Solving Human Risk: Automate Governance and Prioritize Action
In our previous blog post, “Closing the Visibility Gap,” we established that visibility is the first step in managing the modern human attack surface; however, prioritizing that data is the next major concern for any CISO. Prioritization of human risk data is critical, as it directly informs governance and effective high-level decision-making. Simply put, prioritization is crucial to driving action.
The current playbook offers little support in that regard, leaving SOC teams with vast pools of data from siloed tools. Each separate dashboard compounds the problem with its own set of alerts, forcing leaders to constantly ask:
How do I know which teams and individuals pose the highest risk, and how do we allocate finite resources with precision?
In this post, we’ll discuss the second aspect of mitigating human risk in your organization: prioritization to enable effective governance. We’ll examine how the traditional playbook has faltered under the weight of modern user risk, resulting in alert fatigue, increased organizational risk, and a negative business impact.
Finally, we will explore how User Risk addresses this concern through automated, policy-driven human risk management.
The need for human risk data prioritization
Whether you're using the legacy playbook of siloed tools or have invested in our User Risk solution, the next step in taking action based on those insights is prioritization. Beyond simply seeing individual data points, you need to convert them into prioritized risk signals.
This enables you to gain a comprehensive understanding of your overall human risk and take action where risk is more concentrated. A comprehensive view is vital because not all human risks are equal, and leaders must focus their efforts on users at higher risk and with greater access, making this an imperative for modern security teams.
For example, security teams have access to users' job roles, permissions, and app usage data; however, these are often just disparate data points. This is where contextual prioritization becomes essential, as it helps make connections between these signals and drive action.
You identify a highly sensitive group—like C-suite members—who have access to critical data. You can then overlay which of these users are also using unapproved AI applications from unmonitored vendors, and which have granted overzealous permissions to those apps.
The core principle is clear: when singular data points are translated into prioritized risk signals, it provides security leaders with the context and insight needed to secure their workforce, fine-tune their action plans, and allocate limited resources to address the risks most critical to business operations.
Examples of the prioritization insights that drive clear, actionable strategies include:
Policy violation status:
- Insight: Cross-reference aggregated data against current security policies to identify specific violations and non-compliant user behaviors.
- Drives Action: Pinpoint individual users or teams that require immediate remediation or policy intervention.
Application approval status:
- Insight: Compare usage data against the established application security baseline.
- Drives action: Confirm whether newly discovered applications are sanctioned or approved for use, triggering appropriate vetting or blocking actions as needed.
Emerging threat assessment:
- Insight: Monitor the latest rise in Shadow IT, and more specifically, Shadow AI (unapproved AI applications) as detailed in our 2025 Shadow AI report.
- Drives action: Quantify the scale and severity of these new, unmanaged risks entering the organization’s perimeter to justify policy changes or technology investment.
Read the full 2025 Shadow AI report here >
Stakeholder reporting & investment:
- Insight: Glean insights to quantify the human risk levels across the organization.
- Drives action: Manually builds reports for management, allowing them to pinpoint necessary interventions and justify program investment.
Remediation planning and execution:
- Insight: Synthesize all prioritized violations, applications, and threat data across the organization.
- Drives action: Structure and execute clear, prioritized remediation plans that ensure resources are focused on the highest-risk users and vulnerabilities, minimizing operational disruption.
Unfortunately, this is where the traditional playbook falls short. Security teams must manually compile all the data points to align with these prioritization factors to begin driving remedial action. Effectively, security teams are relegated to acting as data analysts, investigating signals and seeking feedback—wasting valuable resources that should be focused on stopping specific and time-sensitive threats. And this manual burden does come at a high cost.
The high cost of manual prioritization: Ineffective governance
Prioritizing human risk data manually is a challenging process, and it often becomes impossible when handling hundreds of risk signals. This manual process poses significant organizational concerns, ranging from operational friction to widespread alert fatigue among security teams, which leaves the door open for critical alerts to be missed.
