Salesforce Extortion Accelerates With New Leak Site
For months now, journalists and cybersecurity experts, including UpGuard, have been following the movements of the hacker collective “Scattered Lapsus$ Hunters,” a sort of supergroup of the already well-known cybercriminal entities ShinyHunters, Scattered Spider and Lapsus$. Now, this collective has launched a website where they can extort payment from entities in return for delisting and deleting their data. The collective has specifically been targeting Salesforce data as valuable extortion leverage.
The scope and organization of this operation represents the next step in cybercrime, hinting at the potential ramifications of the group’s previously stated aim of offering ransomware-as-a-service. But if we trace it back to the beginning, we can see that even sophisticated attacks like this begin with simple and typical digital inroads.
Timeline of Events
Late 2024
- Attackers using social engineering, particularly over the phone (“vishing” for voice phishing), gain access to widespread corporate Salesforce data. They accomplish this by tricking someone with access into adding a fraudulent integration into their Salesforce system. Once this integration was added, the attackers had API level access to the target Salesforce system and were able to exfiltrate data. This affected many large companies, including Google and Cisco.
March 2025 - June 2025
- Attackers gain access to Salesloft’s corporate Github account. Salesloft is a sales engagement platform with an AI chatbot called “Drift” that integrates with Salesforce and other applications. Using this Github account, they download content from multiple repositories, create their own user in the organization and set up custom workflows. It appears that during this time the attackers also reconnoitered Salesloft’s application environment, but Salesloft claims no other actions were taken there.
- The attackers access Salesloft Drift’s AWS environment, presumably using credentials found in the compromised Github repository.
- Within the AWS environment, attackers discover the OAuth tokens of Salesloft Drift clients.
June 2025
- Google publishes an article detailing how these attackers use social engineering phone calls, in which they impersonate IT support or other authorized users, to gain access specifically to Salesforce related data by way of malicious integrations. It may have been through such a social engineering attempt, or the data gained from a successful one, that the initial Github credentials for Salesloft were compromised.
August 8-18 2025
- Using the valid OAuth integration tokens from Salesloft Drift, the attackers access and exfiltrate data from the integrated platforms, such as Salesforce. At first, Salesloft claims that only Salesforce integrations are affected, but it is quickly revealed that “Salesloft Drift customers were compromised en masse, potentially snagging any user that integrated the AI chat agent platform to another third-party service,” according to Google’s August 26th report.
August 20th 2025
- Salesloft discloses the breach.
August 26th 2025
- Google releases detailed information about the Salesloft attack and its consequences.
September 7th 2025
- Salesloft Drift goes back online.
