Solving Human Risk: Build a Measurable, Security-First Culture
We've previously addressed the foundational problems of visibility and automated human risk management. However, the final, most enduring challenge remains: how do you address the human element that lies at the core of human cybersecurity risk?
Now more than ever, users are prime targets for attackers, but the traditional playbook offers little more than check-the-box training (which is often easily forgotten). Worse, it lacks holistic, continuous governance, making the management of users the core of your human risk surface tedious and difficult for security leaders to manage.
We believe effective safeguarding means providing employees with automated guidance and safer alternatives. It's time to empower users themselves and establish a resilient security culture that turns your workforce into your first line of defense.
Let's dive into our final installment and explore how User Risk achieves this by building a measurable, security-first culture.
Modern security culture: Built on a hollow framework
Regardless of how well you can detect and respond to human risk within your organization, you're only addressing the symptoms of the problem. The only way to safeguard your organization's overall security posture is to address the root cause of the problem: the users themselves.
The traditional playbook attempts to establish this through annual check-the-box training and Security Awareness Training (SAT), but they fail to build lasting security habits. The reason for this is that training consists of one-off events that do not directly address day-to-day scenarios, leading employees to quickly forget routines and view them merely as administrative tasks.
The result is clear: the traditional approach is flawed, leaving a significant gap between training and the day-to-day workflows of users. This inevitably leads to a weakened security culture on the macro scale (risky behaviors continue unchecked) and leaves users ill-equipped to handle the complex risk landscape on the micro scale (users aren't guided at the moment of risk).
The unseen cost of an ineffective security culture
As stated, the scope of the risk landscape is changing and expanding at an unprecedented rate. Employees have more access to external tools than ever before, with concerns rising about unauthorized software, especially the "long tail" of AI-enabled tools (such as meeting assistants) and apps that require users to sign in with workplace credentials.
Additionally, the use of Shadow AI within organizations is increasing. Our State of Shadow AI Report reveals that as employees interact with LLMs, more sensitive corporate data is being shared, leading to significantly higher, unmanaged risk. The result is that, with 40% of employees now using unapproved AI in their daily workflows, your users are becoming higher-risk targets with each passing day.
Download our State of Shadow AI Report here >
Security leaders need to stay on top of monitoring their various point-solution tools to make discoveries and manually enforce governance. Meanwhile, the very core of the risk they're managing—the users—remain unguided, at high risk, and prime targets for malicious actors due to a lack of true security culture.
This ultimately leads to negative consequences for both business operations and overall security posture that include, but aren't limited to:
- Strategic failure: Wasted resources are inevitable as security teams continue to spend valuable time on manual investigations and reactive monitoring due to sporadic user behavior.
- Persistent risk: Without sustained behavioral change, fundamental human risk vectors (phishing, misconfiguration, Shadow AI usage) remain, ensuring the organization is perpetually vulnerable.
We must move beyond mere visibility and governance action. While these are vital, they only address risk after it has been created. The real challenge is to address the root cause of human risk—the users in your organization—before or at the moment users perform risky actions. This shift begins by building an automated, robust, measurable, and security-first culture. User Risk is the path to achieving exactly that.
Building a security-first culture with User Risk
User Risk aims to fill the gap and move beyond the shortcomings of the traditional human security playbook by acting as the employee’s trusted security coach. The solution does this through three powerful core features: contextual nudges, personalized security insights, and automated validation.
Each of these three core features fills in the gaps left by modern security training. Instead of the one-sided enforcement of governance and policy, they offer continuous guidance toward safer habits and behaviour.
The approach these features take is to allow users to monitor and understand their own risk activity while also learning how to adopt and execute safer security practices, all in one swift process.
The features are also designed to provide leaders with the insight they need into user behavior. This helps your organization determine whether training is effective, identify users who are still at risk, and pinpoint those who are secure, effectively closing the loop in governance.
Let's break down each of these features and explore how User Risk takes your team from reactive firefighting and a hollow security culture to proactive governance and a security culture that is aware of, acts on, and mitigates risk all in real-time.
