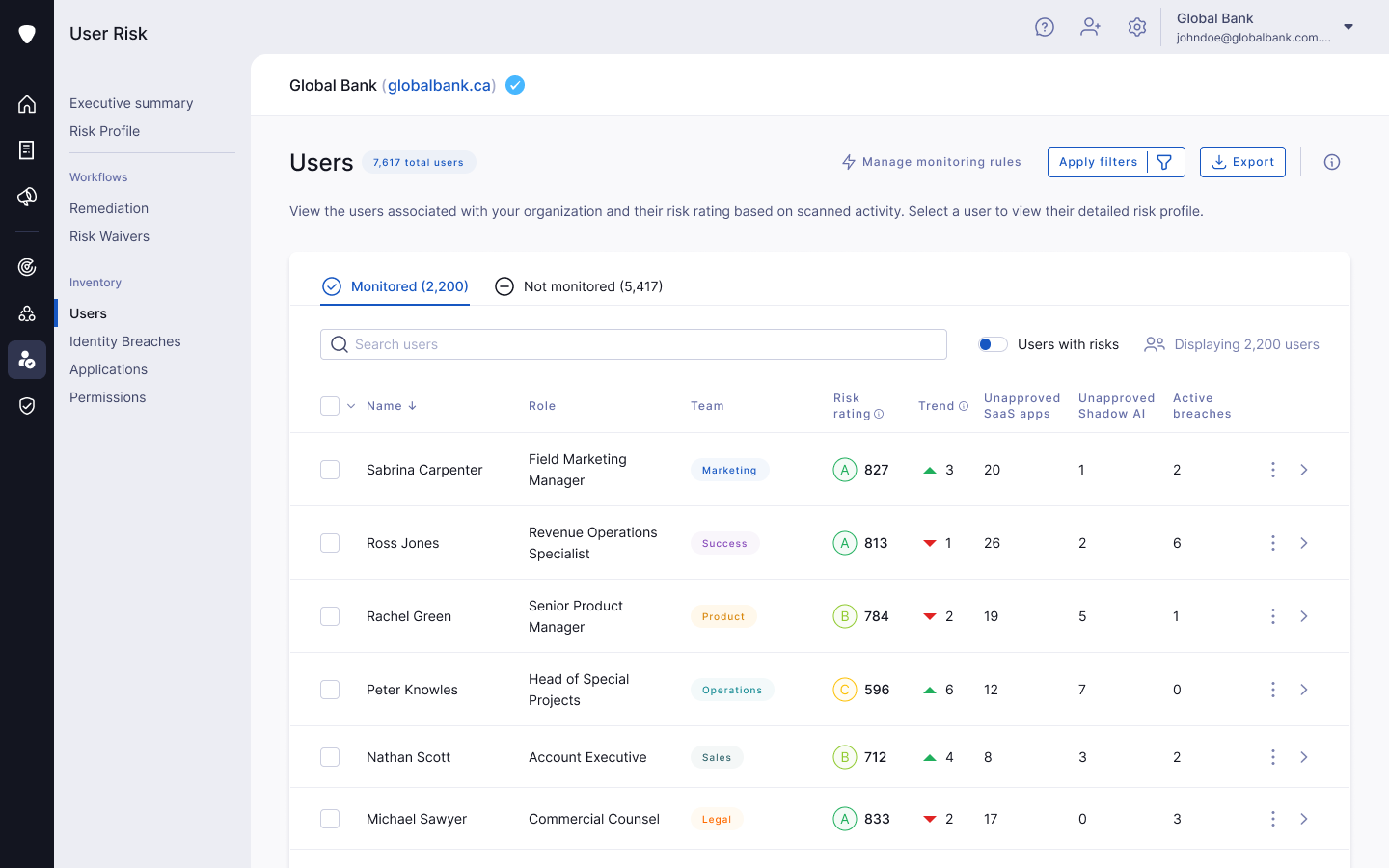
User Risk closes the critical visibility gap by using our Global Risk Inference Domains (GRID) technology to unify signals across your workforce, providing full identity-based coverage. This approach extends far beyond the limited scope of traditional systems, such as Data Loss Prevention (DLP) and Cloud Access Security Broker (CASB) tools.
Legacy network proxies (CASB/DLP) offer only limited, superficial traffic monitoring and are blind to the user identity when Single Sign-On (SSO) is bypassed—a critical technical blind spot. Similarly, security awareness training (SAT) is often theoretical and episodic, functioning as a "check-the-box" compliance exercise rather than providing the continuous, identity-based insights needed to manage dynamic daily risks. This combination of limited network view and intermittent behavior training leaves significant gaps in crucial areas, such as Shadow SaaS and risky application permissions.
User Risk fundamentally addresses these deficiencies. Where traditional tools offer only partial or fragmented visibility, User Risk delivers full, continuous coverage across the board. This unified approach provides true browser-level context, eliminating the critical SSO blind spot, managing the unmanageable long tail, and detecting threats like shadow AI usage where the old playbook fails entirely. User Risk is engineered to fill these structural gaps by providing the identity-level view required to turn passive data into active, identity-based security.
See your true human attack surface with User Risk
We’ve seen the severity of the Visibility Gap and the structural failure of traditional security tools to detect human-shaped threats. We’ve established that visibility isn't a feature; it's the non-negotiable prerequisite for modern security governance and the first step any organization must take before implementing applied action and lasting behavioral changes.
We wholly believe that User Risk provides this essential step forward for any organization seeking to secure its workforce. And while we’ve highlighted how User Risk is the definitive way forward for gaining visibility, it doesn't stop there. It's only when visibility is coupled with its features for enabling automated action and building secure habits with contextual nudges that you can turn the human-shaped visibility gap into your first line of defense.