September 17th 2025
- Hacker collective Scattered Lapsus$ Hunters claims to be “going dark” and that operations will cease. Continued activity, especially around Salesforce related data, is noted by many cybersecurity experts.
October 3rd 2025
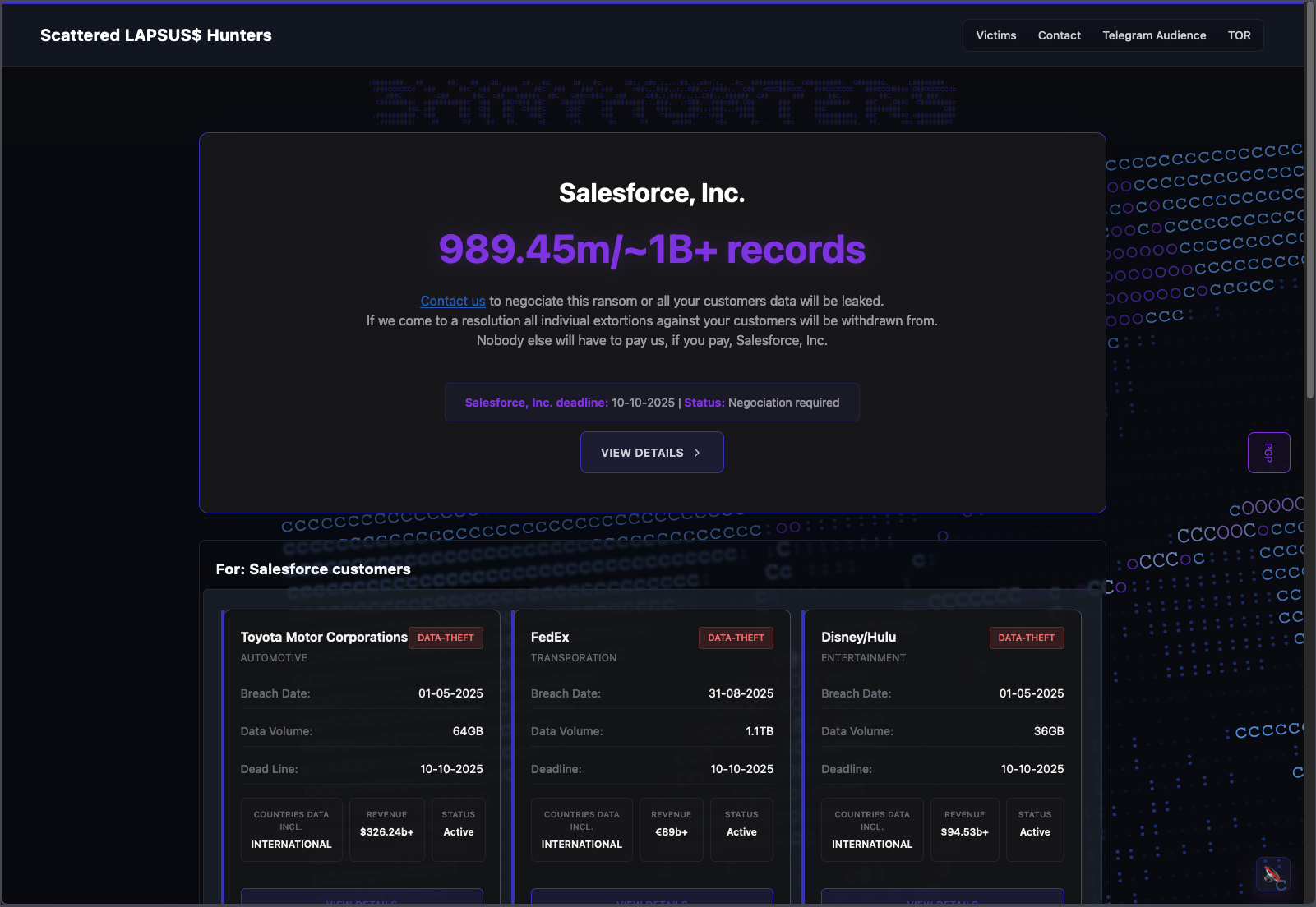
- Scattered Lapsus$ Hunters launches their “extortionware” portal, threatening Salesforce and those organizations compromised by social engineering or in the Salesloft Drift breach with exposure of their data should payment not be made. A deadline is posted of October 10th.
Extortionware Portal
Most news organizations are, understandably, not linking directly to the attackers’ website, though links can be found on social media. The site operates on the TOR Onion network, although claims of an additional clear web version have been made. The website lists affected Salesforce customers, along with how much of their data the group claims to have exfiltrated during the attacks.
Ramifications
This incident can seem overwhelming, but the root causes are both known and preventable. User risk, especially that of social engineering, continues to be the most common cause of data exposures. Accounting for and addressing user risk is crucial to operational security. We don’t know for sure how attackers compromised Salesloft’s Github account, but we do know that in doing so, they gained access to a vast amount of data, including further credentials that let them into other systems. Github sanitation has long been known as a key factor in preventing data exposure. Usually such breaches happen when a repository is made public, but even in a private repository, care should be taken to limit or completely remove embedded credentials that could be used for further access.
Salesforce data is valuable leverage for a malicious actor because it contains the crucial business components that generate revenue, such as customer and lead data, deal details, and other confidential information that can financially and reputationally damage a company and their customers if it becomes public. One of Salesforce’s greatest functional strengths is the ability to integrate with almost anything, a flexibility that allows companies in different industries and of different scales to tailor it to their specific needs. However, acting as a platform into which many third-parties can be integrated also creates a large attack surface and a substantial increase in risk.
In the first method of obtaining data, the attackers used social engineering to trick people into allowing malicious Salesforce integrations. In the second method, they were able to compromise a large legitimate Salesforce integration itself and use that integration’s OAuth keys to exfiltrate Salesforce data from its users. In both cases, the ability for integrations to read the full Salesforce dataset led to the compromise of that data.
In an official response, Salesforce has stated that “At this time, there is no indication that the Salesforce platform has been compromised, nor is this activity related to any known vulnerability in our technology.” This is technically true. It is also true that the Salesforce platform has been the single largest source of stolen data this year.