Real-time nudges that guide users
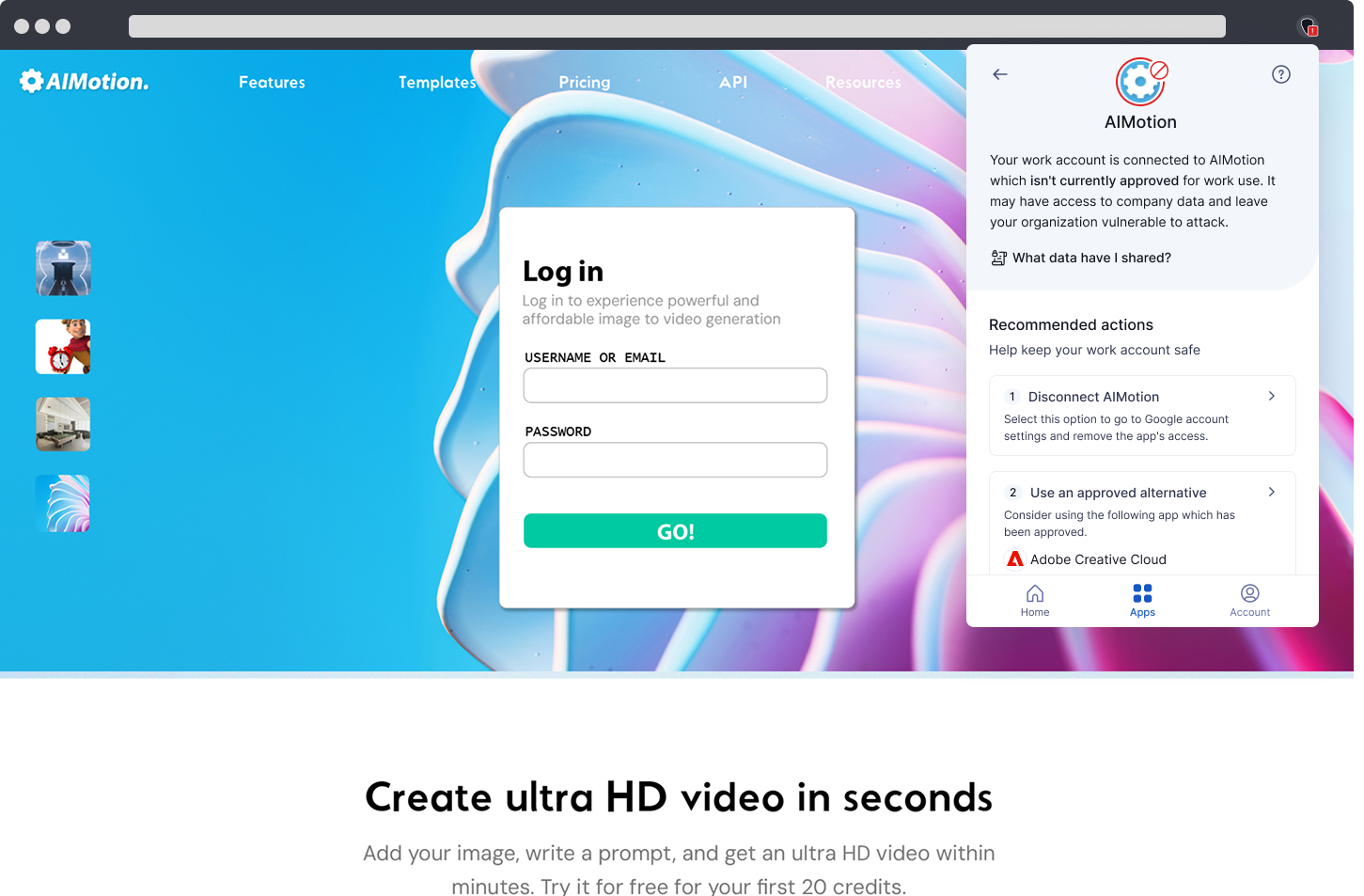
User Risk supplements check-the-box training by acting as the employee’s trusted security coach. This eliminates the struggles of non-continuous training, as it provides automated, educational "nudges" directly within the employee's workflow (browser) at the moment of risk, ensuring guidance is timely and non-punitive.