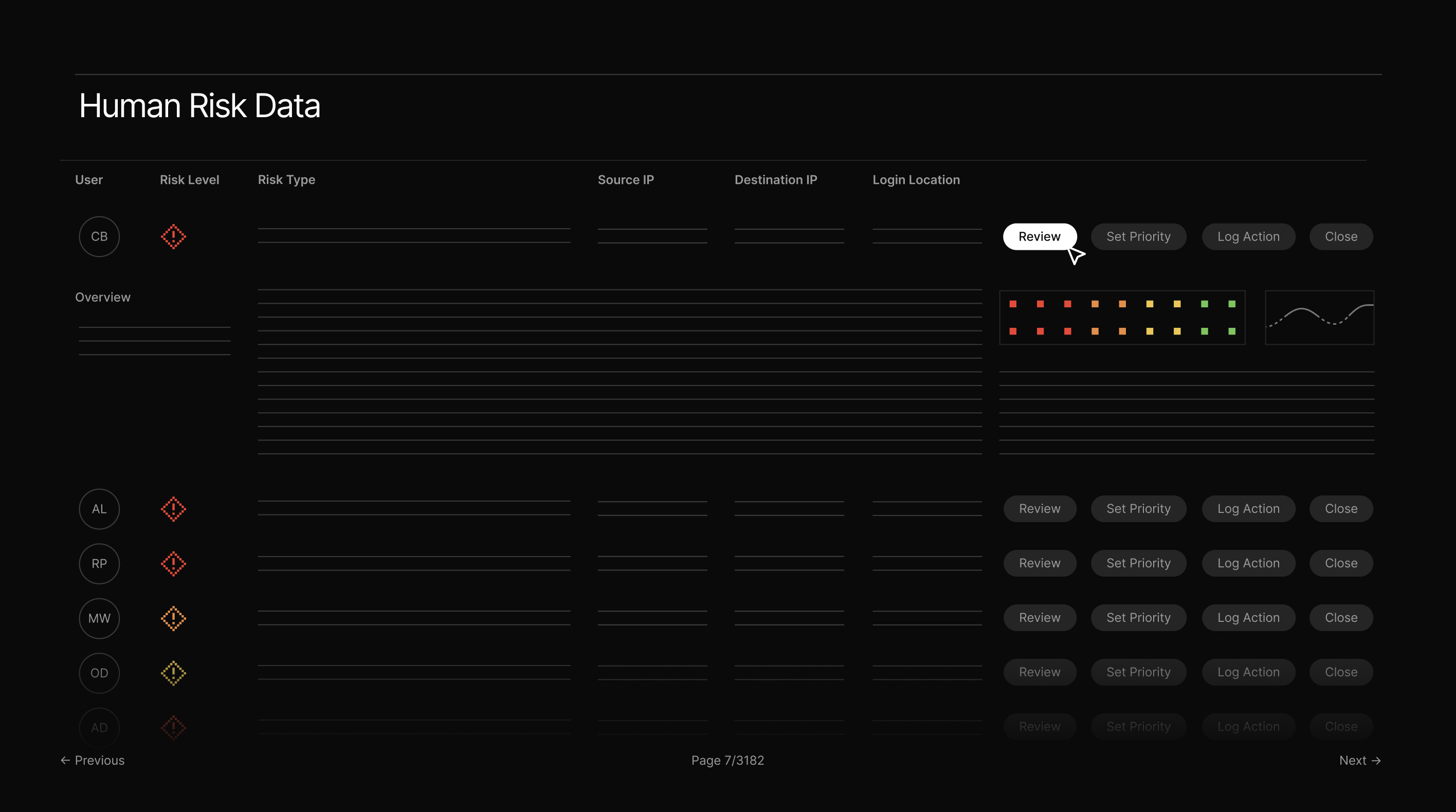
The lack of a robust prioritization model hinders strategic governance, wastes analyst resources, and contributes to unchecked expansion of the attack surface, resulting in pervasive, unmanaged exposure across the organization.
Here are the real impacts of failing to prioritize, broken down into the measurable costs to your security team and business.
Business impact:
- Wasted resources and costs: High-skill, expensive security analysts are forced to manually export and aggregate risk data from multiple point solutions to drive insights, rather than focusing on remediating the highest impact risks or performing high-value security work. This equates to significant operational waste.
- Strategic failure: Leaders cannot consistently quantify human risk or effectively understand the posture of their workforce. This makes it impossible to demonstrate a return on security investment (ROI) or justify strategic governance to the board.