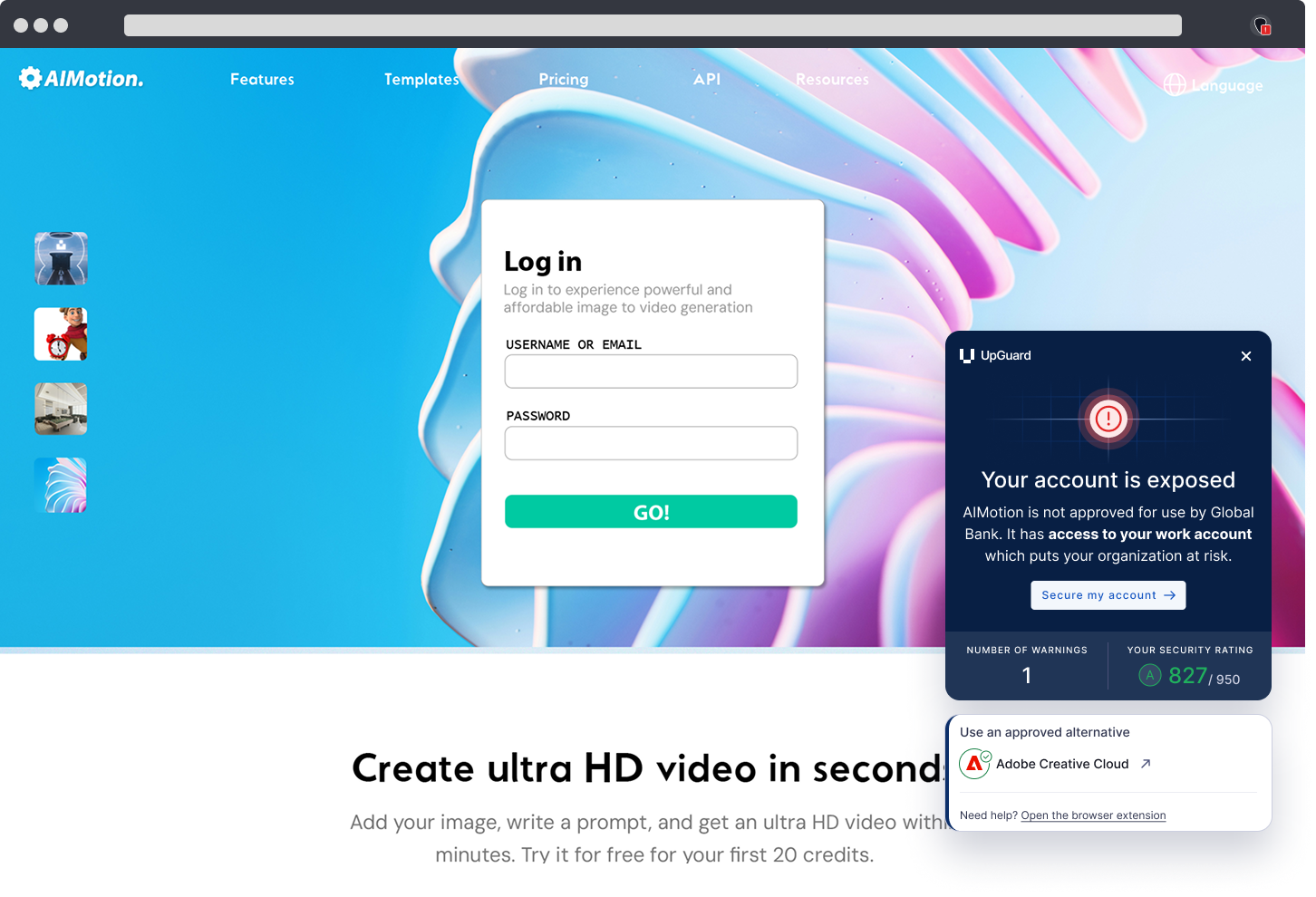
Unlike solutions that merely block risky behavior, User Risk provides helpful, real-time guidance. For example, when a user attempts to use an unapproved application, the nudge instantly redirects them to the approved corporate alternative or allows them to submit a formal application request—turning enforcement into an educational and workflow-friendly process.
Key benefits of real-time nudges:
- Continuous guidance: Delivers automated, educational guidance to employees at the actual moment of risk, ensuring training is relevant, actionable, and not forgotten—a massive improvement over episodic, annual training.
- Policy-driven enforcement: Your defined security policies directly power the real-time nudges, ensuring that your security standards are consistently coached and enforced at the exact moment a risky action occurs.
- Building secure habits: This intervention serves as an automated security coach, providing guidance that is relevant and timely to drive measurable security habits with minimal effort from your security team.
Our emphasis is always on empowering users with safe, approved options, ensuring that security is effective while also enhancing—not hindering—productivity.
Personalized security insights that inform and empower
Make security tangible for every employee. The User Risk solution provides each person with their own risk score and security insights, demonstrating the direct impact of their actions and motivating continuous improvement. This score acts as a natural guardrail to prevent future unsafe behaviors, as many employees strive to maintain a high score, giving them a clear security standard to work towards.