Risk to business security:
- Alert fatigue: The high volume of scattered, non-prioritized alerts leads to alert fatigue, thereby increasing the likelihood that genuine, critical threats will be overlooked.
- Increased attack surface: Without a clear, prioritized action plan, the rapid growth of SaaS usage and the rise of generative AI continue unchecked, expanding the unmanaged portion of the attack surface and increasing exposure to data leakage and intellectual property loss.
Burden placed on security teams:
- Operational friction: Teams are stuck in a constant state of reactive firefighting and endless contextual investigations, leading to burnout and decreased effectiveness.
- Ineffective governance (No clear path forward): Leaders struggle to consistently enforce security policies, as they are often buried in documents rather than integrated into a system that automatically triggers alerts and provides real-time coaching.
Clearly, the current playbook struggles to provide visibility; even when it does, the signals are often unprioritized and require manual analysis. And this slow, laborious process leads to massive organizational and security deficits that can't manage the rising scale of the modern human risk landscape.
What's needed is a single solution that provides visibility and prioritized, actionable data, all in one consolidated platform. Our newest addition, User Risk, delivers both. As the human risk management platform within our CRPM ecosystem, it is designed for the modern attack surface, giving teams the insights and direction needed to reduce human risk more effectively.
The User Risk action engine
We've established that prioritization is a fundamental requirement for managing the modern human attack surface. This is precisely why we have made it a core pillar of the User Risk platform.
Think of User Risk as an engine that uses prioritization to drive action. It continuously aggregates raw data from various tools and browser activity monitoring to keep a constant pulse on your human risk perimeter. It then contextualizes and prioritizes all findings in accordance with your existing security policies and governance rules.
This contextualized and prioritized data is then presented within our User Risk dashboard to produce a single, unified view of your human attack surface. With this unified view, leaders can quickly take the necessary actions based on the findings, effectively automating the tedious aspects of governance and driving them from raw data to action in seconds.
High-level prioritization with the Unified Risk Score
At a high level, we transform this raw, centralized data into an immediate action signal: what we call the Unified Risk Score. This is the single, quantifiable metric that cuts through the noise and provides absolute clarity on user risk within your workforce, per individual or team.
This score immediately answers the most critical operational question: "What should I fix first?"—and who poses the greatest threat right now. It entirely automates the stakeholder reporting and investment burden by providing management with a single, clear metric.
The intelligence behind this score is also compounding: User Risk prioritizes your Shadow IT with instant vendor risk context. It doesn't just discover a new Shadow SaaS app; it instantly cross-references it with your vendor risk program to see if that newly discovered app is from an approved, monitored vendor. This is the only platform that transforms a simple discovery into a prioritized, actionable insight that siloed tools can't provide.
AI-driven prioritization and granular governance
Visibility and a unified score are powerful, but action requires intelligence. This is where the AI analyst prioritization feature comes into play. Instead of treating every signal as equal, our AI takes your defined security policies and turns them into dynamic, automated governance rules.
This instantly solves the manual burden of policy violation status and emerging threat assessment by automating comparison and quantification.
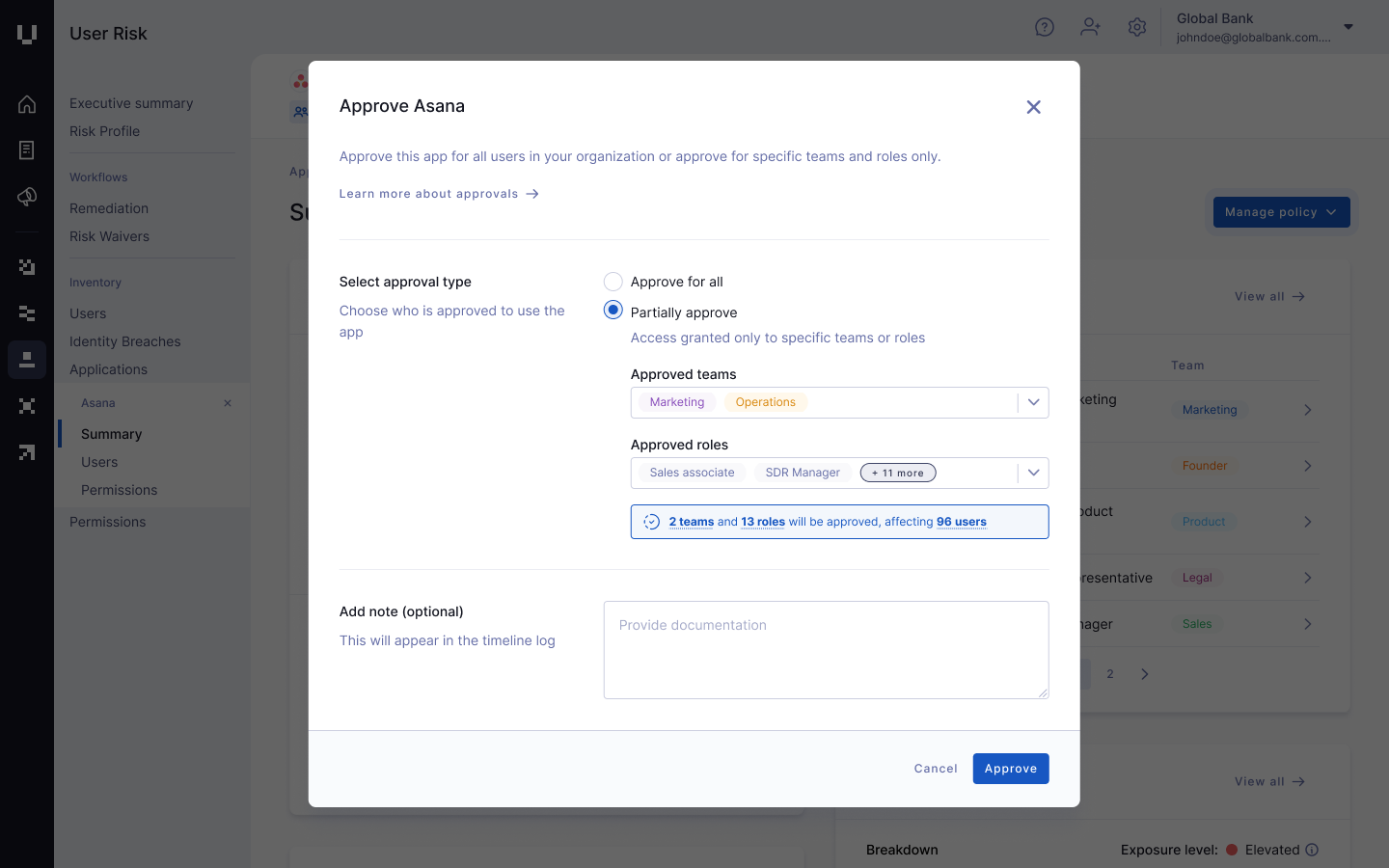
This intelligence enables granular SaaS & AI governance, allowing leaders to define their application security posture with precision. Leaders can create rules that define which applications or specific SaaS and AI applications to approve, restrict, or monitor based on their risk level, category, or the teams that use them.
To close the loop on granular governance, the AI Analyst identifies the most critical human risks based on context, intent, and data exposure, and then provides detailed, actionable remediation advice alongside every prioritized risk. This ensures your team focuses its finite resources on the few threats that genuinely matter.
From reactive to active governance
The key shift is moving away from the reactive posture of traditional security (post-discovery blocking or investigation). Automated risk generation transforms your policies into a proactive risk detection system that continuously analyzes user activity against your established rules, automatically prioritizing and surfacing risks when a policy is violated.
User Risk enables security leaders to transition to an active, automated governance state, where policies consistently drive actions across the entire human attack surface. This allows security to manage the continuous and growing landscape of human risk, rather than constantly chasing individual signals reactively.
This continuous cycle of enforcement and monitoring is the only way to manage risk and prepare for the ultimate last step in solving human risk: lasting behavior change.
Prioritize human risk and take action with User Risk
Human and workforce risks are growing as the landscape expands, and the way we manage risk within this space is no longer working. We've discussed the common struggles with both visibility and effective prioritization, and it's clear that it's time for a solution that offers both to keep pace with the increasing scale of human risk.
We believe the time for change is now, and User Risk is the platform we stand behind as the solution. It provides the engine needed to take that visible data, transform it into effective, automated governance, and finally secure your workforce from the noise of unprioritized risk.