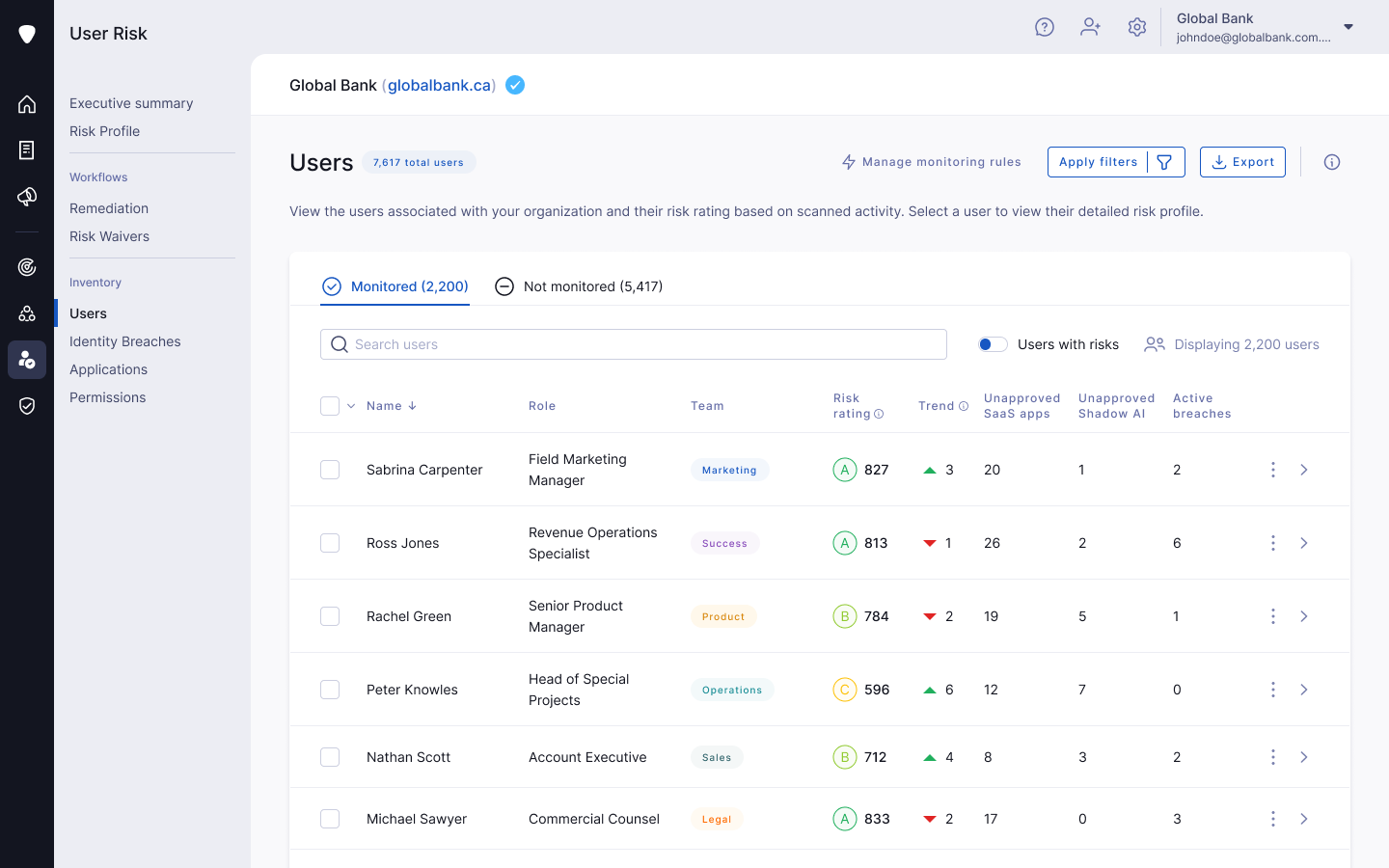
Key benefits of personalised security scores:
- Tangible security for all: Provides each employee with a personal risk score, making security tangible and demonstrating the direct impact of their actions.
- Actionable feedback: This score provides clear, actionable feedback, helping to motivate continuous improvement in the employee's security posture.
Automated validation and habit reinforcement
User Risk closes the gap between policy and action by focusing on validation, ensuring that new, secure habits actually stick. It provides security leaders with the crucial evidence that remediation efforts are effective, measuring the tangible success of behavior change. You don't just train your workforce; you continuously drive measurable risk reduction that is both measurable and reportable.
Key benefits of automated validation:
- Expedite validation: Utilizes daily scans to confirm or prompt users to ensure remedial actions have been taken and that risky behaviors have ceased.
- Closing the feedback loop: Provides a closed loop that verifies and reinforces lasting behavioral change, allowing leaders to definitively measure the program's success and report to higher-ups on the company's human risk status.
Solving human risk with visibility, action, and culture
Addressing modern human risk is an arduous task, and one that's only growing in complexity as time proceeds and users are exposed to more risk. While building a solid security culture is essential for addressing the core of human risk, it's still only one piece of the puzzle.
True human risk management requires a complete framework, and we’ve provided exactly that with User Risk. As we’ve explored in this series, our solution to addressing the human risk is to confront the core structural gaps in the modern human risk playbook and provide the tools leaders need to truly secure their workforce.
User Risk is the only solution that unifies discovery, automates governance, and drives lasting, measurable behavior change, solving legacy issues of visibility, prioritizing risk data to take action, and securing the human layer of your organization. This is our comprehensive framework for managing modern-day human risk.
So as we close out this series, we have a final thought for you to consider:
Is your human risk data visible? Can you act on it effectively? And do your users have the effective guidance and guardrails in place to keep your human layer secure?